- Updates and Announcements
- Product Introduction
- New/Legacy Anti-DDoS Advanced Version Differences
- Comparison of Anti-DDoS Protection Schemes
- Purchase Guide
- Getting Started
- Operation Guide
- Best Practice
- API Documentation
- FAQs
- Troubleshooting
- Anti-DDoS Advanced (Global Enterprise Edition)
- Legacy Anti-DDoS Advanced (Legacy)
- Service Level Agreement
- Contact Us
- Glossary
- Updates and Announcements
- Product Introduction
- New/Legacy Anti-DDoS Advanced Version Differences
- Comparison of Anti-DDoS Protection Schemes
- Purchase Guide
- Getting Started
- Operation Guide
- Best Practice
- API Documentation
- FAQs
- Troubleshooting
- Anti-DDoS Advanced (Global Enterprise Edition)
- Legacy Anti-DDoS Advanced (Legacy)
- Service Level Agreement
- Contact Us
- Glossary
Configuration Directions and Notes on CC Protection Policy
Last updated: 2022-08-16 15:28:12
Anti-DDoS Advanced provides CC attack protection, the protection policy features protection level, cleansing threshold, precise protection, and CC frequency limit, etc. After connecting your business, you can configure CC attack protection policy as instructed in this document to use Anti-DDoS Advanced to safeguard your business.
