



Establish an encrypted channel for data transmission to ensure that the data has the following features during the transmission process:
- Eavesdropping Prevention
- Tamper Resistance
- MITM Protection

Establish an encrypted channel for data transmission to ensure that the data has the following features during the transmission process:
- Eavesdropping Prevention
- Tamper Resistance
- MITM Protection

Logical Segmentation is implemented based on RBAC (Role-Based Access Control) to ensure:
- Each tenant is assigned a Dedicated Storage Volume
- Prevent Lateral Movement through Namespace and access policy (ACL)

Logical Segmentation is implemented based on RBAC (Role-Based Access Control) to ensure:
- Each tenant is assigned a Dedicated Storage Volume
- Prevent Lateral Movement through Namespace and access policy (ACL)

Deploy the SIEM (Security Information and Event Management) system to implement:
- Full Immutable Logging, recording CRUD behaviors throughout the process
- Real-time alarm for abnormal access
- Forensic Readiness, supporting Chain of Custody traceability

Deploy the SIEM (Security Information and Event Management) system to implement:
- Full Immutable Logging, recording CRUD behaviors throughout the process
- Real-time alarm for abnormal access
- Forensic Readiness, supporting Chain of Custody traceability

Data generated during your use of this service will be processed in strict compliance with "Category C Privacy Policy Module" and "Category C Data Processing and Security Agreement Module".

Data generated during your use of this service will be processed in strict compliance with "Category C Privacy Policy Module" and "Category C Data Processing and Security Agreement Module".

Establish an encrypted channel for data transmission to ensure that the data has the following features during the transmission process:
- Eavesdropping Prevention
- Tamper Resistance
- MITM Protection

Logical Segmentation is implemented based on RBAC (Role-Based Access Control) to ensure:
- Each tenant is assigned a Dedicated Storage Volume
- Prevent Lateral Movement through Namespace and access policy (ACL)

Deploy the SIEM (Security Information and Event Management) system to implement:
- Full Immutable Logging, recording CRUD behaviors throughout the process
- Real-time alarm for abnormal access
- Forensic Readiness, supporting Chain of Custody traceability

Data generated during your use of this service will be processed in strict compliance with "Category C Privacy Policy Module" and "Category C Data Processing and Security Agreement Module".

