- Release Notes and Announcements
- CLB Release Notes
- [April 15, 2024] Domain Name Upgrade for Domain Name-based Public Network CLB
- [July 25, 2023] Adding Rate Limits on Shared CLB Instances
- [July 3, 2023] CLB API Authentication Upgrade
- [June 9, 2023] Adjusting the Grace Period for Pay-as-you-go CLB Instances
- [March 6, 2023] Launching Domain Name-Based Public CLBs
- [Feb. 24, 2023] Changing Health Check Source IP to 100.64.0.0/10 IP Range
- [July 8, 2022] Classic CLB Upgrade Prompt
- 【October 20, 2021】Classic CLB End-of-Sale Notice
- 【April 27, 2021】Announcement on the Authentication Upgrade for Certain CLB APIs
- Product Introduction
- Purchase Guide
- Getting Started
- Directions
- CLB Instance
- Directions for Upgrading to Domain Name-Based CLB
- Creating CLB Instances
- Creating an IPv6 CLB Instance
- Creating IPv6 NAT64 CLB Instances
- Creating an Anycast CLB Instance
- Configure CLB Forwarding Domain Name
- Configuring CLB Security Group
- Binding Private Network CLB to EIP
- Enabling or Disabling a CLB Instance
- Cloning CLB Instances
- Exporting CLB Instances
- Upgrade to a LCU-supported instances
- Adjusting Specification of LCU-supported CLBs
- Deleting CLB Instances
- Releasing Idle CLB Instances
- Configuring Deletion Protection
- Adjusting Instance Public Network Configurations
- CLB Listener
- CLB Listener Overview
- Configuring TCP Listener
- Configuring a UDP Listener
- Configuring TCP SSL Listener
- Configuring a QUIC Listener
- Configuring an HTTP Listener
- Configuring HTTPS Listener
- Load Balancing Methods
- Session Persistence
- Layer-7 Redirection Configuration
- Layer-7 Custom Configuration
- Layer-7 Domain Name Forwarding and URL Rules
- Using QUIC Protocol on CLB
- SNI Support for Binding Multiple Certificates to a CLB Instance
- Configuring gRPC Support for Layer-7 Protocols
- Real Server
- Health Check
- Certificate Management
- Log Management
- Monitoring and Alarm
- Cloud Access Management
- Classic CLB
- CLB Instance
- Best Practices
- Enabling Gzip Compression & Testing
- HTTPS Forwarding Configurations
- Obtaining Real Client IPs
- Best Practices for Configuring Load Balancing Monitoring Alerts
- Implementing HA Across Multiple AZs
- Load Balancing Algorithm Selection and Weight Configuration Examples
- Configuring WAF protection for CLB listening domain names
- Ops Guide
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Instance APIs
- Listener APIs
- Backend Service APIs
- Target Group APIs
- Redirection APIs
- Other APIs
- ModifyLoadBalancersProject
- InquiryPriceCreateLoadBalancer
- InquiryPriceModifyLoadBalancer
- InquiryPriceRenewLoadBalancer
- DescribeLoadBalancerTraffic
- DescribeTaskStatus
- DescribeClsLogSet
- CreateClsLogSet
- CreateTopic
- CreateLoadBalancerSnatIps
- DeleteLoadBalancerSnatIps
- SetLoadBalancerSecurityGroups
- SetSecurityGroupForLoadbalancers
- ReplaceCertForLoadBalancers
- DescribeLoadBalancerListByCertId
- SetLoadBalancerClsLog
- DescribeQuota
- DescribeResources
- Classic CLB APIs
- Load Balancing APIs
- Data Types
- Error Codes
- CLB API 2017
- FAQs
- Service Level Agreement
- Contact Us
- Glossary
- Release Notes and Announcements
- CLB Release Notes
- [April 15, 2024] Domain Name Upgrade for Domain Name-based Public Network CLB
- [July 25, 2023] Adding Rate Limits on Shared CLB Instances
- [July 3, 2023] CLB API Authentication Upgrade
- [June 9, 2023] Adjusting the Grace Period for Pay-as-you-go CLB Instances
- [March 6, 2023] Launching Domain Name-Based Public CLBs
- [Feb. 24, 2023] Changing Health Check Source IP to 100.64.0.0/10 IP Range
- [July 8, 2022] Classic CLB Upgrade Prompt
- 【October 20, 2021】Classic CLB End-of-Sale Notice
- 【April 27, 2021】Announcement on the Authentication Upgrade for Certain CLB APIs
- Product Introduction
- Purchase Guide
- Getting Started
- Directions
- CLB Instance
- Directions for Upgrading to Domain Name-Based CLB
- Creating CLB Instances
- Creating an IPv6 CLB Instance
- Creating IPv6 NAT64 CLB Instances
- Creating an Anycast CLB Instance
- Configure CLB Forwarding Domain Name
- Configuring CLB Security Group
- Binding Private Network CLB to EIP
- Enabling or Disabling a CLB Instance
- Cloning CLB Instances
- Exporting CLB Instances
- Upgrade to a LCU-supported instances
- Adjusting Specification of LCU-supported CLBs
- Deleting CLB Instances
- Releasing Idle CLB Instances
- Configuring Deletion Protection
- Adjusting Instance Public Network Configurations
- CLB Listener
- CLB Listener Overview
- Configuring TCP Listener
- Configuring a UDP Listener
- Configuring TCP SSL Listener
- Configuring a QUIC Listener
- Configuring an HTTP Listener
- Configuring HTTPS Listener
- Load Balancing Methods
- Session Persistence
- Layer-7 Redirection Configuration
- Layer-7 Custom Configuration
- Layer-7 Domain Name Forwarding and URL Rules
- Using QUIC Protocol on CLB
