Configuring Custom Domain Name
Last updated:2026-01-30 14:59:41
Users can use a custom domain name to connect to the TDMQ for MQTT cluster. This method has several advantages:
When MQTT access points are provided to customers, maintain brand consistency for users.
Migrate the backend cluster by reparsing DNS, keeping the access point unchanged.
Reuse existing corporate PKI facilities.
Configure instance use with a custom domain name includes the following steps:
1. Upload a server certificate to SSL Certificate Service.
2. Configure server certificate pairs and trust certificates for the MQTT instance.
3. Create a DNS record.
Uploading Certificate Pairs and Trust Certificates to SSL Certificate Service
To ensure normal certificate rotation and expiration reminder, unaffected business continuity, MQTT instances can only be configured with SSL Certificate Service managed certificates.
Certificate Requirements
1. The server certificate (End Entity Certificate) must contain the X.509 v3 Extended Key Usage extension, which must include serverAuth (TLS Web Server Authentication). Refer to RFC 5280. The certificate should include the necessary Subject Alternative Name (SAN) extension and Common Name (CN). If your certificate is issued by a CA, it normally contains this extension.
Note:
If a certificate contains both CN and SAN, when a certificate is selected via TLS Server Name Indication (SNI), priority is given to domain names listed in the SAN extension; if SAN is absent, it falls back to using CN for selection.
Major browsers have deprecated CN matching, for example, Chrome 58+ ignores CN. When using Web Secure Socket as the MQTT transport layer, ensure the SAN extension and Server Auth value are properly configured.
2. The certificate chain can contain up to 5 certs.
3. The certificate chain file is no more than 16KiB.
Certificate Upload, Managed, Purchase
Configuring Certificates and Trust Certificates for the MQTT Instance
MQTT Console > Cluster Page, switch to Authentication Management/X.509 Certificate Management Page:
Choose the appropriate authentication mode based on whether client certificate verification is required.
One-way authentication: no verification of client certificate
Mutual authentication: validate client certificate
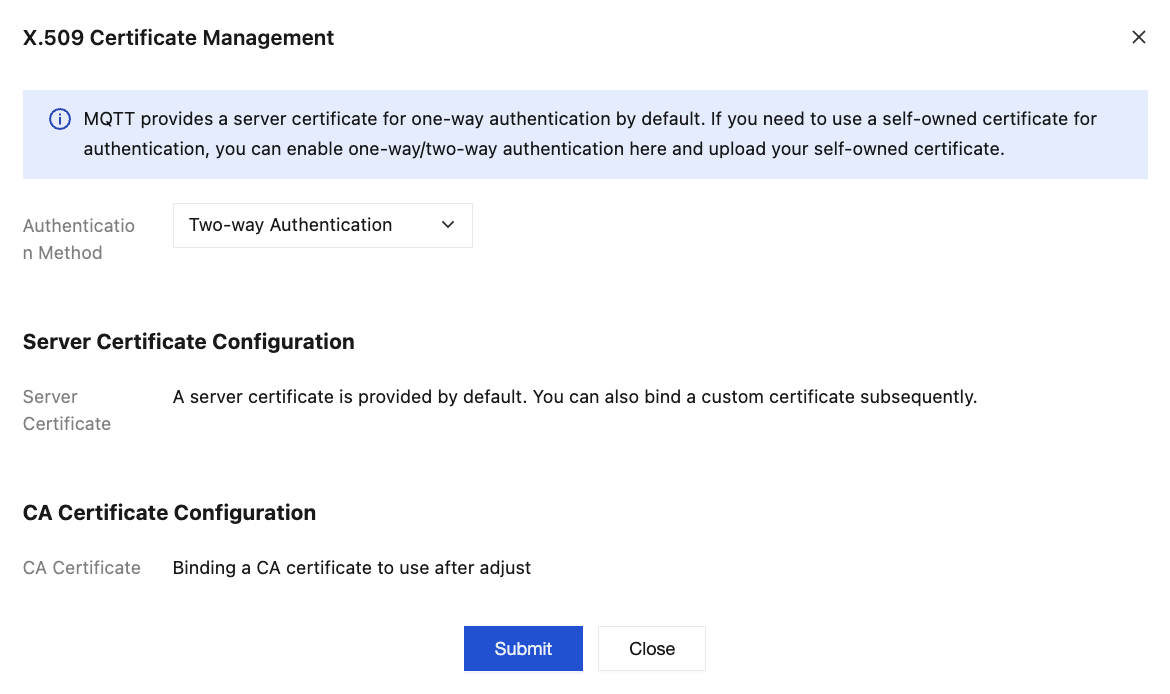
Assuming the selected server certificate Subject Alternative Name includes the following domain name:
mqtt-abc.compay.com.Creating DNS Record
Refer to Cloud Resolution - CNAME Record, create a CNAME record to resolve
mqtt-abc.compay.com to the domain name provided by the access point of the instance: mqtt-xxx-sh-public.mqtt.tencenttdmq.com.
Subsequently access via
mqtt-abc.company.com.Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

