- Release Notes
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Origin Server Management
- Access Management
- Access Acceleration Connection
- Connection Group Management
- Statistics
- Configuring Permissions
- Access Tencent Cloud Observability Platform
- Certificate Management
- Obtaining Real Client IP
- Country/Region Mapping
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Origin Server APIs
- Listener APIs
- ModifyUDPListenerAttribute
- ModifyTCPListenerAttribute
- ModifyHTTPSListenerAttribute
- ModifyHTTPListenerAttribute
- DescribeUDPListeners
- DescribeTCPListeners
- DescribeListenerRealServers
- DescribeHTTPSListeners
- DescribeHTTPListeners
- DeleteListeners
- CreateUDPListeners
- CreateTCPListeners
- CreateHTTPSListener
- CreateHTTPListener
- BindListenerRealServers
- Rule APIs
- SetAuthentication
- ModifyRuleAttribute
- ModifyDomain
- ModifyCertificate
- DescribeRules
- DescribeRuleRealServers
- DeleteRule
- DeleteDomain
- CreateRule
- CreateDomain
- BindRuleRealServers
- DescribeDomainErrorPageInfo
- DeleteDomainErrorPageInfo
- CreateDomainErrorPageInfo
- DescribeRulesByRuleIds
- DescribeDomainErrorPageInfoByIds
- DescribeCustomHeader
- DescribeBlackHeader
- CreateCustomHeader
- Connection Group APIs
- Connection APIs
- OpenSecurityPolicy
- OpenProxies
- ModifySecurityRule
- ModifyProxyConfiguration
- ModifyProxiesProject
- ModifyProxiesAttribute
- InquiryPriceCreateProxy
- DestroyProxies
- DescribeSecurityPolicyDetail
- DescribeProxyDetail
- DescribeProxyAndStatisticsListeners
- DescribeProxiesStatus
- DescribeProxies
- DescribeDestRegions
- DescribeAccessRegionsByDestRegion
- DescribeAccessRegions
- DeleteSecurityRules
- DeleteSecurityPolicy
- CreateSecurityRules
- CreateSecurityPolicy
- CreateProxy
- CloseSecurityPolicy
- CloseProxies
- CheckProxyCreate
- DescribeSecurityRules
- Certificate APIs
- Other APIs
- Data Types
- Error Codes
- Service Agreement
- FAQs
- Contact Us
- Glossary
- Release Notes
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Origin Server Management
- Access Management
- Access Acceleration Connection
- Connection Group Management
- Statistics
- Configuring Permissions
- Access Tencent Cloud Observability Platform
- Certificate Management
- Obtaining Real Client IP
- Country/Region Mapping
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Origin Server APIs
- Listener APIs
- ModifyUDPListenerAttribute
- ModifyTCPListenerAttribute
- ModifyHTTPSListenerAttribute
- ModifyHTTPListenerAttribute
- DescribeUDPListeners
- DescribeTCPListeners
- DescribeListenerRealServers
- DescribeHTTPSListeners
- DescribeHTTPListeners
- DeleteListeners
- CreateUDPListeners
- CreateTCPListeners
- CreateHTTPSListener
- CreateHTTPListener
- BindListenerRealServers
- Rule APIs
- SetAuthentication
- ModifyRuleAttribute
- ModifyDomain
- ModifyCertificate
- DescribeRules
- DescribeRuleRealServers
- DeleteRule
- DeleteDomain
- CreateRule
- CreateDomain
- BindRuleRealServers
- DescribeDomainErrorPageInfo
- DeleteDomainErrorPageInfo
- CreateDomainErrorPageInfo
- DescribeRulesByRuleIds
- DescribeDomainErrorPageInfoByIds
- DescribeCustomHeader
- DescribeBlackHeader
- CreateCustomHeader
- Connection Group APIs
- Connection APIs
- OpenSecurityPolicy
- OpenProxies
- ModifySecurityRule
- ModifyProxyConfiguration
- ModifyProxiesProject
- ModifyProxiesAttribute
- InquiryPriceCreateProxy
- DestroyProxies
- DescribeSecurityPolicyDetail
- DescribeProxyDetail
- DescribeProxyAndStatisticsListeners
- DescribeProxiesStatus
- DescribeProxies
- DescribeDestRegions
- DescribeAccessRegionsByDestRegion
- DescribeAccessRegions
- DeleteSecurityRules
- DeleteSecurityPolicy
- CreateSecurityRules
- CreateSecurityPolicy
- CreateProxy
- CloseSecurityPolicy
- CloseProxies
- CheckProxyCreate
- DescribeSecurityRules
- Certificate APIs
- Other APIs
- Data Types
- Error Codes
- Service Agreement
- FAQs
- Contact Us
- Glossary
Adding an HTTP/HTTPS Listener
- Log in to the GAAP console. Enter the Access Management page. Click the ID/Connection Name of the specific connection.