- SNI Support for Binding Multiple Certificates to a CLB Instance
- Configuring gRPC Support for Layer-7 Protocols
- Real Server
- Health Check
- Certificate Management
- Log Management
- Monitoring and Alarm
- Cloud Access Management
- Classic CLB
- CLB Instance
- Best Practices
- Enabling Gzip Compression & Testing
- HTTPS Forwarding Configurations
- Obtaining Real Client IPs
- Best Practices for Configuring Load Balancing Monitoring Alerts
- Implementing HA Across Multiple AZs
- Load Balancing Algorithm Selection and Weight Configuration Examples
- Configuring WAF protection for CLB listening domain names
- Ops Guide
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Instance APIs
- Listener APIs
- Backend Service APIs
- Target Group APIs
- Redirection APIs
- Other APIs
- ModifyLoadBalancersProject
- InquiryPriceCreateLoadBalancer
- InquiryPriceModifyLoadBalancer
- InquiryPriceRenewLoadBalancer
- DescribeLoadBalancerTraffic
- DescribeTaskStatus
- DescribeClsLogSet
- CreateClsLogSet
- CreateTopic
- CreateLoadBalancerSnatIps
- DeleteLoadBalancerSnatIps
- SetLoadBalancerSecurityGroups
- SetSecurityGroupForLoadbalancers
- ReplaceCertForLoadBalancers
- DescribeLoadBalancerListByCertId
- SetLoadBalancerClsLog
- DescribeQuota
- DescribeResources
- Classic CLB APIs
- Load Balancing APIs
- Data Types
- Error Codes
- CLB API 2017
- FAQs
- Service Level Agreement
- Contact Us
- Glossary
You can create a TCP SSL listener for a Cloud Load Balancer (CLB) instance to forward encrypted TCP requests from the client. TCP SSL is applicable to scenarios where ultra-high performance and large-scale TLS offloading are required. Real servers bound to the TCP SSL listener can directly obtain the real client IP address.
Note:
TCP SSL listeners currently support CLB instances but not classic CLB instances.
Use Cases
TCP SSL is suitable for scenarios that have high requirements for security when the TCP protocol is used:
TCP SSL listeners support configuration of certificates to block unauthorized access.
Unified certificate management is supported for CLB to implement decryption.
One-way authentication and mutual authentication are supported.
A real server can directly obtain the client IP address.
Prerequisites
Directions
Step 1. Configure a listener
1. Log in to the CLB console and click Instance management in the left sidebar.
2. Select your region in the top-left corner of the CLB instance list and click Configure listener in the Operation column of the target instance.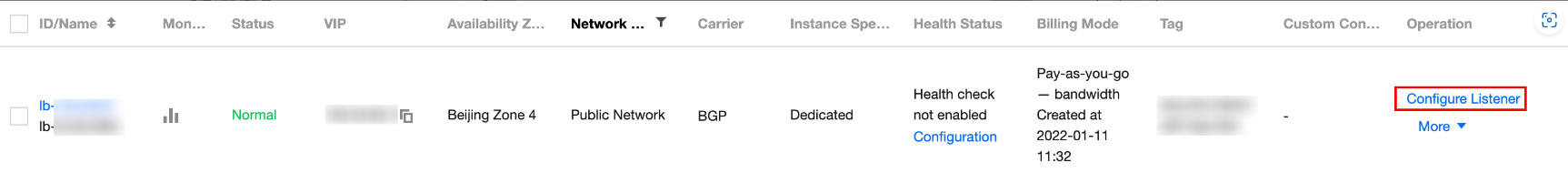

3. Under TCP/UDP/TCP SSL/QUIC listener, click Create and configure the TCP SSL listener in the pop-up window.
3.1 Configure basic parameters
Parameter | Description | Example |
Name | Listener name. | test-tcpssl-9000 |
Listening protocol and port | Listening protocol: In this case, select TCP SSL.Listening port: The port used to receive requests and forward them to the real server. The port number ranges from 1 to 65535. A listening port must be unique in the same CLB instance. | TCP SSL:9000 |
SSL parsing | One-way authentication and mutual authentication are supported. | One-way authentication |
Server certificate | You can select an existing certificate in the SSL Certificate Service console or create a certificate. | Select an existing certificate. |
Balancing method | CLB supports two scheduling algorithms for TCP SSL listeners: weighted round robin (WRR) and weighted least connections (WLC). WRR: Requests are distributed to real servers in sequence based on their weights. This algorithm performs scheduling based on the number of new connections. Servers with higher weights are more likely to be scheduled and servers with the same weight process the same number of connections. WLC: Loads of servers are estimated based on the number of active connections to the servers. This algorithm performs scheduling based on server loads and weights. For servers with the same weight, those have less loads are more likely to be scheduled. | WRR |
3.2 Configure health check
3.3 Configure session persistence
TCP SSL listeners don't support session persistence currently.
Step 2. Bind a real server
1. On the Listener management page, click the created listener
TCP SSL:9000 to view the bound real servers on the right of the listener.2. Click Bind, select the target real server, and configure the server port and weight in the pop-up window.
Note:
If you set Default port first and then select real servers, the port of every real server is the default port.
Step 3. Configure a security group (optional)
You can configure a CLB security group to isolate public network traffic. For more information, see Configuring a CLB Security Group.
Step 4. Modify or delete a listener (optional)
If you need to modify or delete a created listener, click the listener on the Listener management page and click 


 Yes
Yes
 No
No
Was this page helpful?