Frequently
Asked Questions
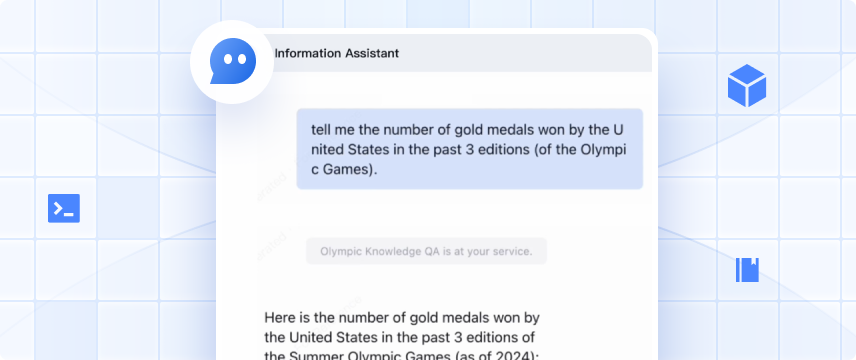
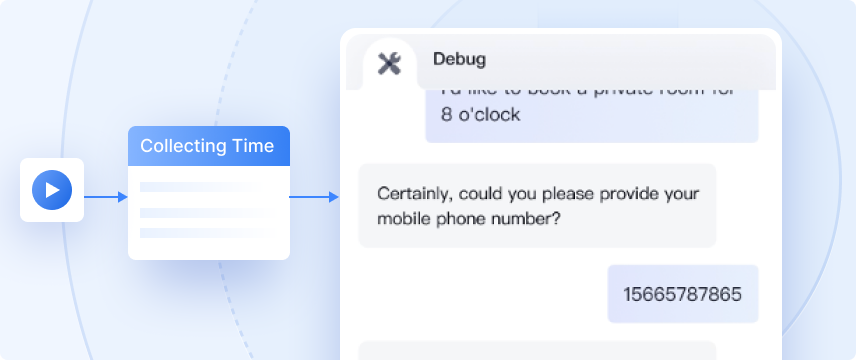
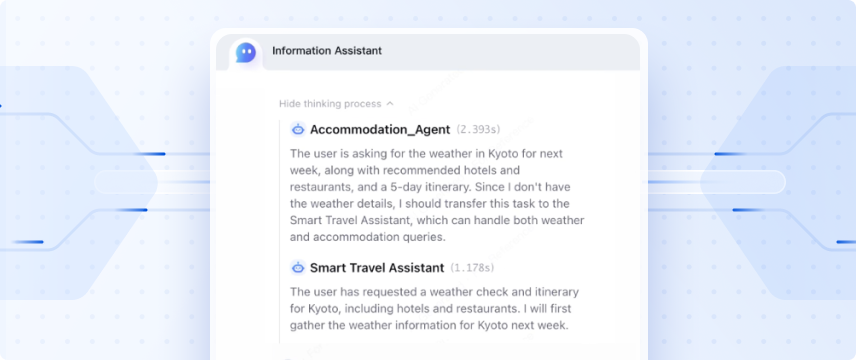
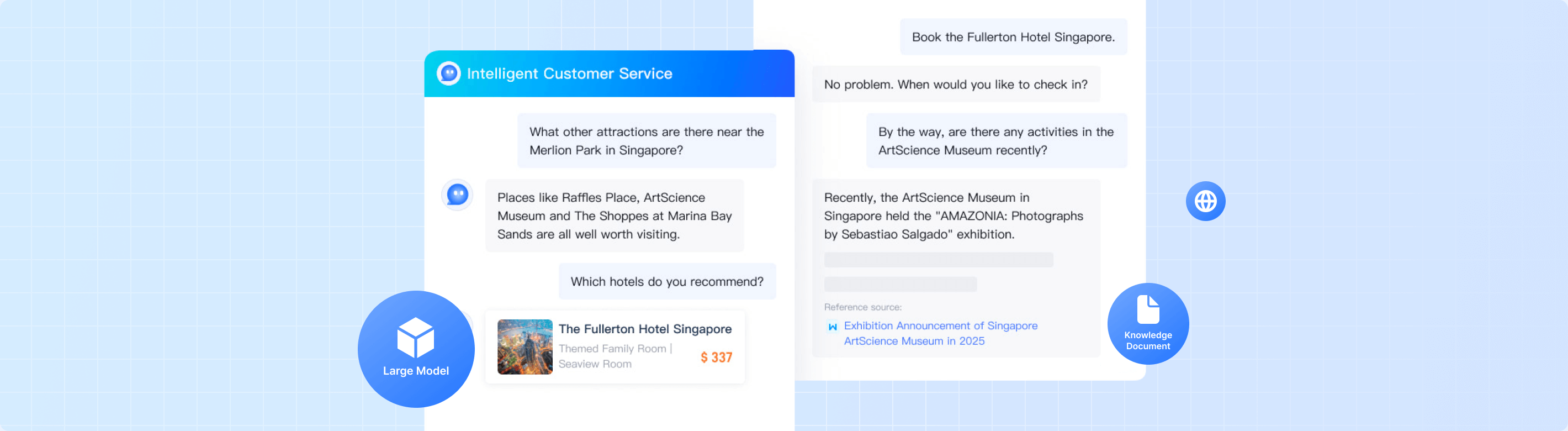
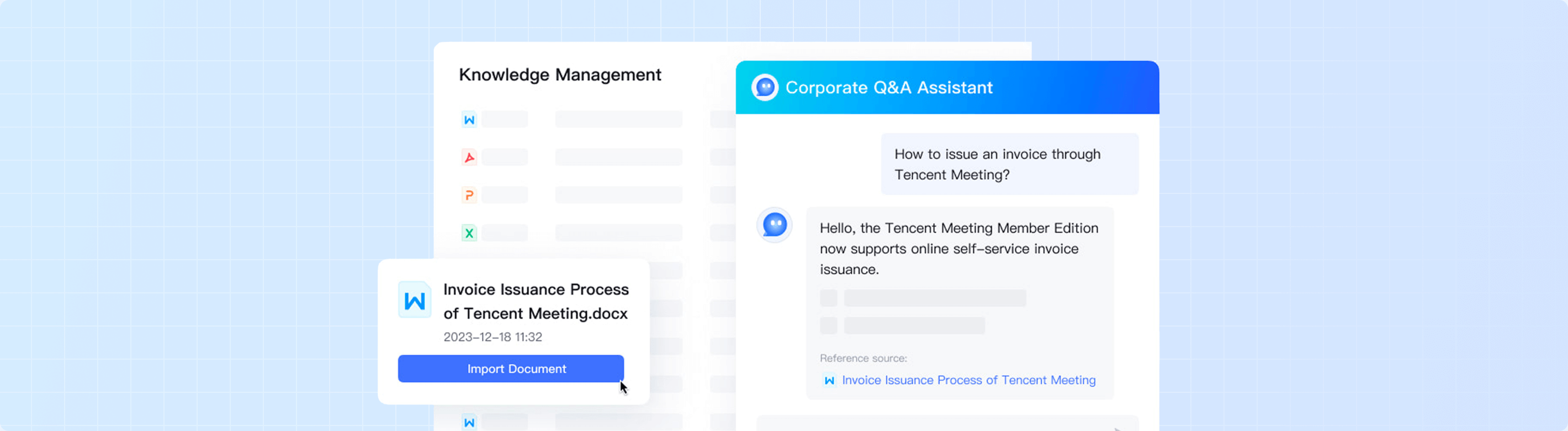
Tencent Cloud Agent Development Platform(ADP)is an Agent application development platform designed for enterprises and partners. By combining enterprise's exclusive data, it provides application paradigms, such as knowledge Q&A, and API services to enable faster and more efficient development and implementation of Agent applications in enterprise service scenarios. By integrating with the full-strength version of DeepSeek, enterprises can quickly build self-service inquiry services based on natural language conversations and use operation tools to improve service quality at a low cost. This platform is mainly targeted at enterprise operation and maintenance personnel. Through the configuration management platform, they can edit and maintain customer-level knowledge bases and business APIs. They can improve their efficiency in training robots and maintaining knowledge bases through machine learning methods.
Frequently
Asked Questions
Tencent Cloud Agent Development Platform(ADP)is an Agent application development platform designed for enterprises and partners. By combining enterprise's exclusive data, it provides application paradigms, such as knowledge Q&A, and API services to enable faster and more efficient development and implementation of Agent applications in enterprise service scenarios. By integrating with the full-strength version of DeepSeek, enterprises can quickly build self-service inquiry services based on natural language conversations and use operation tools to improve service quality at a low cost. This platform is mainly targeted at enterprise operation and maintenance personnel. Through the configuration management platform, they can edit and maintain customer-level knowledge bases and business APIs. They can improve their efficiency in training robots and maintaining knowledge bases through machine learning methods.