- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Billing Overview
- Basic Service Fees
- Value-added Service Fees
- Related Tencent Cloud Services
- Extra Package Description (Prepaid)
- Subscriptions
- Renewals
- Overdue and Expiration Policies
- Refund Policy
- Usage Cap Policy
- EdgeOne Plan Upgrade Guide
- Comparison of EdgeOne Plans
- About "clean traffic" billing instructions
- Getting Started
- Domain Service
- Site Acceleration
- Origin Configuration
- Edge Functions
- Overview
- Getting Started
- Operation Guide
- Runtime APIs
- Sample Functions
- Returning an HTML Page
- Returning a JSON Object
- Fetch Remote Resources
- Authenticating a Request Header
- Modifying a Response Header
- Performing an A/B Test
- Setting Cookies
- Performing Redirect Based on the Request Location
- Using the Cache API
- Caching POST Requests
- Responding in Streaming Mode
- Merging Resources and Responding in Streaming Mode
- Protecting Data from Tampering
- Rewriting a m3u8 File and Configuring Authentication
- Adaptive Image Resize
- Image Adaptive WebP
- Custom Referer Anti-leeching
- Remote Authentication
- HMAC Digital Signature
- Naming a Downloaded File
- Obtaining Client IP Address
- Best Practices
- Security Protection
- Overview
- DDoS Protection
- DDoS Protection Overview
- Exclusive DDoS Protection Usage
- Configuration of Exclusive DDoS protection Rules
- Web Protection
- Bot Management
- Rules Template
- IP and IP Segment Grouping
- Origin Protection
- Alarm Notification
- Rule Engine
- L4 Proxy
- Data Analysis&Log Service
- Tool Guide
- Best Practices
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Site APIs
- Acceleration Domain Management APIs
- Site Acceleration Configuration APIs
- Alias Domain APIs
- Security Configuration APIs
- Layer 4 Application Proxy APIs
- CreateL4Proxy
- ModifyL4Proxy
- ModifyL4ProxyStatus
- DescribeL4Proxy
- DeleteL4Proxy
- CreateL4ProxyRules
- ModifyL4ProxyRules
- ModifyL4ProxyRulesStatus
- DescribeL4ProxyRules
- DeleteL4ProxyRules
- CreateApplicationProxy
- ModifyApplicationProxy
- ModifyApplicationProxyStatus
- DescribeApplicationProxies
- DeleteApplicationProxy
- CreateApplicationProxyRule
- ModifyApplicationProxyRule
- ModifyApplicationProxyRuleStatus
- DeleteApplicationProxyRule
- Content Management APIs
- Data Analysis APIs
- Log Service APIs
- Billing APIs
- Certificate APIs
- Load Balancing APIs
- Diagnostic Tool APIs
- Version Management APIs
- Data Types
- Error Codes
- FAQs
- Agreements
- TEO Policy
- Contact Us
- Glossary
- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Billing Overview
- Basic Service Fees
- Value-added Service Fees
- Related Tencent Cloud Services
- Extra Package Description (Prepaid)
- Subscriptions
- Renewals
- Overdue and Expiration Policies
- Refund Policy
- Usage Cap Policy
- EdgeOne Plan Upgrade Guide
- Comparison of EdgeOne Plans
- About "clean traffic" billing instructions
- Getting Started
- Domain Service
- Site Acceleration
- Origin Configuration
- Edge Functions
- Overview
- Getting Started
- Operation Guide
- Runtime APIs
- Sample Functions
- Returning an HTML Page
- Returning a JSON Object
- Fetch Remote Resources
- Authenticating a Request Header
- Modifying a Response Header
- Performing an A/B Test
- Setting Cookies
- Performing Redirect Based on the Request Location
- Using the Cache API
- Caching POST Requests
- Responding in Streaming Mode
- Merging Resources and Responding in Streaming Mode
- Protecting Data from Tampering
- Rewriting a m3u8 File and Configuring Authentication
- Adaptive Image Resize
- Image Adaptive WebP
- Custom Referer Anti-leeching
- Remote Authentication
- HMAC Digital Signature
- Naming a Downloaded File
- Obtaining Client IP Address
- Best Practices
- Security Protection
- Overview
- DDoS Protection
- DDoS Protection Overview
- Exclusive DDoS Protection Usage
- Configuration of Exclusive DDoS protection Rules
- Web Protection
- Bot Management
- Rules Template
- IP and IP Segment Grouping
- Origin Protection
- Alarm Notification
- Rule Engine
- L4 Proxy
- Data Analysis&Log Service
- Tool Guide
- Best Practices
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Site APIs
- Acceleration Domain Management APIs
- Site Acceleration Configuration APIs
- Alias Domain APIs
- Security Configuration APIs
- Layer 4 Application Proxy APIs
- CreateL4Proxy
