- Updates and Announcements
- User Tutorial
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Purchasing Instances
- Creating an Enterprise Edition Instance
- Access Configuration
- Manage Image Repository
- Image Distribution
- Image Security
- Synchronization and Replication
- Configuring Image Tag Retention
- Image Cleanup
- DevOps
- OCI Artifacts Management
- Operation Guide for TCR Individual
- Terminating/Returning Instances
- Best Practices
- TCR Personal migration
- Using the Delivery Assembly Line to Implement Container DevOps
- TKE Clusters Use the TCR Addon to Enable Secret-free Pulling of Container Images via Private Network
- Synchronizing Images to TCR Enterprise Edition from External Harbor
- TKE Serverless Clusters Pull TCR Container Images
- Image Data Synchronization and Replication Between Multiple Platforms in Hybrid Cloud
- Nearby Access Through Image Synchronization Between Multiple Global Regions
- Using Custom Domain Name and CCN to Implement Cross-Region Private Network Access
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Instance Management APIs
- DescribeInstances
- DescribeInstanceStatus
- CreateInstanceToken
- CreateInstance
- ModifyInstanceToken
- DescribeInstanceToken
- DeleteInstanceToken
- DeleteInstance
- RenewInstance
- CheckInstanceName
- CheckInstance
- ModifyInstance
- DescribeRegions
- DescribeInstanceCustomizedDomain
- DescribeImageAccelerateService
- DeleteInstanceCustomizedDomain
- DeleteImageAccelerateService
- CreateInstanceCustomizedDomain
- CreateImageAccelerationService
- Namespace APIs
- Image Repository APIs
- Custom Account APIs
- Trigger APIs
- Instance Synchronization APIs
- Access Control APIs
- Helm Chart APIs
- Tag Retention APIs
- Data Types
- Error Codes
- FAQs
- Service Level Agreement
- Contact Us
- Glossary
- Updates and Announcements
- User Tutorial
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Purchasing Instances
- Creating an Enterprise Edition Instance
- Access Configuration
- Manage Image Repository
- Image Distribution
- Image Security
- Synchronization and Replication
- Configuring Image Tag Retention
- Image Cleanup
- DevOps
- OCI Artifacts Management
- Operation Guide for TCR Individual
- Terminating/Returning Instances
- Best Practices
- TCR Personal migration
- Using the Delivery Assembly Line to Implement Container DevOps
- TKE Clusters Use the TCR Addon to Enable Secret-free Pulling of Container Images via Private Network
- Synchronizing Images to TCR Enterprise Edition from External Harbor
- TKE Serverless Clusters Pull TCR Container Images
- Image Data Synchronization and Replication Between Multiple Platforms in Hybrid Cloud
- Nearby Access Through Image Synchronization Between Multiple Global Regions
- Using Custom Domain Name and CCN to Implement Cross-Region Private Network Access
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Instance Management APIs
- DescribeInstances
- DescribeInstanceStatus
- CreateInstanceToken
- CreateInstance
- ModifyInstanceToken
- DescribeInstanceToken
- DeleteInstanceToken
- DeleteInstance
- RenewInstance
- CheckInstanceName
- CheckInstance
- ModifyInstance
- DescribeRegions
- DescribeInstanceCustomizedDomain
- DescribeImageAccelerateService
- DeleteInstanceCustomizedDomain
- DeleteImageAccelerateService
- CreateInstanceCustomizedDomain
- CreateImageAccelerationService
- Namespace APIs
- Image Repository APIs
- Custom Account APIs
- Trigger APIs
- Instance Synchronization APIs
- Access Control APIs
- Helm Chart APIs
- Tag Retention APIs
- Data Types
- Error Codes
- FAQs
- Service Level Agreement
- Contact Us
- Glossary
Image signing and signature verification can avoid man-in-the-middle attacks and the update and running of invalid images, ensuring image consistency across the entire linkage ranging from distribution to deployment. TCR Enterprise supports namespace-level automatic image signing. When an image is pushed to the repository, it will be automatically signed according to the matched signing policy to ensure image content trustworthiness in your repository.
Prerequisites
Before using the image signing feature, you need to perform the following operations:
If you are using a sub-account, you must have granted the sub-account operation permissions for the corresponding instance. For more information, see Example of Authorization Solution of TCR Enterprise.
Key Management Service (KMS) has been activated.
Directions
Creating an asymmetric signature verification key
Log in to the KMS console.
Choose Key Management > Customer Managed CMK and click Create.
In the Create Key window that pops up, set key parameters and click OK. The container signature feature requires that the KMS key usage be set to Asymmetric Signature Verification and the encryption algorithm be set to RSA_2048. For the settings of the other parameters, see Creating a Key.
Note:
TCR supports obtaining user keys in all regions of the KMS service. To reduce the cross-region communication overhead, it is recommended that the KMS user key and the image repository instance be located in the same region.
