C SDK
Last updated:2026-01-30 15:02:25
C SDK
Last updated: 2026-01-30 15:02:25
Feature Overview
Eclipse Paho C and Eclipse Paho Embedded C are C language client libraries (MQTT C Client) under the Eclipse Paho project. All are full-featured MQTT Clients written in ANSI C.
Eclipse Paho Embedded C can be used on desktop operating systems, but is mainly for embedded environments such as Mbed, Arduino and FreeRTOS.
The client provides two API types, synchronous and async, starting with MQTTClient and MQTTAsync respectively:
Synchronous APIs aim to be easier and more useful. Specific calls will block until the operation completes, making programming simpler.
The async API contains only one blocking call, API-waitForCompletion, which performs result notification via callback and is more suitable for non-main thread environments.
Cloud Resource Preparation
Environment Preparation
Note:
Paho MQTT C SDK requires CMake version 3.5+.
Installing the Paho Mqtt C SDK Example
cd paho.mqtt.c && cmake .make && make installecho '/usr/local/lib64' > /etc/ld.so.conf.d/paho.confecho '/usr/local/lib' >> /etc/ld.so.conf.d/paho.confldconfig
Example Code
Copy to
/root/mqtt-example.c#include "stdio.h"#include "stdlib.h"#include "string.h"#include "MQTTClient.h"#define ADDRESS "tcp://mqtt-********.mqtt.tencenttdmq.com:1883"#define CLIENTID "sample_client"#define TOPIC "testtopic/1"#define PAYLOAD "Hello World!"#define QOS 1#define TIMEOUT 10000L#define USERNAME "your-username"#define PASSWORD "your-password"int main(int argc, char* argv[]){MQTTClient client;MQTTClient_connectOptions conn_opts = MQTTClient_connectOptions_initializer;MQTTClient_message pubmsg = MQTTClient_message_initializer;MQTTClient_deliveryToken token;int rc;MQTTClient_create(&client, ADDRESS, CLIENTID,MQTTCLIENT_PERSISTENCE_NONE, NULL);// MQTT connection parametersconn_opts.keepAliveInterval = 20;conn_opts.cleansession = 1;conn_opts.MQTTVersion = MQTTVERSION_3_1_1;conn_opts.username = USERNAME;conn_opts.password = PASSWORD;if ((rc = MQTTClient_connect(client, &conn_opts)) != MQTTCLIENT_SUCCESS){printf("Failed to connect, return code %d\\n", rc);exit(-1);}// Publish a messagepubmsg.payload = PAYLOAD;pubmsg.payloadlen = strlen(PAYLOAD);pubmsg.qos = QOS;pubmsg.retained = 0;MQTTClient_publishMessage(client, TOPIC, &pubmsg, &token);printf("Waiting for up to %d seconds for publication of %s\\n""on topic %s for client with ClientID: %s\\n",(int)(TIMEOUT/1000), PAYLOAD, TOPIC, CLIENTID);rc = MQTTClient_waitForCompletion(client, token, TIMEOUT);printf("Message with delivery token %d delivered\\n", token);disconnectMQTTClient_disconnect(client, 10000);MQTTClient_destroy(&client);return rc;}
Parameter Description
Parameter | Description |
ADDRESS | broker connection address can be copied from the Basic Information > Access Information section of the target cluster in the console, as shown below. Format: mqtt-xxx-gz.mqtt.qcloud.tencenttdmq.com:1883. 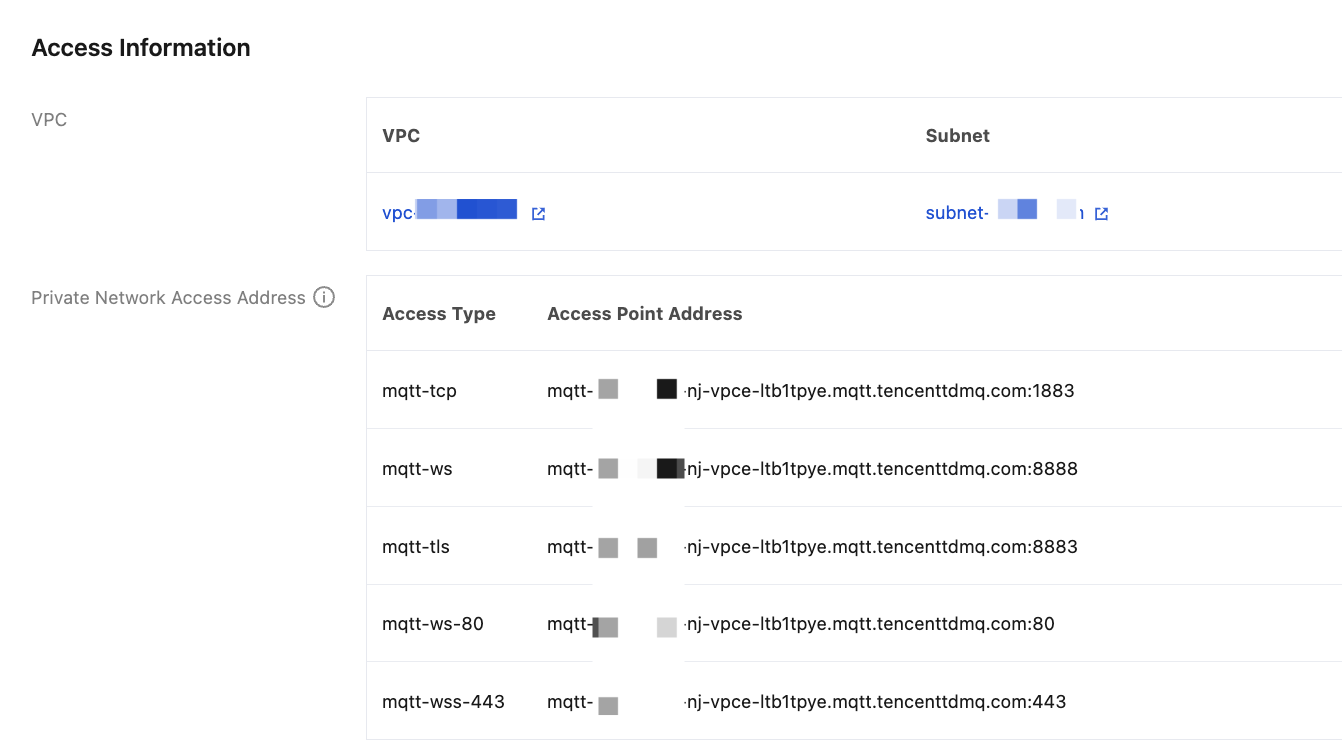 |
CLIENTID | Client ID is obtained from the Client Management page in the cluster details page on the console. |
USERNAME | User name can be obtained on the Authentication Management page in the console. |
PASSWORD | Password can be obtained on the Authentication Management page in the console. |
Compilation Example
cd /rootgcc mqtt-example.c -lpaho-mqtt3c -o mqtt-example
