- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Billing Overview
- Basic Service Fees
- Value-added Service Fees
- Related Tencent Cloud Services
- Extra Package Description (Prepaid)
- Subscriptions
- Renewals
- Overdue and Expiration Policies
- Refund Policy
- Usage Cap Policy
- EdgeOne Plan Upgrade Guide
- Comparison of EdgeOne Plans
- About "clean traffic" billing instructions
- Getting Started
- Domain Service
- Site Acceleration
- Origin Configuration
- Edge Functions
- Overview
- Getting Started
- Operation Guide
- Runtime APIs
- Sample Functions
- Returning an HTML Page
- Returning a JSON Object
- Fetch Remote Resources
- Authenticating a Request Header
- Modifying a Response Header
- Performing an A/B Test
- Setting Cookies
- Performing Redirect Based on the Request Location
- Using the Cache API
- Caching POST Requests
- Responding in Streaming Mode
- Merging Resources and Responding in Streaming Mode
- Protecting Data from Tampering
- Rewriting a m3u8 File and Configuring Authentication
- Adaptive Image Resize
- Image Adaptive WebP
- Custom Referer Anti-leeching
- Remote Authentication
- HMAC Digital Signature
- Naming a Downloaded File
- Obtaining Client IP Address
- Best Practices
- Security Protection
- Overview
- DDoS Protection
- DDoS Protection Overview
- Exclusive DDoS Protection Usage
- Configuration of Exclusive DDoS protection Rules
- Web Protection
- Bot Management
- Rules Template
- IP and IP Segment Grouping
- Origin Protection
- Alarm Notification
- Rule Engine
- L4 Proxy
- Data Analysis&Log Service
- Tool Guide
- Best Practices
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Site APIs
- Acceleration Domain Management APIs
- Site Acceleration Configuration APIs
- Alias Domain APIs
- Security Configuration APIs
- Layer 4 Application Proxy APIs
- CreateL4Proxy
- ModifyL4Proxy
- ModifyL4ProxyStatus
- DescribeL4Proxy
- DeleteL4Proxy
- CreateL4ProxyRules
- ModifyL4ProxyRules
- ModifyL4ProxyRulesStatus
- DescribeL4ProxyRules
- DeleteL4ProxyRules
- CreateApplicationProxy
- ModifyApplicationProxy
- ModifyApplicationProxyStatus
- DescribeApplicationProxies
- DeleteApplicationProxy
- CreateApplicationProxyRule
- ModifyApplicationProxyRule
- ModifyApplicationProxyRuleStatus
- DeleteApplicationProxyRule
- Content Management APIs
- Data Analysis APIs
- Log Service APIs
- Billing APIs
- Certificate APIs
- Load Balancing APIs
- Diagnostic Tool APIs
- Version Management APIs
- Data Types
- Error Codes
- FAQs
- Agreements
- TEO Policy
- Contact Us
- Glossary
- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Billing Overview
- Basic Service Fees
- Value-added Service Fees
- Related Tencent Cloud Services
- Extra Package Description (Prepaid)
- Subscriptions
- Renewals
- Overdue and Expiration Policies
- Refund Policy
- Usage Cap Policy
- EdgeOne Plan Upgrade Guide
- Comparison of EdgeOne Plans
- About "clean traffic" billing instructions
- Getting Started
- Domain Service
- Site Acceleration
- Origin Configuration
- Edge Functions
- Overview
- Getting Started
- Operation Guide
- Runtime APIs
- Sample Functions
- Returning an HTML Page
- Returning a JSON Object
- Fetch Remote Resources
- Authenticating a Request Header
- Modifying a Response Header
- Performing an A/B Test
- Setting Cookies
- Performing Redirect Based on the Request Location
- Using the Cache API
- Caching POST Requests
- Responding in Streaming Mode
- Merging Resources and Responding in Streaming Mode
- Protecting Data from Tampering
- Rewriting a m3u8 File and Configuring Authentication
- Adaptive Image Resize
- Image Adaptive WebP
- Custom Referer Anti-leeching
- Remote Authentication
- HMAC Digital Signature
- Naming a Downloaded File
- Obtaining Client IP Address
- Best Practices
- Security Protection
- Overview
- DDoS Protection
- DDoS Protection Overview
- Exclusive DDoS Protection Usage
- Configuration of Exclusive DDoS protection Rules
- Web Protection
- Bot Management
- Rules Template
- IP and IP Segment Grouping
- Origin Protection
- Alarm Notification
- Rule Engine
- L4 Proxy
- Data Analysis&Log Service
- Tool Guide
- Best Practices
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Site APIs
- Acceleration Domain Management APIs
- Site Acceleration Configuration APIs
- Alias Domain APIs
- Security Configuration APIs
- Layer 4 Application Proxy APIs
- CreateL4Proxy
- ModifyL4Proxy
- ModifyL4ProxyStatus
- DescribeL4Proxy
- DeleteL4Proxy
- CreateL4ProxyRules
- ModifyL4ProxyRules
- ModifyL4ProxyRulesStatus
- DescribeL4ProxyRules
- DeleteL4ProxyRules
- CreateApplicationProxy
- ModifyApplicationProxy
- ModifyApplicationProxyStatus
- DescribeApplicationProxies
- DeleteApplicationProxy
- CreateApplicationProxyRule
- ModifyApplicationProxyRule
- ModifyApplicationProxyRuleStatus
- DeleteApplicationProxyRule
- Content Management APIs
- Data Analysis APIs
- Log Service APIs
- Billing APIs
- Certificate APIs
- Load Balancing APIs
- Diagnostic Tool APIs
- Version Management APIs
- Data Types
- Error Codes
- FAQs
- Agreements
- TEO Policy
- Contact Us
- Glossary
HTTPS Configuration
Last updated: 2022-10-18 10:30:12
Log in to the EdgeOne console and click Site Acceleration > HTTPS configuration on the left sidebar.
