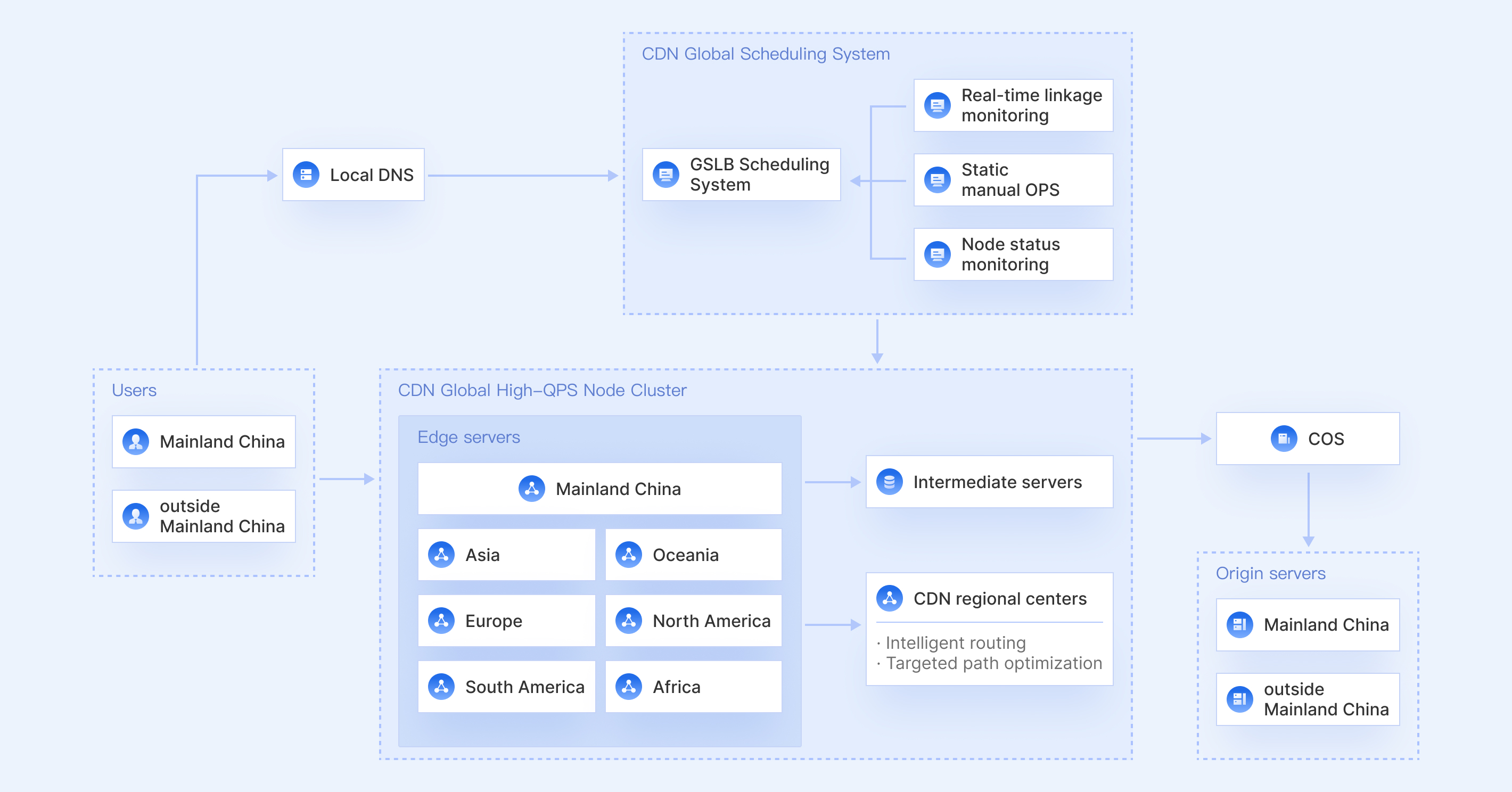