Based on Tencent Security's massive amounts of threat data, Cloud Workload Protection Platform (CWPP) leverages machine learning to provide a wide variety of security protection services, including asset management, trojan detection and prevention, intrusion detection, vulnerability alerting, and security baseline. It helps build a security protection system to cope with major network security risks faced by servers. It supports unified security protection for non-Tencent Cloud servers and enables effortless security intelligence sharing in Tencent Cloud, providing the same level of protection for private IDCs as in the cloud.
Cloud Workload Protection Platform
Protect your servers with the all-around security services provided by Cloud Workload Protection Platform (CWPP)

Collect and manage the fingerprint data of your assets, including accounts, ports, processes, and applications.

Fight against trojan virus, such as miner trojans and blackmail trojans, based on Tencent’s certified AI-based virus database, Webshell detection engine and TAV engine.

Monitor for intrusion events and send alerts. Intrusion behaviors including abnormal logins, brute-force attacks, malicious requests, high-risk commands, local privilege escalation, reverse shell, etc.

Scan for Linux, Windows, Web-CMS and application vulnerabilities. Trigger alerts when vulnerabilities are detected and provide professional fix solutions.

Manage security baselines with the preset baseline check items (CIS, weak password). Check the baseline score and resolve the risks according to the suggested solutions.

Monitor core files for abnormal behaviors and trigger alerts. You can handle the alerts as needed. It’s only available for Linux 3.10 and later versions.
Use Case
Services deployed on the Internet are always confronted with threat and attacks. Lack of effective pre-warning and response mechanism can lead to enterprise data breach or service interruption.
Solution
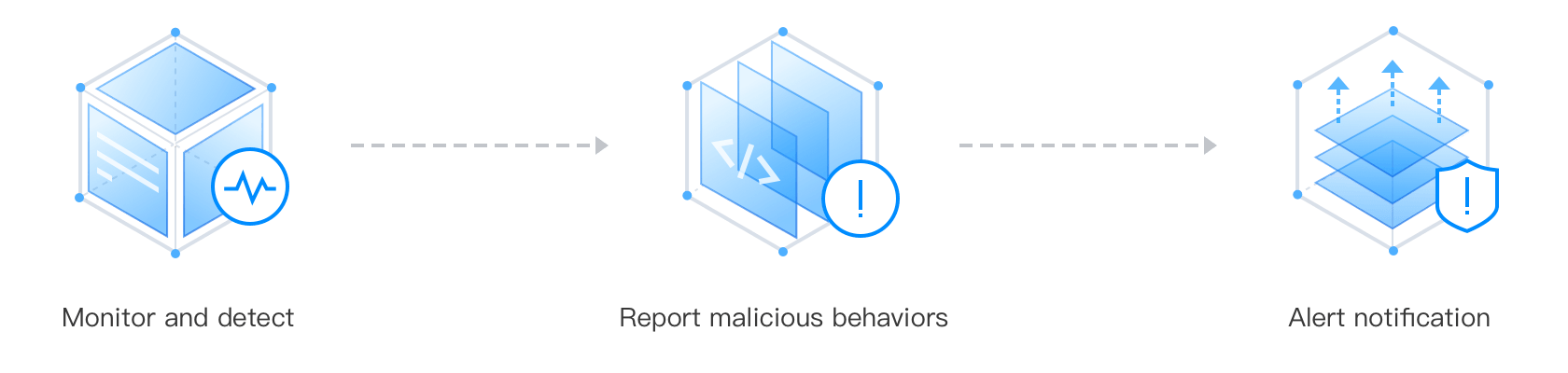
Discover intrusion events with the help of CWPP intrusion defense, which can detect virus files, abnormal logins, brute-force attacks, malicious requests, high-risk commands, local privilege escalation, and reserve shell.
Use Case
When new vulnerabilities appear, enterprises do not have a professional security team to assess the vulnerability risk.
Solution
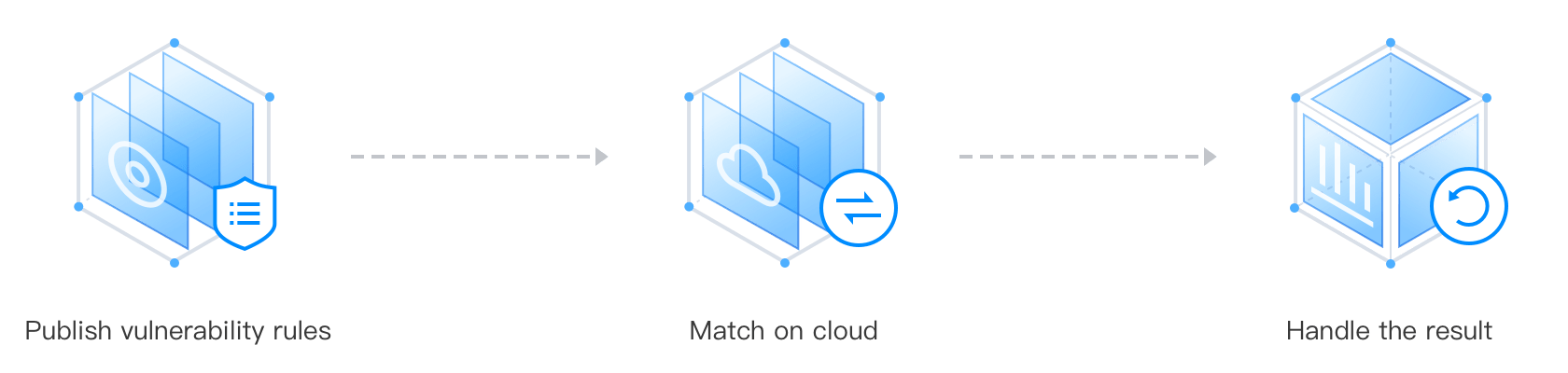
With the Vulnerability Scan feature of CWPP, enterprises can monitor the impact of new vulnerabilities, and repair them according to the suggestions provided by CWPP experts .
Use Case
There are many types of software on the server. When a new vulnerability breaks out, it is impossible to quickly count the business impact.
Solution
By utilizing the Asset Fingerprint feature of CWPP, the enterprise can quickly identify, classify and count the components on the server, build a panorama of enterprise asset fingerprints, and improve the efficiency of emergency response.