- ModifyL4Proxy
- ModifyL4ProxyStatus
- DescribeL4Proxy
- DeleteL4Proxy
- CreateL4ProxyRules
- ModifyL4ProxyRules
- ModifyL4ProxyRulesStatus
- DescribeL4ProxyRules
- DeleteL4ProxyRules
- CreateApplicationProxy
- ModifyApplicationProxy
- ModifyApplicationProxyStatus
- DescribeApplicationProxies
- DeleteApplicationProxy
- CreateApplicationProxyRule
- ModifyApplicationProxyRule
- ModifyApplicationProxyRuleStatus
- DeleteApplicationProxyRule
- Content Management APIs
- Data Analysis APIs
- Log Service APIs
- Billing APIs
- Certificate APIs
- Load Balancing APIs
- Diagnostic Tool APIs
- Version Management APIs
- Data Types
- Error Codes
- FAQs
- Agreements
- TEO Policy
- Contact Us
- Glossary
Overview
Token authentication is a simple and reliable access control strategy that verifies URL access through authentication rules, effectively preventing malicious brushing of site resources. The usage of this function requires the cooperation of the client and EdgeOne. The client is responsible for initiating encrypted URL requests, and EdgeOne is responsible for verifying the legality of the URL based on pre-set rules.
Function principle
The implementation of Token authentication mainly consists of the following two parts:
Client: Initiate the authentication URL request based on the authentication rules (including authentication algorithm, key).
EdgeOne node: Verify the authentication information (md5 string + timestamp) in the authentication URL. When the verification is passed, the access request will be considered as a valid request, and the node will respond normally. If the verification fails, the node will reject the access and directly return 403.
Token authentication URL generation and verification tool
EdgeOne provides a generation tool and verification tool for Token authentication URLs. Developers can use this tool to quickly and accurately generate and verify anti-leeching URLs that meet the requirements.
Directions
1. Log in to the EdgeOne console, click on the site list in the left menu bar, and click on the site to be configured in the site list.
2. On the site details page, click on the rule engine.
3. On the rule engine management page, click Create Rule to enter the editing page of the new rule.
4. On the rule editing page, set the matching conditions that trigger this rule.
5. Click Operation > Select Box, and select Token Authentication in the pop-up operation list. The parameter configuration instructions are as follows:
Parameter | Description |
Method | Currently, 4 authentication signature calculation methods are supported. Please choose the appropriate method based on the access URL format. For details, please refer to the authentication method. |
Primary key | The primary password, consisting of 6-40 uppercase and lowercase English letters or numbers. |
Secondary key | The secondary password, consisting of 6-40 uppercase and lowercase English letters or numbers. |
Authentication parameter | An authentication parameter must be between 1-100 characters and contains letters, numbers and underscores. The parameter value will be authenticated by nodes. |
Validity period | Validity period of the authentication URL (1-630720000 seconds). It determines whether a client request is valid: If the time "timestamp + validity period" is reached, the request is considered expired and a 403 is returned. If the current time does not exceed the "timestamp + valid duration" time, the request is not expired and continues to verify the md5 string. |
Authentication Methods
Method A
Authentication URL format
http://Hostname/Filename?sign=timestamp-rand-uid-md5hash
Field description
Field | Description |
Hostname | Site domain name. |
Path | Path to access the resource, which must start with "/". |
sign | Custom name of the authentication parameter. |
timestamp | A positive decimal integer, indicating the number of seconds elapsed since 00:00:00, January 1, 1970 at UTC. It does not change regardless of your time zone. |
rand | Random string, which contains letters and digits. Length: 0–100. |
uid | User ID (not in use), which defaults to 0. |
md5hash | A fixed-length 32-bit string calculated with the MD5 algorithm: Authentication algorithm: MD5 (Path-timestamp-rand-uid-key). Authentication logic: When receiving a valid request, the node starts comparing this string value with the md5hash value in the request URL. If they match, the node will respond to the request after it is authenticated, otherwise it returns a 403. |