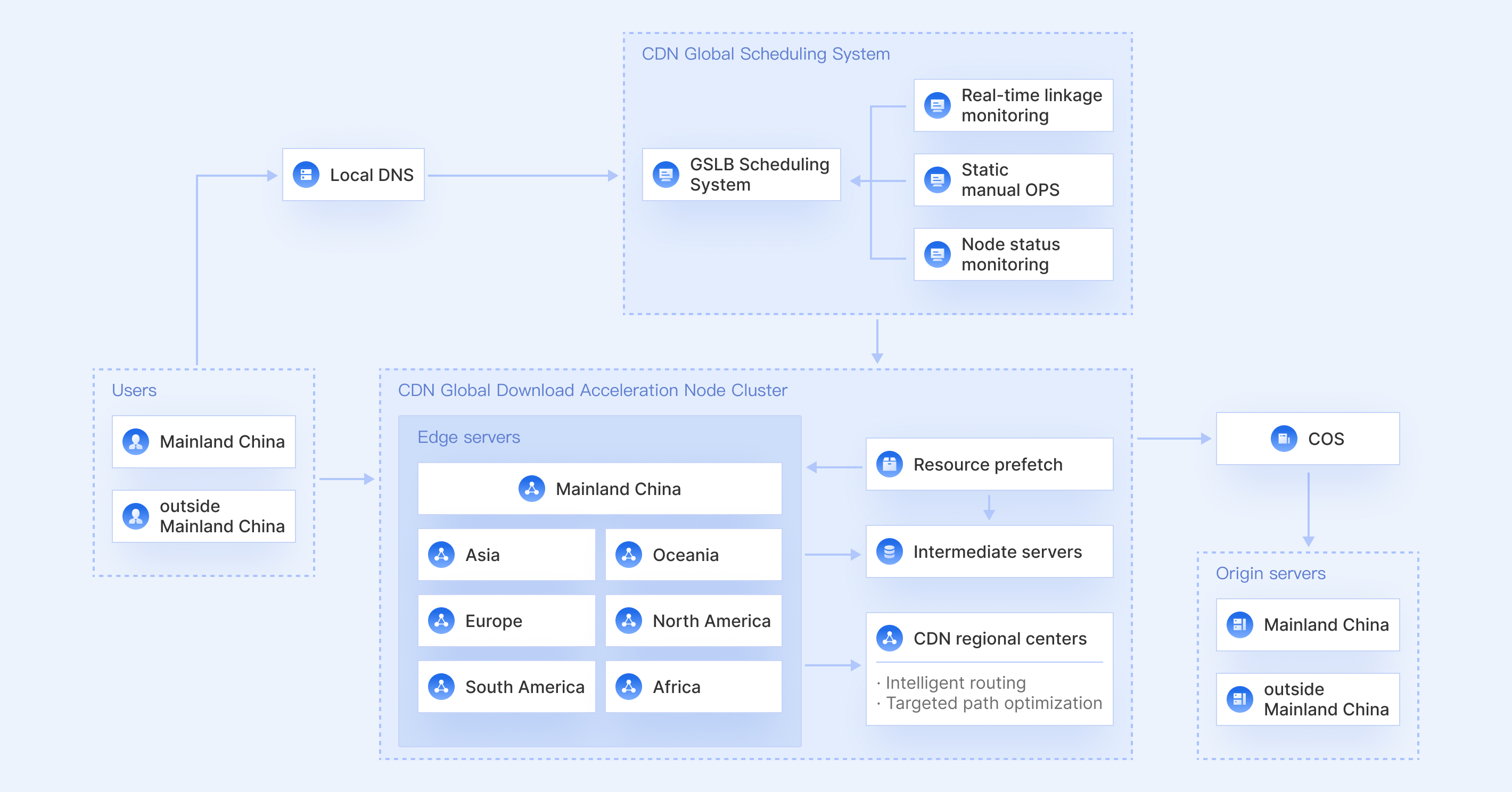