Use Case
Enterprises need to comply with the industry-specific security standards. But they are in lack of the related capabilities and experiences.
Solution
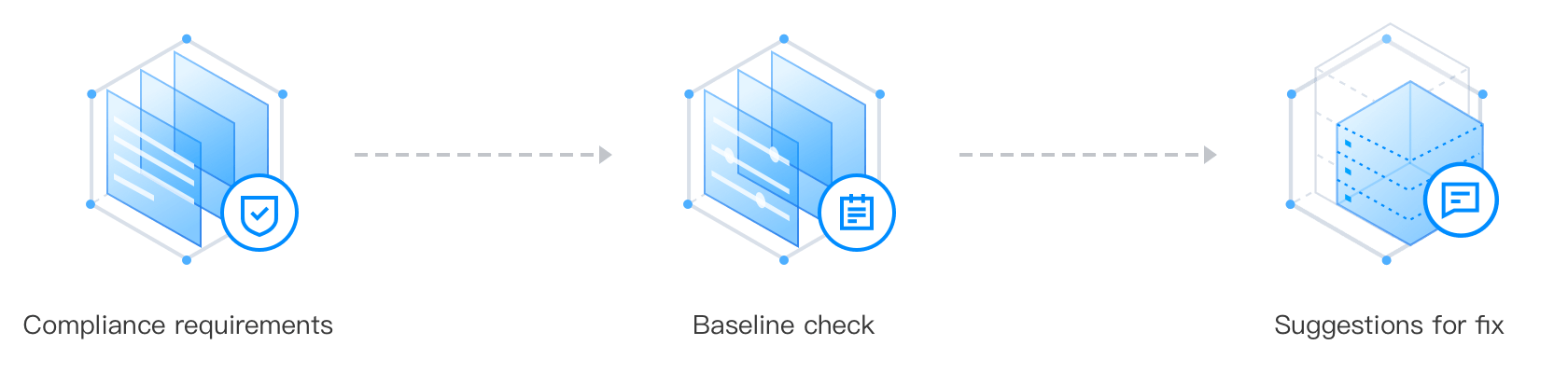
Check the service with the preset and custom baseline policies, and fix the detected problems according to the professional suggestions.
Cloud Workload Protection Platform (CWPP) offers different subscription plans. Go to the purchase page to check details of different plans.