- On the page that appears, select HTTP/HTTPS Listener Management > Create. You can select either the HTTP or HTTPS protocol. (Note: currently, HTTP/HTTPS listener configuration is not supported for IPv6 connections.)
- The specific configuration is as follows:
- If HTTP is selected, only the listener port number is required, and the listener will forward packets using the HTTP protocol by default.
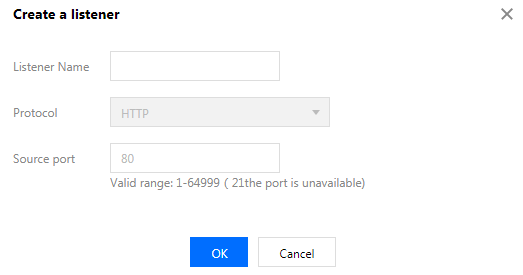
- If HTTPS is selected, certificates and additional information need to be configured, as shown below:
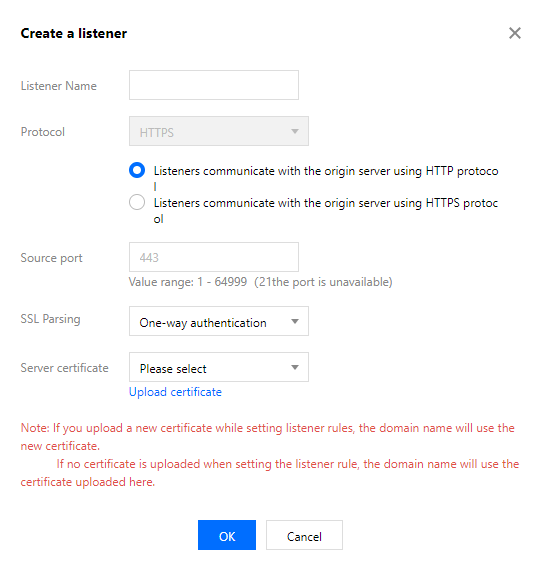
- Listeners communicate with the origin server using HTTP protocol means that the HTTPS protocol is used between the client and the acceleration connection VIP, while the HTTP protocol is used between the VIP and the origin server, which requires an HTTP port to be opened on the origin server;
Listeners communicate with the origin server using HTTPS protocol means that the HTTPS protocol is used between the client and the origin server, which requires an HTTPS port to be opened on the origin server. - SSL Parsing: Both one-way and two-way authentication are supported.
- Server/Client Certificate: Upload/Update a certificate in Certificate Management of the GAAP console, and then select the certificate when creating/modifying an HTTPS listener. For more information, see Certificate Management.
- Listeners communicate with the origin server using HTTP protocol means that the HTTPS protocol is used between the client and the acceleration connection VIP, while the HTTP protocol is used between the VIP and the origin server, which requires an HTTP port to be opened on the origin server;
- If HTTP is selected, only the listener port number is required, and the listener will forward packets using the HTTP protocol by default.