Paho C MQTT 5.0 Support
Paho C currently has complete support for MQTT 5.0.
One Device One Certificate Example
Scenario Introduction
For high-value devices in scenarios with high security requirements, recommend using the "One Device One Certificate" approach for client authentication. "One Device One Certificate" strengthens mutual authentication (mTLS): on the basis of mutual authentication, the cloud manages the state of client certificates, including activating, deactivating, and revoking operations.
Generating a Certificate
Generating a CA Certificate
openssl ecparam -genkey -name prime256v1 -out CA.keyopenssl req -new -x509 -key CA.key -sha256 -subj "/C=CN/ST=ZheJiang/L=HangZhou/O=TencentCloud/CN=MQTT-CA" -days 3650 -out CA.crt
openssl genrsa -out CA.key 4096openssl req -new -x509 -key CA.key -sha256 -subj "/C=CN/ST=ZheJiang/L=HangZhou/O=TencentCloud/CN=MQTT-CA" -days 3650 -out CA.crt
Issuing a Server Certificate
create configuration file server.conf
[req]distinguished_name = req_distinguished_namereq_extensions = v3_reqprompt = no[req_distinguished_name]C = CNST = ZheJiangL = HangZhouO = ExampleCN = mqtt.example.com[v3_req]basicConstraints = critical, CA:FALSE# Common Key Usage Combinations# TLS Server: keyUsage=digitalSignature,keyEncipherment + extendedKeyUsage=serverAuth# TLS Client: keyUsage=digitalSignature + extendedKeyUsage=clientAuth# Code Signing: keyUsage=digitalSignature + extendedKeyUsage=codeSigningkeyUsage = critical, digitalSignature, keyEnciphermentextendedKeyUsage = serverAuthsubjectAltName = @alt_names[alt_names]DNS.1 = mqtt.example.comDNS.2 = www.example.comDNS.3 = api.example.comDNS.4 = *.example.comIP.1 = 192.168.1.100IP.2 = 10.0.0.50
openssl ecparam -genkey -name prime256v1 -out server.keyopenssl req -new -key server.key -out server.csr -config server.confopenssl x509 -req -in server.csr -CA CA.crt -CAkey CA.key -CAcreateserial -out server.crt -days 365 -sha256 -extensions v3_req -extfile server.conf
openssl genrsa -out server.key 4096openssl req -new -key server.key -out server.csr -config server.confopenssl x509 -req -in server.csr -CA CA.crt -CAkey CA.key -CAcreateserial -out server.crt -days 365 -sha256 -extensions v3_req -extfile server.conf
Verifying Server Certificate
openssl x509 -in server.crt -text -nooutopenssl verify -CAfile CA.crt server.crtopenssl x509 -in server.crt -text -noout | grep -A 10 "Subject Alternative Name"
Creating a complete server certificate chain file
cat server.crt > server.chain.crtcat CA.crt >> server.chain.crt
Issuing a Client Certificate
create configuration file client.conf.
[v3_req]basicConstraints = critical, CA:FALSEkeyUsage = critical, digitalSignatureextendedKeyUsage = clientAuth
openssl ecparam -genkey -name prime256v1 -out client.keyopenssl req -new -key client.key -out client.csr -subj "/C=CN/ST=ZheJiang/L=HangZhou/O=IoV/CN=SN0001"openssl x509 -req -in client.csr -CA CA.crt -CAkey CA.key -CAcreateserial -out client.crt -days 365 -sha256 -extfile client.conf -extensions v3_req
openssl genrsa -out client.key 4096openssl req -new -key client.key -out client.csr -subj "/C=CN/ST=ZheJiang/L=HangZhou/O=IoV/CN=SN0001"openssl x509 -req -in client.csr -CA CA.crt -CAkey CA.key -CAcreateserial -out client.crt -days 365 -sha256 -extfile client.conf -extensions v3_req
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback