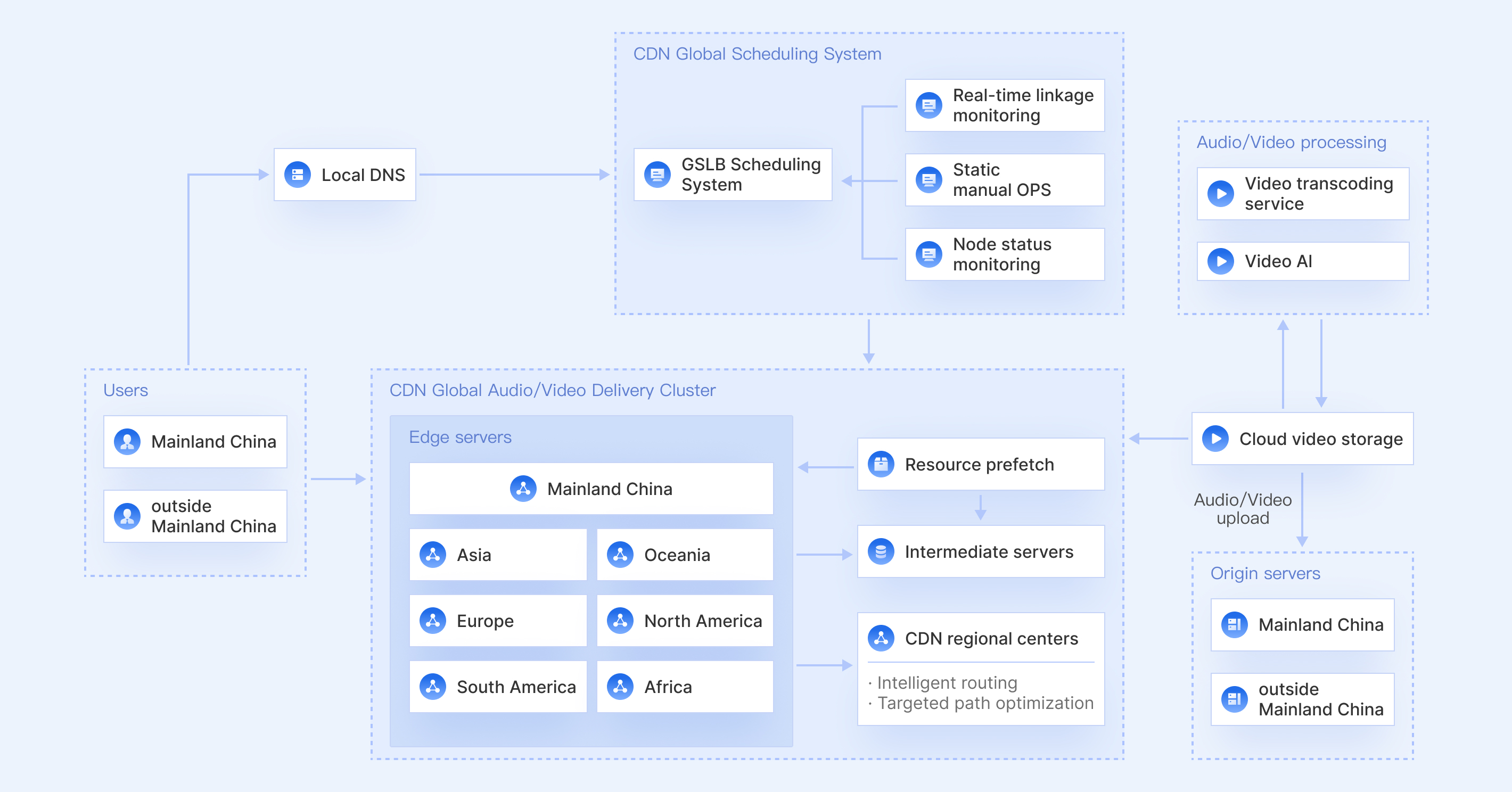