Configuring an HTTP/HTTPS Listener
Under the HTTP/HTTPS Listener Management tab, click Set a rule in the operation column to enter the domain name and URL management page.
Creating a distribution
- To add a domain name for an HTTP listener, enter a valid domain name. It must be 3 to 80 characters containing [a-z], [0–9], [.-]. Only exact match is supported.
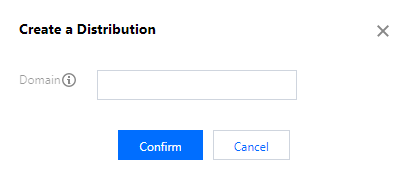
- To add a domain name for an HTTPS listener, enter a valid domain name and select the corresponding server certificate.
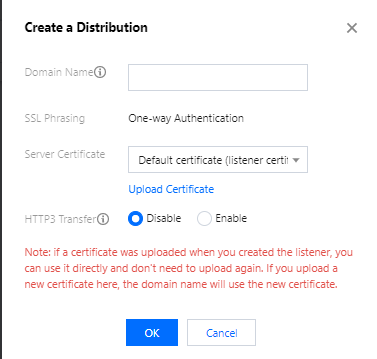
- Domain: 3 to 80 characters containing [a-z], [0–9], [.-]. Only exact match is supported.
- Server Certificate: by default, it is the certificate used to create the listener. If you upload another certificate, the domain name is authenticated with the uploaded certificate.
- HTTP3 Transfer: enables it to support QUIC. If the client does not support this protocol, HTTP2.0 and previous versions will be used for access.