Directions
- Log in to the Anti-DDoS console and select Anti-DDoS Advanced (New) > Configurations on the left sidebar. Open the CC Protection tab.
- Select a domain name under an instance ID from the left list, e.g., 212.64.xx.xx bgpip-000002je -> http:80 -> www.xxx.com.
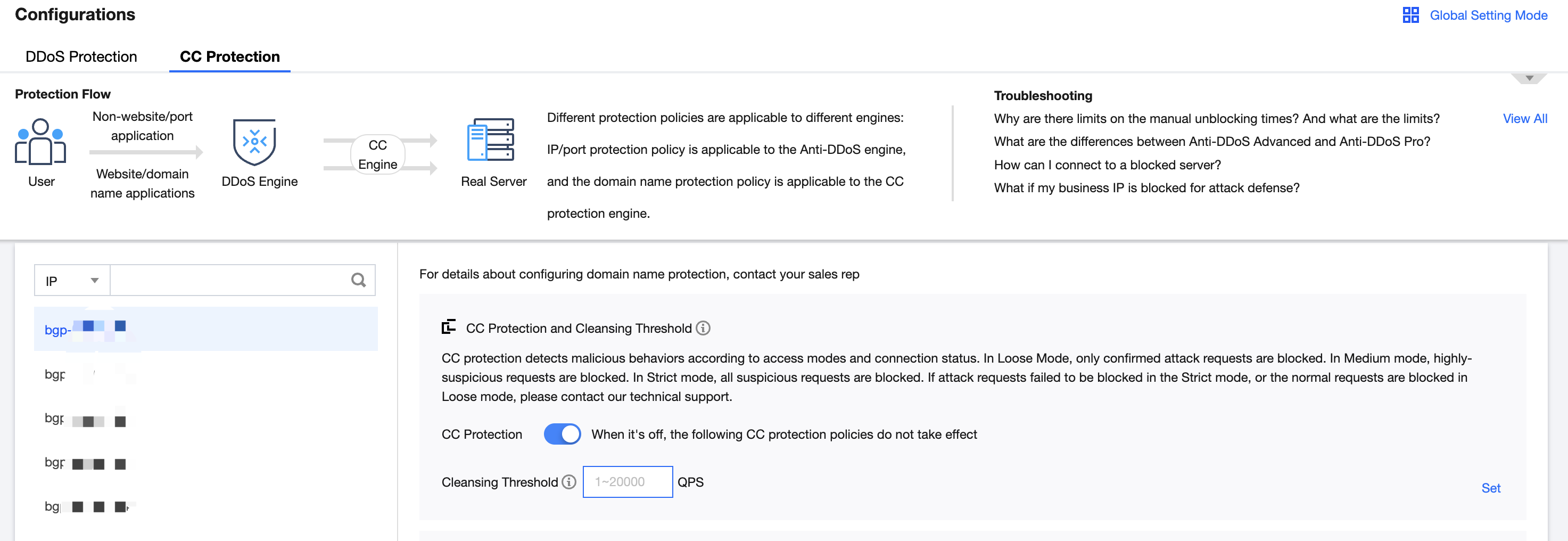
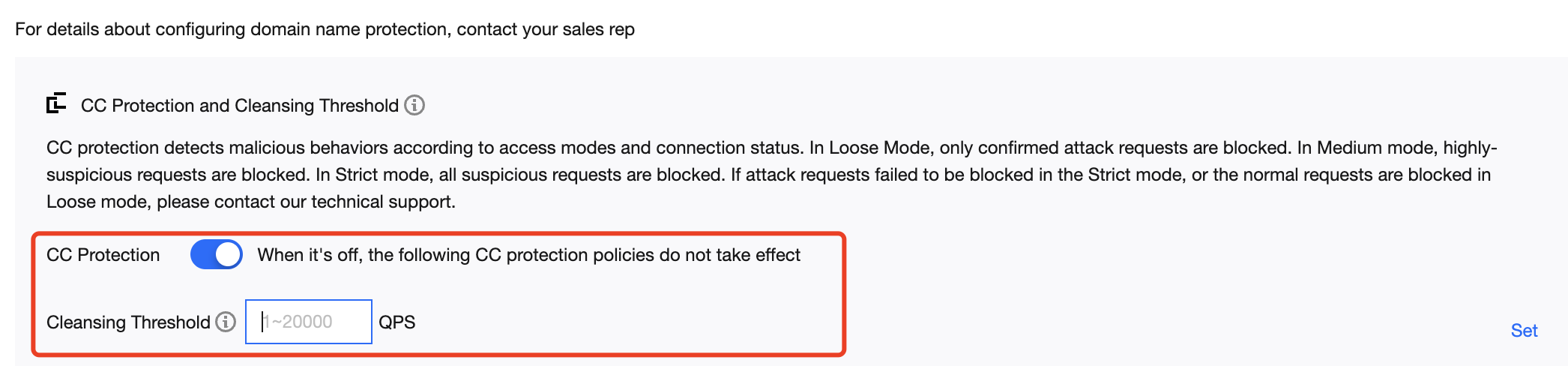
- Toggle on the switch
 in the CC Protection and Cleansing Threshold card. Then set a cleansing threshold.
Note:
in the CC Protection and Cleansing Threshold card. Then set a cleansing threshold.
Note:- The Anti-DDoS Advanced CC protection will be enabled once you set a cleansing threshold. A value that 1.5 times your common business peak is recommended.
- The Anti-DDoS Advanced cleansing feature will remain disabled if no threshold value is set, and the protection level, precise protection, and CC frequency limit you configured in the console will not be in effect even when your business is under CC attacks. For more information, please see CC Protection and Cleansing Threshold.
