Tencent Cloud Key Management Service (KMS) is a security management solution that lets you to easily create and manage keys and protect their confidentiality, integrity, and availability, helping meet your key management and compliance needs in multi-application and multi-business scenarios.
Key Management Service
A secure, easy-to-use key management service for encrypted data

KMS leverages a third-party certified hardware security module (HSM) to generate and protect keys, and utilizes secure data transfer protocols, distributed clustered service deployment and hot backup for guaranteed availability. The security and quality control practices adopted by KMS are accredited by multiple compliance schemes.

The Key Management Service provides you with rich management features, including key creation, enabling, disabling, rotation settings, alias settings, viewing key details, and modifying related information.

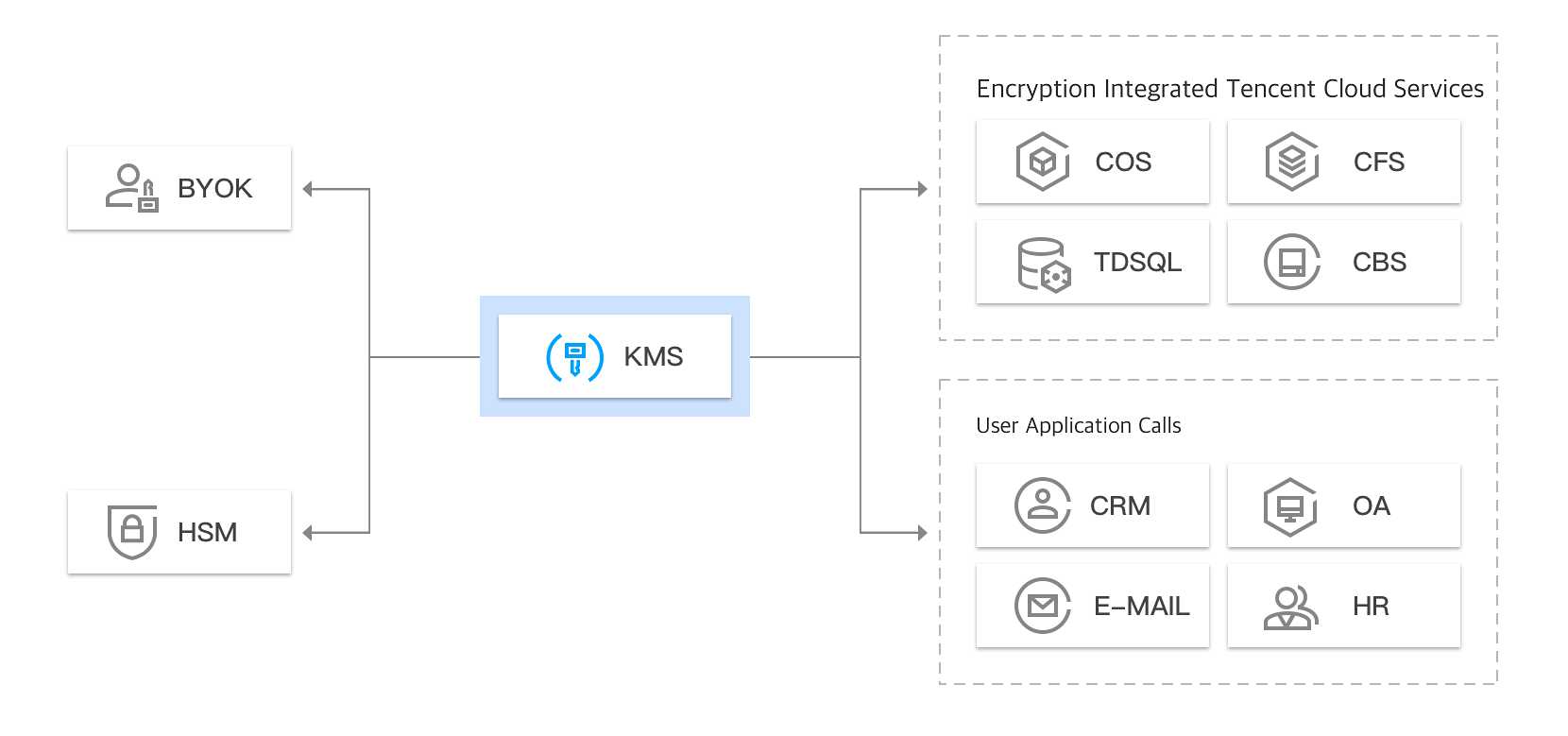
KMS can be seamlessly integrated with Tencent Cloud services such as COS, TencentDB for MySQL, and CBS, enabling you to manage their keys through KMS.

KMS console is integrated with CAM and Cloud Monitor, enabling you to create keys easily for access control. Management operations and keys usages are also logged.

KMS is deployed in a multi-datacenter distributed clustering manner with hot backup enabled, and its underlying HSM devices are deployed in dual-datacenter cold backup manner, ensuring high availability.