Adding a rule
After adding a domain name, click Add Rule to add the corresponding URL and select the origin server type. You can add up to 20 URL rules for one domain name as shown below:
Basic configuration:
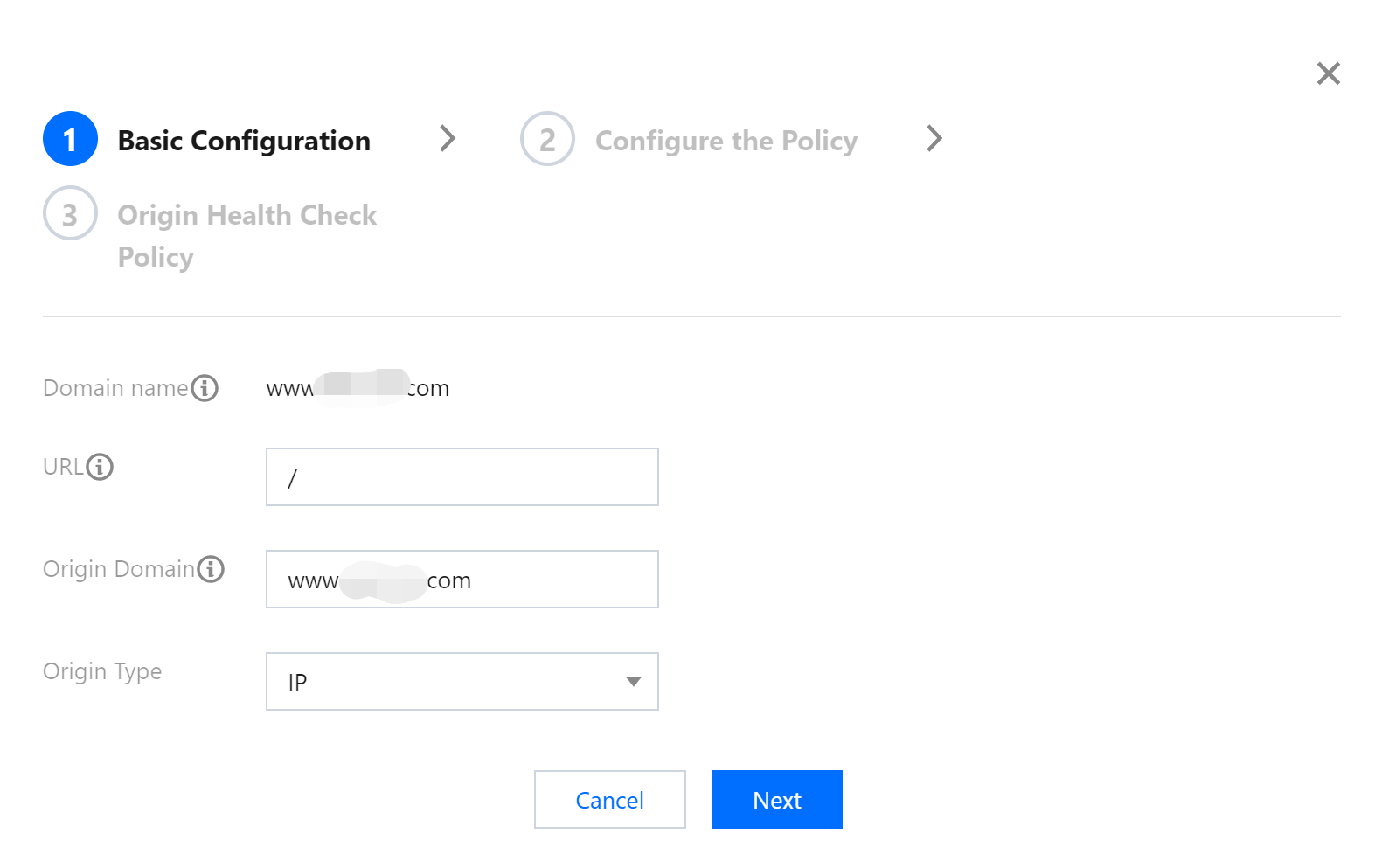
- URL: It contains 1-80 characters in the following types: [a-z], [0–9], and [_.-/].
- Origin Domain: The host field of the origin-pull request can be modified.
- Origin Server Type: It supports an IP or a domain name. A listener supports only one type.
Processing policy for the origin server:
Configure the origin server processing policy, that is, if a listener is bound with multiple origin servers, you need to select a scheduling policy for origin servers.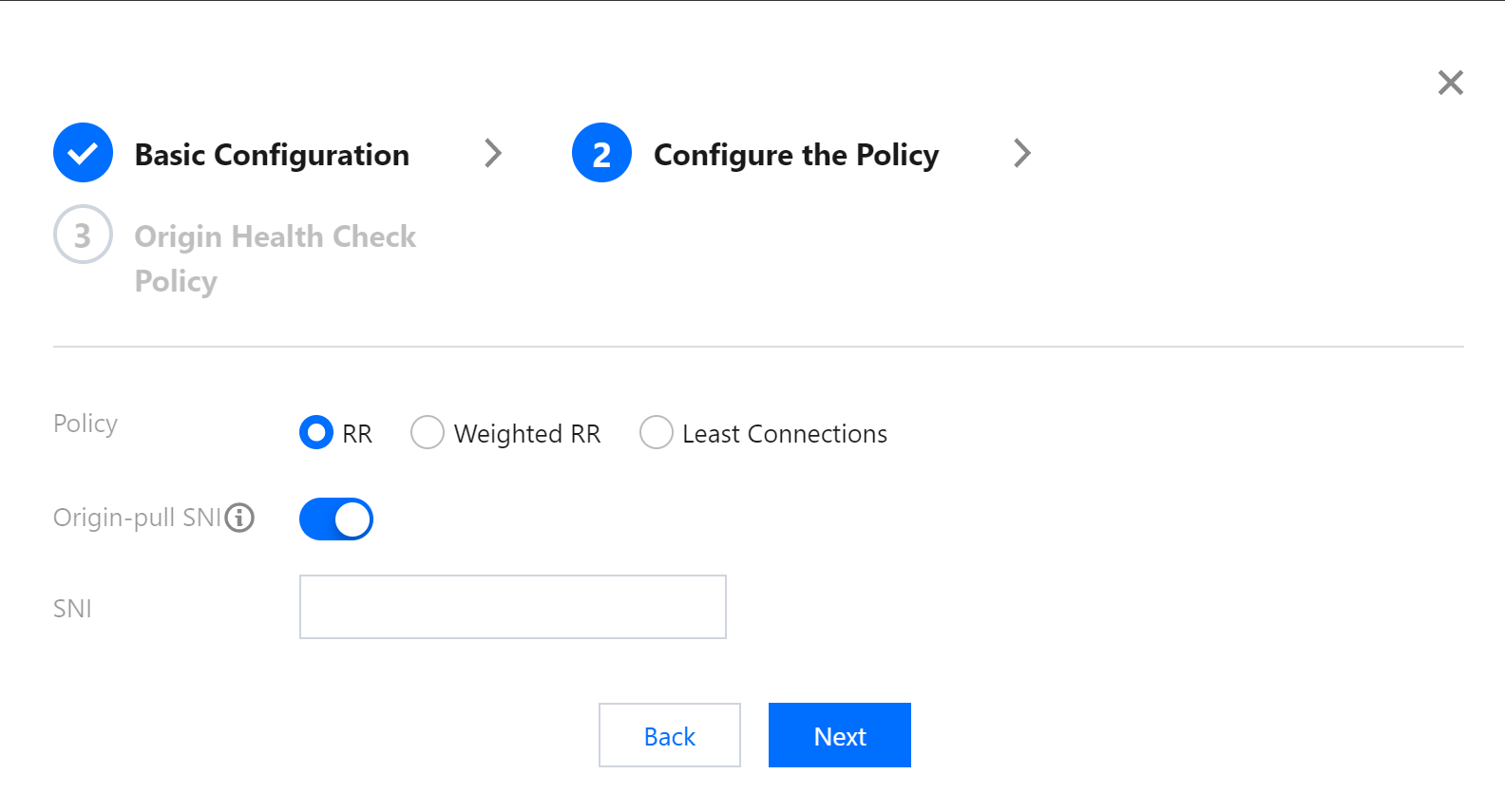
- RR: Multiple origin servers perform origin-pull according to the RR policy.
- Weighted RR: Multiple origin servers perform origin-pull according to the weight ratio (this configuration is not supported if the origin server type is a domain name).
