- Updates and Announcements
- Product Introduction
- New/Legacy Anti-DDoS Advanced Version Differences
- Comparison of Anti-DDoS Protection Schemes
- Purchase Guide
- Getting Started
- Operation Guide
- Best Practice
- API Documentation
- FAQs
- Troubleshooting
- Anti-DDoS Advanced (Global Enterprise Edition)
- Legacy Anti-DDoS Advanced (Legacy)
- Service Level Agreement
- Contact Us
- Glossary
- Updates and Announcements
- Product Introduction
- New/Legacy Anti-DDoS Advanced Version Differences
- Comparison of Anti-DDoS Protection Schemes
- Purchase Guide
- Getting Started
- Operation Guide
- Best Practice
- API Documentation
- FAQs
- Troubleshooting
- Anti-DDoS Advanced (Global Enterprise Edition)
- Legacy Anti-DDoS Advanced (Legacy)
- Service Level Agreement
- Contact Us
- Glossary
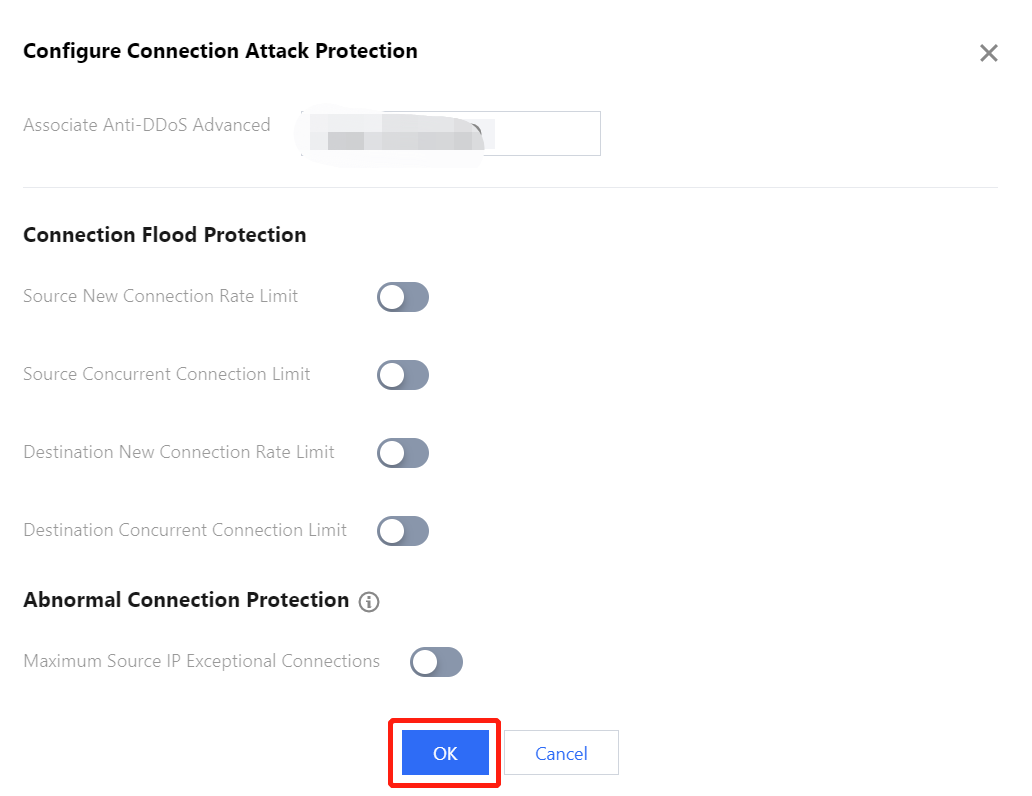
Anti-DDoS Advanced (Global Enterprise Edition) can automatically trigger blocking policies facing abnormal connections. With Maximum Source IP Exceptional Connections enabled, a source IP that frequently sends a large number of messages about abnormal connection status will be detected and added to the blocklist. The source IP will be accessible after being blocked for 15 minutes. You can set the following configurations as needed:
Note:
- Source New Connection Rate Limit: limits the rate of new connections from source ports.
- Source Concurrent Connection Limit: limits the number of active TCP connections from source addresses at any one time.
- Destination New Connection Rate Limit: limits the rate of new connections from destination IP addresses and destination ports.
- Destination Concurrent Connection Limit: limits the number of active TCP connections from destination IP addresses at any one time.
- Maximum Source IP Exceptional Connections: limits the maximum number of abnormal connections from source IP addresses.
Prerequisite
You have purchased an Anti-DDoS Advanced (Global Enterprise Edition) instance and set the object to protect.
Directions
- Log in to the Anti-DDoS Advanced (Global Enterprise Edition) console and select Anti-DDoS Advanced > Configurations > DDoS Protection.
- Select an Anti-DDoS Advanced instance ID in the list on the left, such as "xxx.xx.xx.xx bgpip-000003n2".
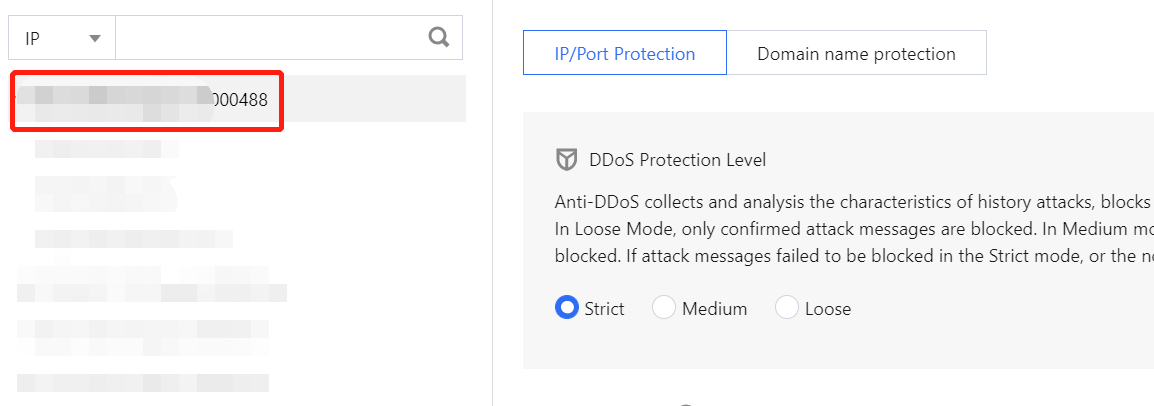
- Click Set in the Connection Attack Protection section.
- Click Create. On the pop-up page, configure the protection settings and click OK.
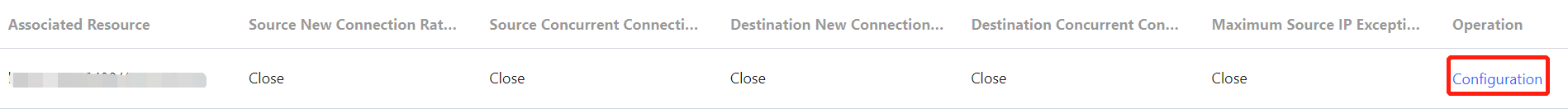
- After the rule is created, it is added to the list. You can click Configuration on the right of the rule to modify it.

 Yes
Yes
 No
No
Was this page helpful?