On the HTTPS configuration page, select the target site and configure the following HTTPS items for site acceleration:
Forced HTTPS
In the forced HTTPS module, click  to forcibly redirect all edge HTTP requests to HTTPS through 301/302. It is disabled by default.
to forcibly redirect all edge HTTP requests to HTTPS through 301/302. It is disabled by default.
Note:After this feature is enabled, all requests will be transferred over HTTPS. Make sure that certificates of service-providing subdomains have been deployed in EdgeOne.
Origin-Pull HTTPS
In the origin-pull HTTPS module, click Edit, select the origin-pull encryption mode (i.e., protocol used for origin-pull), and click Save.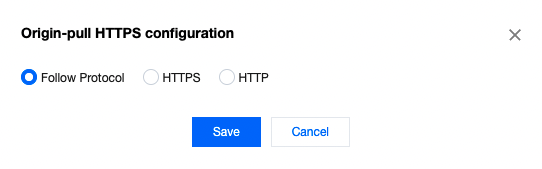
Parameter description:
- Follow protocol (default): The origin-pull protocol follows the request protocol. For example, if the request uses HTTP, origin-pull will also use HTTP.
- HTTP: All origin-pull requests use the HTTP protocol.
- HTTPS: All origin-pull requests use the HTTPS protocol.
HTTP Strict Transport Security (HSTS)
- In the HSTS module, click Enable HSTS, configure relevant parameters, and click OK.
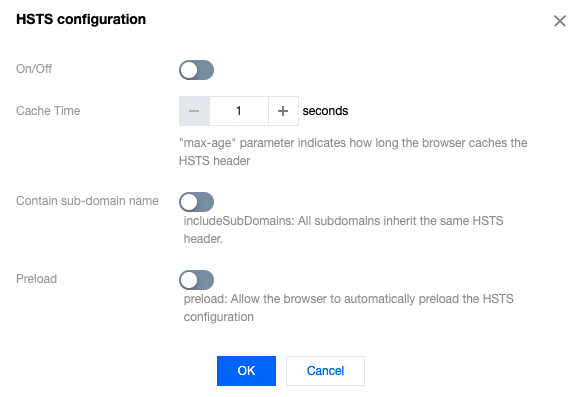
Parameter description:
- Default status: It is disabled by default. To use the HSTS feature, you need to enable it.
- Cache time: Set the HSTS header validity period in seconds, during which browsers always initiate requests over HTTPS. The value range is 1–31536000.
- Include subdomain: If it is enabled, HSTS will take effect for the current domain and its subdomains.
- Preload: If it is enabled, browsers will automatically load the HSTS configuration in advance to avoid the attack risks of the first HTTP request. This feature can take effect only if you add the domain to the HSTS preload list in browsers first.
- After HSTS is configured, the
Strict-Transport-Securityheader will be added to the EdgeOne cache node responses to force clients such as browsers to establish connections to edge nodes over HTTPS for global website encryption.
HTTPS header format
Strict-Transport-Security: max-age=expireTime [; includeSubDomains] [; preload]Field description
- max-age: HSTS header validity period in seconds, during which browsers always initiate requests over HTTPS.
- includeSubDomains: It is an optional field. If it is enabled, HSTS will take effect for the current domain and its subdomains.
- preload: It is an optional field. If it is enabled, browsers will automatically load the HSTS configuration in advance to avoid the attack risks of the first HTTP request. This feature can take effect only if you add the domain to the HSTS preload list in browsers first.
Note:
- Before enabling HSTS, make sure that domain certificates have been deployed to respond to HTTPS requests normally.
- We recommend you also enable forced HTTPS when enabling HSTS; otherwise, if requests use HTTP, browsers won't execute the HSTS configuration.
- The value range of
max-ageis 1–31536000 seconds.
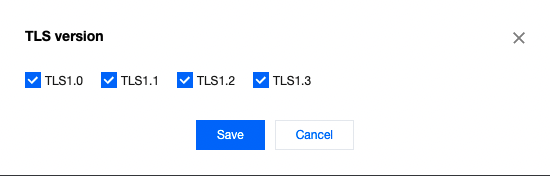
TLS version
In the TLS version module, click Edit, select the target version, and click Save.
Note:Only HTTPS links on enabled TLS versions are allowed. Available TLS versions are 1.0–1.3. You can enable a single version or a series of consecutive versions.
OCSP stapling
In the OCSP stapling module, the cached OCSP response will be sent during TLS handshake to improve the handshake efficiency. After you click  to enable OCSP stapling, cache nodes will cache the OCSP response for clients to verify it, and clients won't need to send query requests to certificate authorities (CAs), which accelerates TLS handshakes.
to enable OCSP stapling, cache nodes will cache the OCSP response for clients to verify it, and clients won't need to send query requests to certificate authorities (CAs), which accelerates TLS handshakes.

 Yes
Yes
 No
No
Was this page helpful?