Method B
Authentication URL format
http://Hostname/timestamp/md5hash/Filename
Field description
Field | Description |
Hostname | Site domain name. |
Path | Path to access the resource, which must start with "/". |
timestamp | Timestamp. Format: YYYYMMDDHHMM (represented in UTC+8), such as 201807301000. |
md5hash | A fixed-length 32-bit string calculated with the MD5 algorithm: Authentication algorithm: MD5 (key + timestamp + Path). Authentication logic: When receiving a valid request, the node starts comparing this string value with the md5hash value in the request URL. If they match, the node will respond to the request after it is authenticated, otherwise it returns a 403. |
Method C
Authentication URL format
http://Hostname/md5hash/timestamp/Filename
Field description
Field | Description |
Hostname | Site domain name. |
Path | Path to access the resource, which must start with "/". |
timestamp | Unix timestamp. Format: A positive hex integer, indicating the number of seconds elapsed since 00:00:00, January 1, 1970 at UTC. It does not change regardless of your time zone. |
md5hash | A fixed-length 32-bit string calculated with the MD5 algorithm: Authentication algorithm: MD5 (key + Path + timestamp). Note that you should remove the identifier 0x from a hex timestamp before calculation. Authentication logic: When receiving a valid request, the node starts comparing this string value with the md5hash value in the request URL. If they match, the node will respond to the request after it is authenticated, otherwise it returns a 403. |
Method D
Authentication URL format
http://Hostname/Filename?sign=md5hash&t=timestamp
Field description
Field | Description |
Hostname | Site domain name. |
Path | Path to access the resource, which must start with "/". |
sign | Custom name of the authentication parameter. |
t | Custom name of the timestamp parameter. |
timestamp | Unix timestamp. Format: A positive decimal/hex integer, indicating the number of seconds elapsed since 00:00:00, January 1, 1970 at UTC. It does not change regardless of your time zone. |
md5hash | A fixed-length 32-bit string calculated with the MD5 algorithm: Authentication algorithm: MD5 (key + Path + timestamp). Note that you should remove the identifier 0x from a hex timestamp before calculation. Authentication logic: When receiving a valid request, the node starts comparing this string value with the md5hash value in the request URL. If they match, the node will respond to the request after it is authenticated, otherwise it returns a 403. |
Configuration Sample
The following configuration sample shows how to authenticate a request for
http://www.example.com/test.jpg with Method A: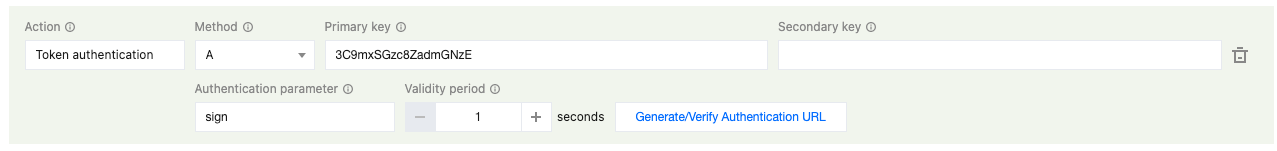
Getting authentication parameters
Path:
/foo.jpgtimestamp:
1647311432. The timestamp is returned as a 10-digit positive decimal integer indicating that the authentication URL is generated at 10:30:32, March 15, 2022 (UTC+8).rand:
J0ehJ1Gegyia2nD2HstLvwuid:
0key:
3C9mxSGzc8ZadmGNzEmd5hash: MD5 (Path-timestamp-rand-uid-key) = MD5 (
/foo.jpg-1647311432-J0ehJ1Gegyia2nD2HstLvw-0-3C9mxSGzc8ZadmGNzE) = ecce3150cbdaac83b116d937777ca77fGenerating an authentication URL
http://www.example.com/foo.jpg?sign=1647311432-J0ehJ1Gegyia2nD2HstLvw-0-ecce3150cbdaac83b116d937777ca77fAuthenticating the request
After the request is initiated via an encrypted URL, the node parses the value of the "timestamp" parameter from the URL to determine whether the request is valid:
If the time "timestamp + validity period" is reached, the request is considered expired and a 403 is returned.
If the time "timestamp + validity period" is not reached, the request is considered valid and will be authenticated.
The node compares the calculated
md5hash value with the md5hash value in the request URL. If they match, the node will respond to the request after it is authenticated, otherwise it returns a 403.Must-knows
1. After Authentication is passed, the node will automatically ignore the Authentication-related parameters in the URL to improve the Cache hit rate and reduce the amount of origin-pull.
2. The origin-pull request URL cannot contain any Chinese characters.

 Yes
Yes
 No
No
Was this page helpful?