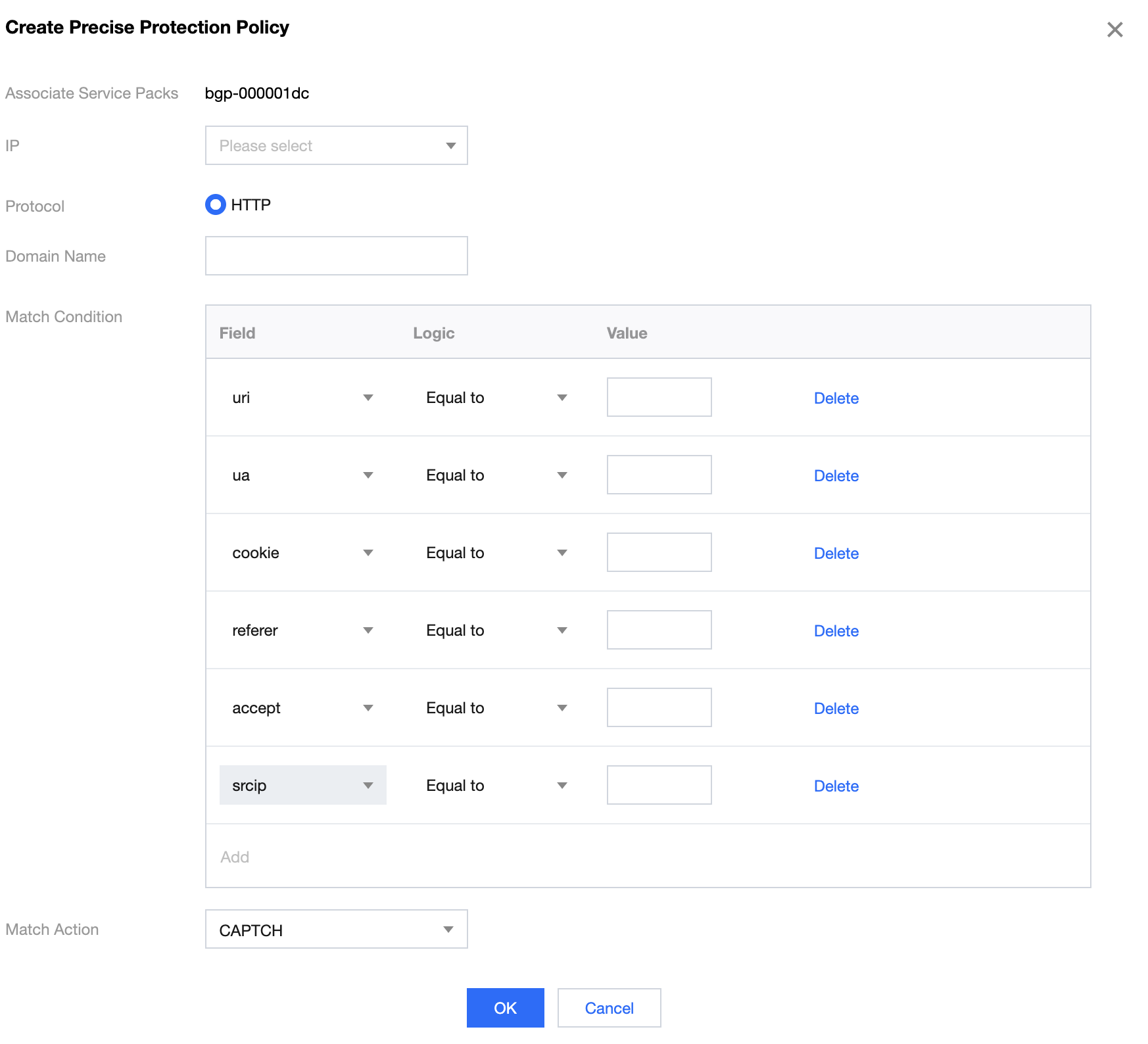
5. Configure the precise protection policy:
When your business is under attack, we recommend deriving the attack characteristics from the specific attack request information obtained through packet capture, middleware access logs, and other protection devices to configure your precise protection policy based on your business.
You can enable precise protection to configure protection policies combining multiple conditions of common HTTP fields, such as URI, UA, Cookie, Referer, and Accept to screen access requests. For the requests that match the conditions, you can configure CAPTCHA to verify requesters or a policy to automatically discard the packets.
- On the CC Protection page, click Set in the Precise Protection section to view the precise protection rule list.