- Least Connections: It schedules the origin server with the least number of connections first.
- Origin-pull SNI: It forwards SNI to the origin server before an SSL connection is established, and based on the SNI value the origin server returns a certificate.
Origin health check mechanism:
The health check mechanism can be enabled. For the current domain name, you can configure an independent check URL. HEAD and GET request methods are supported. Check status codes include http_1xx, http_2xx, http_3xx, http_4xx, and http_5xx, and one or multiple codes can be selected. When a specified status code is detected, the listener considers that the backend origin server is normal. If no status code is detected, the listener considers that the backend origin server has an exception.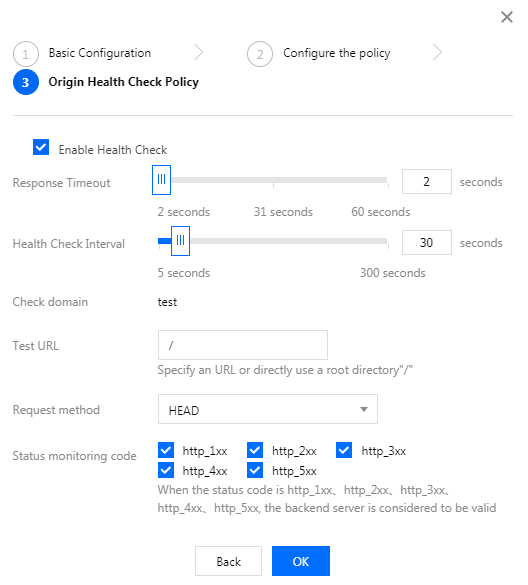
Modifying a domain name
After adding a domain name, you can click Modify Domain Name to modify the domain name.