Authorizing TCR to use the KMS key
To enable TCR to read the asymmetric signature verification key under your account, you need to configure a policy as follows under your account:
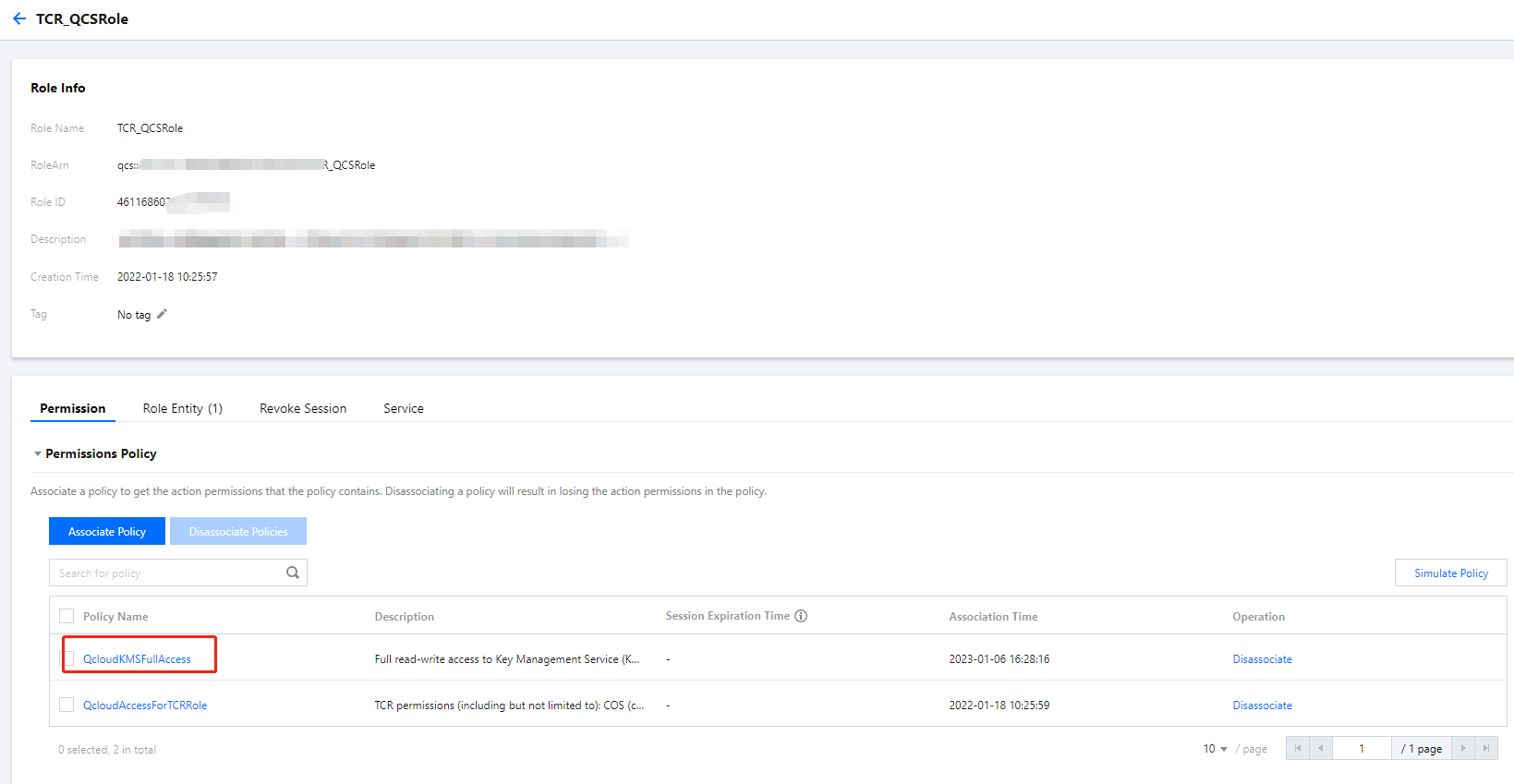
Log in to the CAM console.
On the Role page, click TCR_QCSRole.
On the TCR_QCSRole details page, associate the preset policy QcloudKMSFullAccess.
Creating an image signing policy
Log in to the TCR console.
On the instance management page, select a target image repository instance.
Select Image Security in the left sidebar to go to the image signing details page.
Click Create. In the signing policy creation window that pops up, set parameters as instructed.
Policy Name: Image signing policy name. The value must be 2 to 50 characters in length and can contain only lowercase letters, numbers, and separators, including periods (.), underscores (_), hyphens (-), and slashes (/). It can neither start or end with a separator nor contain consecutive separators.
Namespace: Namespace where the image signing policy takes effect. Only one signing policy is supported per namespace.
KMS Key: KMS customer managed CMK that supports signing. Only a key that is used for RSA2048 asymmetric key verification can be loaded.
Domain Name: Domain name used to access the repository instance service.
Click OK.
Note:- Once created, the signing policy takes effect for new images immediately. That is, when an image is pushed to the repository, it will be automatically signed according to the matched signing policy.
- An enabled signing policy does not take effect for images that already exist in the repository. For existing images, you need to manually trigger signing on the Image Repository > Tag Management page in the console.
Viewing image signing status
You can check whether the signing policy is enabled on the Namespace page.
You can check whether the signing policy is enabled for images on the Image Repository > Tag Management page. For images that have been pushed to the image repository before the signing policy is enabled, you can manually trigger signing in the Operation column.
Deleting an image signing policy
On the Image Signature page, select the signing policy to delete and click Delete. In the window that pops up, click OK.
Note:
Deleting the signing policy will also delete the image signing information in the existing namespace, which may cause signature verification failure.

 Yes
Yes
 No
No
Was this page helpful?