KMS allows you to use your own key to encrypt and decrypt sensitive data by implementing Bring Your Own Key (BYOK) solution.
KMS provides a wealth of management features, including key creation, enabling, disabling, rotation settings, alias settings, key details viewing, and related information modification, letting you create and protect keys and implement key management policies with ease.
KMS features a customer master key (CMK) rotation capability which is disabled by default and can be enabled as needed. If enabled, a CMK will be rotated once per year. Managed by the KMS system, key rotation is imperceptible to users. Existing ciphertexts encrypted by the CMK can still be decrypted, only new encryption tasks use the new CMK.
Fully integrated with CAM, KMS can control which accounts and roles can access or manage your sensitive keys through identity and policy management.
KMS is integrated with Tencent Cloud Audit to record all API requests for detailed logs of key management activities and key usage.
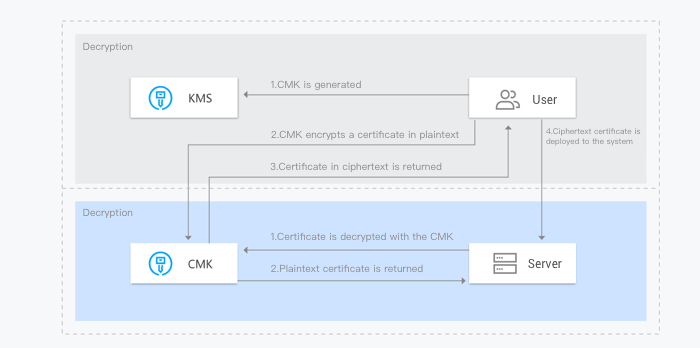
Sensitive information encryption is a core capability of KMS, mainly used to protect sensitive data (less than 4 KB) on the server disks such as keys, certificates and configuration files.
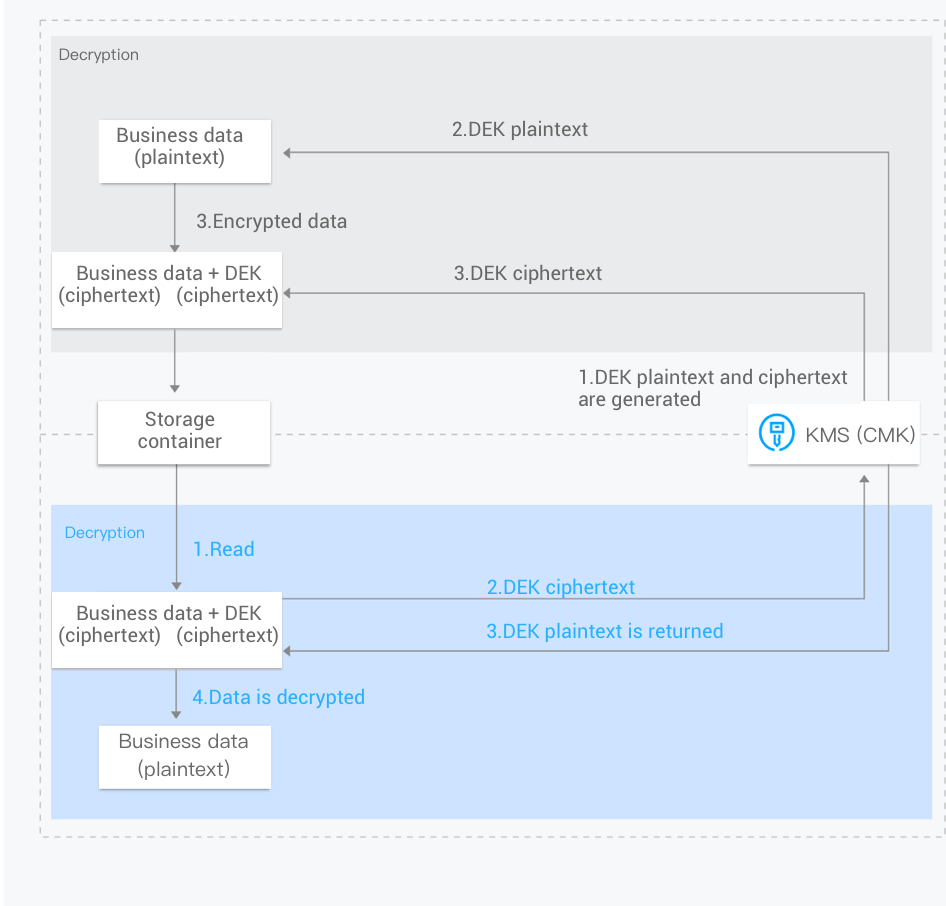
Envelope encryption is a high-performance encryption and decryption solution for massive amounts of data. With the aid of envelope encryption in KMS, only the data encryption keys (DEKs) need to be transferred to the KMS server (which are encrypted and decrypted with the CMK), and all data is processed with efficient local symmetric encryption which has little impact on user access.
BYOK solution allows you to use your own key to encrypt and decrypt sensitive data on Tencent Cloud. When you implement a BYOK solution, you can generate a CMK with no key material. You can then import your own key to form an external CMK which can be managed and distributed with KMS.
Tencent Cloud Key Management System offers monthly subscription billing model. You can refer to billing overview for details.