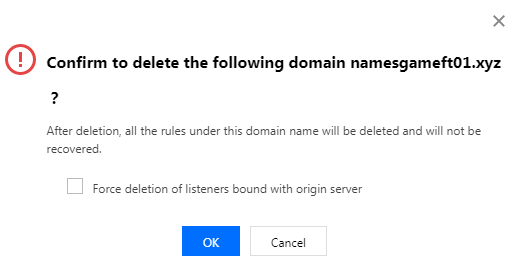
Deleting a domain name
After adding a domain name, you can click Delete to delete the domain name. If a rule under the domain name has been bound to an origin server, you need to select Force deletion of listeners bound with origin server.
HTTP3 configuration
The HTTP3 configuration controls whether to support HTTP3 (QUIC). Currently, HTTP3 can only be configured for HTTPS listeners.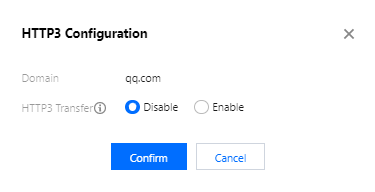
Modifying a rule
Refer to the Adding a rule section above. The main difference is that the domain name and origin server type cannot be modified.
Binding an origin server
For more information, see Binding Origin Server. You can bind different ports to different origin servers. For more information on the Cover Port and Complement Port features, see Binding TCP/UDP Listener to Origin Server.
Note:A rule can be bound to up to 100 origin servers.
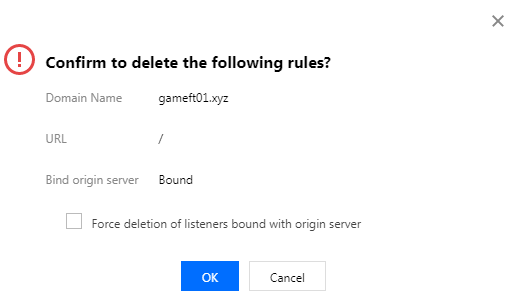
Deleting a rule
After adding a rule, you can click Delete to delete the rule. If the rule has been bound to an origin server, you need to select Force deletion of listeners bound with origin server first.
Configuring origin-pull request header
- After adding a rule, you can select More in the Operation column of the rule and click Set Origin-Pull Request Header.
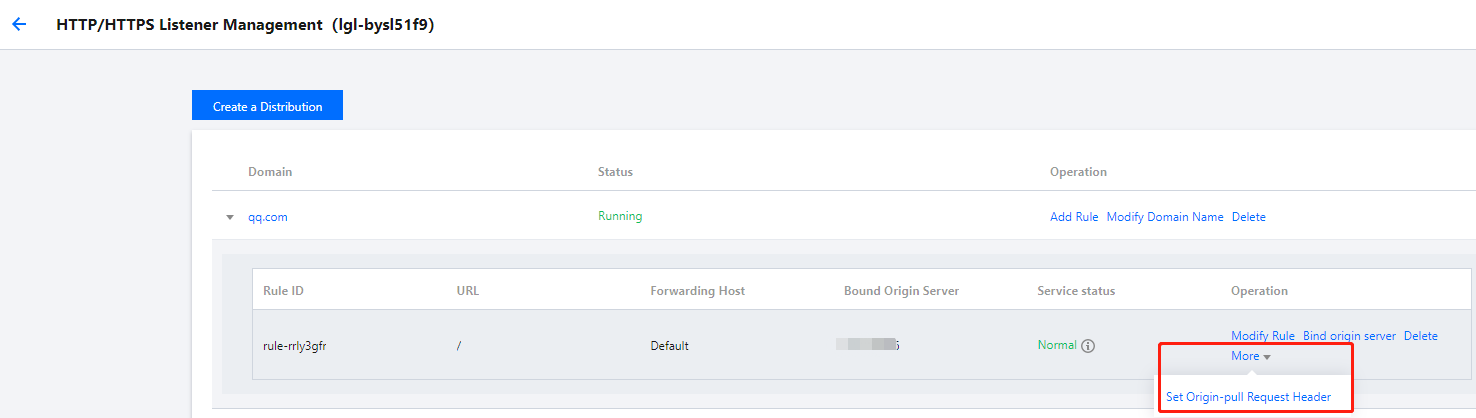
- Click Add Parameter and enter the request header's name and value. The
$remote_addrvariable can be used to specify the real client IP carried in the request header (by default, theX-Forwarded-Forheader carries the client IP for origin-pull). To use other variables with$, please submit a ticket.