You can set an access limit and create blocklists/allowlists for referer, IP, and UA to block specific requests. A wide selection of timestamp-based hotlink protection rules is available to prevent unauthorized use of your resources and avoid potential losses.

You can set an access limit and create blocklists/allowlists for referer, IP, and UA to block specific requests. A wide selection of timestamp-based hotlink protection rules is available to prevent unauthorized use of your resources and avoid potential losses.

You can set the cache expiration time of your contents on different CDN nodes according to file type, directory, and path to effectively improve the node hit rate and reduce the origin-pull bandwidth consumption.

You can set the cache expiration time of your contents on different CDN nodes according to file type, directory, and path to effectively improve the node hit rate and reduce the origin-pull bandwidth consumption.

Tencent Cloud provides free SSL certificates. You can apply for a free certificate with us or purchase a preferred one from Symantec or GeoTrust, and easily deploy it to CDN for HTTPS access. After deployment, you can use features such as force HTTPS redirection (301/302 redirection) and HTTP 2.0.

Tencent Cloud provides free SSL certificates. You can apply for a free certificate with us or purchase a preferred one from Symantec or GeoTrust, and easily deploy it to CDN for HTTPS access. After deployment, you can use features such as force HTTPS redirection (301/302 redirection) and HTTP 2.0.

Comprehensive real-time monitoring is available for counting statistics of traffic, bandwidth, requests, hit rate, origin-pull failure rate, and specific status codes at the minute level, helping you understand the CDN service status and monitor origin servers instantly. Alarm policies can be configured as needed in the Cloud Monitor Console, enabling you to stay up to date with business fluctuations.Supports online scale-out when the database has insufficient processing capability or

Comprehensive real-time monitoring is available for counting statistics of traffic, bandwidth, requests, hit rate, origin-pull failure rate, and specific status codes at the minute level, helping you understand the CDN service status and monitor origin servers instantly. Alarm policies can be configured as needed in the Cloud Monitor Console, enabling you to stay up to date with business fluctuations.Supports online scale-out when the database has insufficient processing capability or

After the contents are updated on or deleted from the origin server, URL/directory purge tasks can be submitted in the console or through open APIs to delete the cached resources across the entire network and ensure that users access the latest resources. URL prefetch tasks can also be submitted for the cache nodes to actively pull the specified resources from the origin server and cache them for improved access speed.

After the contents are updated on or deleted from the origin server, URL/directory purge tasks can be submitted in the console or through open APIs to delete the cached resources across the entire network and ensure that users access the latest resources. URL prefetch tasks can also be submitted for the cache nodes to actively pull the specified resources from the origin server and cache them for improved access speed.

Log DownloadAccess logs for all domain names in the past 30 days are provided by default. Logs contain 15 fields, namely request time, client IP, domain name, access path, number of bytes, client location, client ISP, status code, Referer, response time, User-Agent, Range, HTTP Method, HTTP protocol identification, and cache hit/miss. The logs can be downloaded for analysis.

Log DownloadAccess logs for all domain names in the past 30 days are provided by default. Logs contain 15 fields, namely request time, client IP, domain name, access path, number of bytes, client location, client ISP, status code, Referer, response time, User-Agent, Range, HTTP Method, HTTP protocol identification, and cache hit/miss. The logs can be downloaded for analysis.

You can set an access limit and create blocklists/allowlists for referer, IP, and UA to block specific requests. A wide selection of timestamp-based hotlink protection rules is available to prevent unauthorized use of your resources and avoid potential losses.

You can set the cache expiration time of your contents on different CDN nodes according to file type, directory, and path to effectively improve the node hit rate and reduce the origin-pull bandwidth consumption.

Tencent Cloud provides free SSL certificates. You can apply for a free certificate with us or purchase a preferred one from Symantec or GeoTrust, and easily deploy it to CDN for HTTPS access. After deployment, you can use features such as force HTTPS redirection (301/302 redirection) and HTTP 2.0.

Comprehensive real-time monitoring is available for counting statistics of traffic, bandwidth, requests, hit rate, origin-pull failure rate, and specific status codes at the minute level, helping you understand the CDN service status and monitor origin servers instantly. Alarm policies can be configured as needed in the Cloud Monitor Console, enabling you to stay up to date with business fluctuations.Supports online scale-out when the database has insufficient processing capability or

After the contents are updated on or deleted from the origin server, URL/directory purge tasks can be submitted in the console or through open APIs to delete the cached resources across the entire network and ensure that users access the latest resources. URL prefetch tasks can also be submitted for the cache nodes to actively pull the specified resources from the origin server and cache them for improved access speed.

Log DownloadAccess logs for all domain names in the past 30 days are provided by default. Logs contain 15 fields, namely request time, client IP, domain name, access path, number of bytes, client location, client ISP, status code, Referer, response time, User-Agent, Range, HTTP Method, HTTP protocol identification, and cache hit/miss. The logs can be downloaded for analysis.