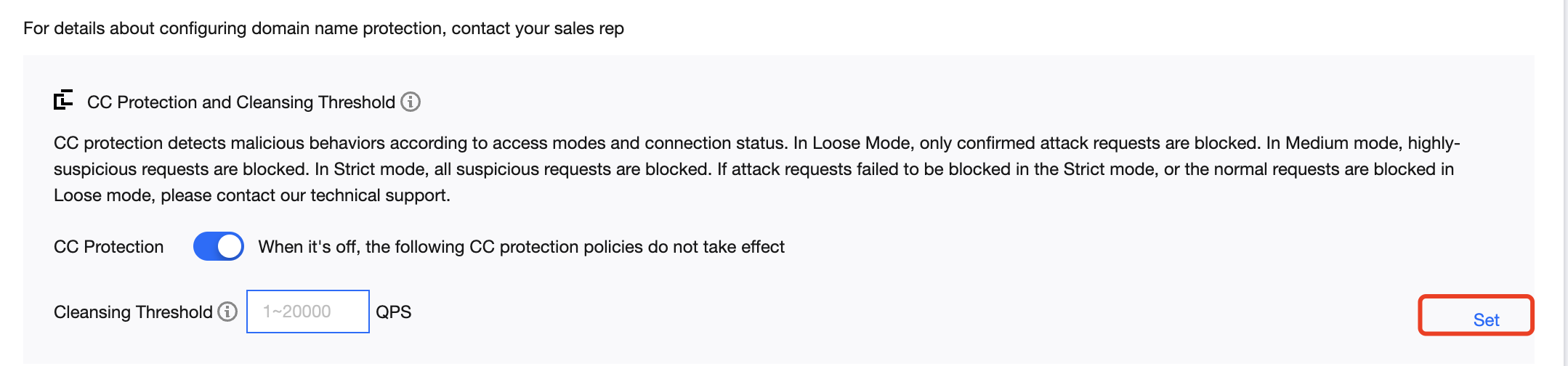
- Click Create. On the pop-up page, enter the required fields, and click OK. For more information, please see Precise Protection.
Note:
- If a policy involves multiple HTTP fields, the policy can be matched if all conditions are met.
- Anti-DDoS Advanced supports configuring precise protection for HTTPS businesses.
Field description:
| Field | Field Description |
|---|---|
| URI | The URI of an access request. |
| UA | The identifier and other information of the client browser that initiates an access request. |
| cookie | The cookie information in an access request. |
| Referer | The source website of an access request, from which the access request is redirected. |
| Accept | The data type to be received by the client that initiates the access request. |
| Match condition | CAPTCHA and discard
|
- Set the CC frequency limit:
Anti-DDoS Advanced supports configuring CC frequency policy for connected web businesses to restrict the access frequency of source IPs. You can customize a frequency policy to apply CAPTCHA and discard on source IPs if any IP accesses a certain page too frequently in a short time. - On the CC Protection page, click Set in the CC Frequency Limit section to view the frequency limit rule list.
- Click Create. On the pop-up page, enter the required fields, and click OK. For detailed configurations, please see CC Frequency Limiting.
Note:
- When configuring a CC frequency limit policy targeting the URI field, you need to configure a frequency limit on the directory
/first and the match mode must be "equals to". Then you can configure the URI access frequency limit on other directories. - If a source IP accesses the
/directory of the domain name for more than the set number of times in the set period, the set action (CAPTCHA or Discard) will be triggered. - If a frequency limit policy is configured for the
/directory of a domain name, then the frequency of the domain name's other directories must be the same. - If the request URI contains any unfixed string, you can set the match mode to "include", so that URIs with the set prefix will be matched.
- When configuring a CC frequency limit policy targeting the URI field, you need to configure a frequency limit on the directory

Field description:
| Field | Field Description |
|---|---|
| Cookie | The cookie information in an access request. |
| User-Agent | The identifier and other information of the client browser that initiates an access request. |
| URI | The URI of an access request. |
| Frequency limit policy | CAPTCHA and discard
|
| Check condition | Set the access frequency based on your business, for which a value 2 to 3 times the common number of access requests is recommended. For example, if your website is accessed averagely 20 times per minute, you can configure the value to 40 to 60 times per minute or adjust it according to the attack severity. |
| Blocking time | The longest period is a whole day. |

 Yes
Yes
 No
No
Was this page helpful?