Note:
- The
Keyvalue of the HTTP header name can contain 1–100 digits (0–9), letters (a–z, A–Z), and special symbols (-, _, :, and space). TheValuecan contain 1–100 characters;- Up to 10 origin-pull HTTP request headers can be configured for each rule;
- The standard headers listed below cannot be set/added/deleted in a self-service manner.
| www-authenticate | authorization | proxy-authenticate | proxy-authorization |
| age | cache-control | clear-site-data | expires |
| pragma | warning | accept-ch | accept-ch-lifetime |
| early-data | content-dpr | dpr | device-memory |
| save-data | viewport-width | width | last-modified |
| etag | if-match | if-none-match | if-modified-since |
| if-unmodified-since | vary | connection | keep-alive |
| Accept | accept-charset | expect | max-forwards |
| access-control-allow-origin | access-control-max-age | access-control-allow-headers | access-control-allow-methods |
| access-control-expose-headers | access-control-allow-credentials | access-control-request-headers | access-control-request-method |
| origin | timing-allow-origin | dnt | tk |
| content-disposition | content-length | content-type | content-encoding |
| content-language | content-location | forwarded | x-forwarded-host |
| x-forwarded-proto | via | from | host |
| referer-policy | allow | server | accept-ranges |
| range | if-range | content-range | cross-origin-embedder-policy |
| cross-origin-opener-policy | cross-origin-resource-policy | content-security-policy | content-security-policy-report-only |
| expect-ct | feature-policy | strict-transport-security | upgrade-insecure-requests |
| x-content-type-options | x-download-options | x-frame-options(xfo) | x-permitted-cross-domain-policies |
| x-powered-by | x-xss-protection | public-key-pins | public-key-pins-report-only |
| sec-fetch-site | sec-fetch-mode | sec-fetch-user | sec-fetch-dest |
| last-event-id | nel | ping-from | ping-to |
| report-to | transfer-encoding | te | trailer |
| sec-websocket-key | sec-websocket-extensions | sec-websocket-accept | sec-websocket-protocol |
| sec-websocket-version | accept-push-policy | accept-signature | alt-svc |
| date | large-allocation | link | push-policy |
| retry-after | signature | signed-headers | server-timing |
| service-worker-allowed | sourcemap | upgrade | x-dns-prefetch-control |
| x-firefox-spdy | x-pingback | x-requested-with | x-robots-tag |
| x-ua-compatible | max-age |
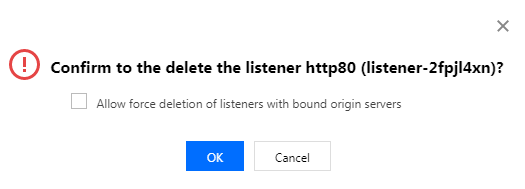
Deleting an HTTP/HTTPS Listener
Open the HTTP/HTTPS Listener Management tab, click Delete on the right of the selected listener. If the listener has been bound with the origin server, you need to check Allow force deletion of listeners bound with origin servers first. After it is deleted, acceleration of the listener port will stop.

 Yes
Yes
 No
No
Was this page helpful?