安全组概述
最后更新时间:2024-01-24 18:13:16
安全组是一种虚拟防火墙,具备有状态的数据包过滤功能,用于设置云服务器、负载均衡、云数据库等实例的网络访问控制,控制实例级别的出入流量,是重要的网络安全隔离手段。
您可以通过配置安全组规则,允许或禁止安全组内的实例的出流量和入流量。
特点
安全组是一个逻辑上的分组,您可以将同一地域内具有相同网络安全隔离需求的云服务器、弹性网卡、云数据库等实例加到同一个安全组内。
安全组未添加任何规则时,默认拒绝所有流量,您需要添加相应的允许规则。
安全组是有状态的,对于您已允许的入站流量,都将自动允许其流出,反之亦然。
您可以随时修改安全组的规则,新规则立即生效。
使用限制
安全组规则
组成部分
安全组规则包括如下组成部分:
来源或目标:流量的源(入站规则) 或目标(出站规则),可以是单个 IP 地址、IP 地址段,也可以是安全组,具体请参见 安全组规则。
协议类型和协议端口:协议类型如 TCP、UDP 等。
策略:允许或拒绝。
规则优先级
安全组内规则具有优先级。规则优先级通过规则在列表中的位置来表示,列表顶端规则优先级最高,最先应用;列表底端规则优先级最低。
若有规则冲突,则默认应用位置更前的规则。
当有流量入/出绑定某安全组的实例时,将从安全组规则列表顶端的规则开始逐条匹配至最后一条。如果匹配某一条规则成功,允许通过,则不再匹配该规则之后的规则。
多个安全组
一个实例可以绑定一个或多个安全组,当实例绑定多个安全组时,多个安全组将按照从上到下依次匹配执行,您可以随时调整安全组的优先级。
安全组模板
新建安全组时,您可以选择腾讯云为您提供的两种安全组模板:
放通全部端口模板:将会放通所有出入站流量。
放通常用端口模板:将会放通 TCP 22端口(Linux SSH 登录),80、443端口(Web 服务),3389端口(Windows 远程登录)、 ICMP 协议(Ping)、放通内网(私有网络网段)。
说明:
如果您对应用层(HTTP/HTTPS)有安全防护需求,可另行购买 腾讯云 Web 应用防火墙(WAF),WAF 将为您提供应用层 Web 安全防护,抵御 Web 漏洞攻击、恶意爬虫和 CC 攻击等行为,保护网站和 Web 应用安全。
使用流程
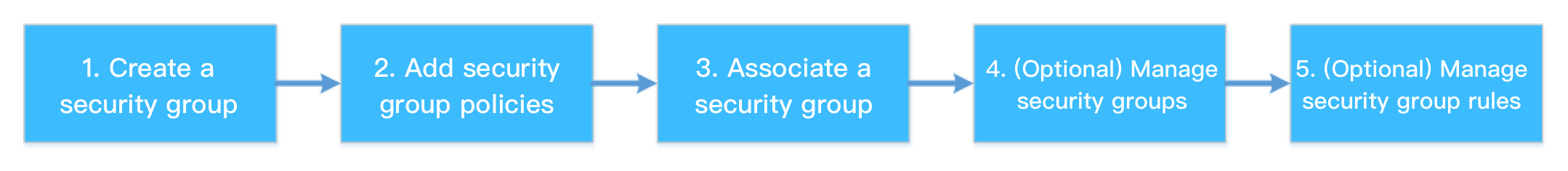
安全组的使用流程如下图所示:

安全组实践建议
创建安全组
调用 API 购买 CVM 时建议指定安全组,未指定安全组时,将使用系统自动生成的默认安全组,默认安全组不可删除,默认规则为放通所有 IPv4 规则,创建后可按需修改。
实例防护策略有变更,建议优先修改安全组内规则,不需要重新新建一个安全组。
管理规则
需要修改规则时可以先将当前安全组导出备份,如果新规则有不利影响,可以导入之前的安全组规则进行恢复。
当所需规则条目较多时可以使用 参数模板。
关联安全组
您可以将有相同防护需求的实例加入一个安全组,而无需为每一个实例都配置一个单独的安全组。
不建议一个实例绑定过多安全组,不同安全组规则的冲突可能导致网络不通。
安全组和云防火墙
腾讯云防火墙(Cloud Firewall,CFW),是腾讯云原生的 SaaS 化防火墙产品,并集成了攻击者视角的漏洞扫描能力、IPS 入侵拦截能力、全网威胁情报和高级威胁溯源分析能力,是云环境的流量安全中心和策略管控中心,业务上云的第一道安全门户。
在实际使用场景中,安全组一般部署在 CVM 等云产品边界,用于实现云产品所属安全组间的访问控制。而腾讯云防火墙部署在 VPC 间的边界或互联网边界,用于实现 VPC 间或腾讯云到互联网访问控制。具体如下图所示:
在如下场景中,使用安全组不能满足需求,可采用 腾讯云防火墙 来实现访问控制:
1. 了解 CVM 资产在互联网的暴露及漏洞情况,并通过 IPS 入侵防御功能和虚拟补丁功能,对网络漏洞加强防护。
2. 按域名实现主动外联控制,加强业务的安全性。
3. 按区域实现访问控制,例如,一键禁封境外 IP 的访问。
文档反馈

