- Updates and Announcements
- Product Introduction
- Differences Between the Old and New Versions
- Comparison of Anti-DDoS Protection Schemes
- Purchase Guide
- Getting Started
- Operation Guide
- Best Practice
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Anti-DDoS Pro Instance List APIs
- Anti-DDoS Advanced Instance APIs
- Protection Configuration APIs
- ModifyPacketFilterConfig
- ModifyDDoSSpeedLimitConfig
- ModifyDDoSGeoIPBlockConfig
- DescribeListWaterPrintConfig
- DescribeListProtocolBlockConfig
- DescribeListProtectThresholdConfig
- DescribeListPacketFilterConfig
- DescribeListDDoSSpeedLimitConfig
- DescribeListDDoSGeoIPBlockConfig
- DescribeListDDoSAI
- DescribeListBlackWhiteIpList
- DescribeBlackWhiteIpList
- DeleteWaterPrintKey
- DeleteWaterPrintConfig
- DeletePacketFilterConfig
- DeleteDDoSSpeedLimitConfig
- DeleteDDoSGeoIPBlockConfig
- DeleteBlackWhiteIpList
- CreateWaterPrintKey
- CreateWaterPrintConfig
- CreateProtocolBlockConfig
- CreatePacketFilterConfig
- CreateDDoSSpeedLimitConfig
- CreateDDoSGeoIPBlockConfig
- CreateDDoSAI
- CreateBlackWhiteIpList
- SwitchWaterPrintConfig
- ModifyCcBlackWhiteIpList
- DescribeCcGeoIPBlockConfigList
- DescribeCcBlackWhiteIpList
- DeleteCcGeoIPBlockConfig
- DeleteCcBlackWhiteIpList
- CreateCcGeoIPBlockConfig
- CreateCcBlackWhiteIpList
- Intelligent Scheduling APIs
- Alarm Notification APIs
- Resource List APIs
- Connection Configuration APIs
- Statistical Report APIs
- Other APIs
- Data Types
- Error Codes
- FAQs
- Legacy Anti-DDoS Pro
- Anti-DDoS Basic
- Service Level Agreement
- Anti-DDoS Pro Policy
- Glossary
- Updates and Announcements
- Product Introduction
- Differences Between the Old and New Versions
- Comparison of Anti-DDoS Protection Schemes
- Purchase Guide
- Getting Started
- Operation Guide
- Best Practice
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Anti-DDoS Pro Instance List APIs
- Anti-DDoS Advanced Instance APIs
- Protection Configuration APIs
- ModifyPacketFilterConfig
- ModifyDDoSSpeedLimitConfig
- ModifyDDoSGeoIPBlockConfig
- DescribeListWaterPrintConfig
- DescribeListProtocolBlockConfig
- DescribeListProtectThresholdConfig
- DescribeListPacketFilterConfig
- DescribeListDDoSSpeedLimitConfig
- DescribeListDDoSGeoIPBlockConfig
- DescribeListDDoSAI
- DescribeListBlackWhiteIpList
- DescribeBlackWhiteIpList
- DeleteWaterPrintKey
- DeleteWaterPrintConfig
- DeletePacketFilterConfig
- DeleteDDoSSpeedLimitConfig
- DeleteDDoSGeoIPBlockConfig
- DeleteBlackWhiteIpList
- CreateWaterPrintKey
- CreateWaterPrintConfig
- CreateProtocolBlockConfig
- CreatePacketFilterConfig
- CreateDDoSSpeedLimitConfig
- CreateDDoSGeoIPBlockConfig
- CreateDDoSAI
- CreateBlackWhiteIpList
- SwitchWaterPrintConfig
- ModifyCcBlackWhiteIpList
- DescribeCcGeoIPBlockConfigList
- DescribeCcBlackWhiteIpList
- DeleteCcGeoIPBlockConfig
- DeleteCcBlackWhiteIpList
- CreateCcGeoIPBlockConfig
- CreateCcBlackWhiteIpList
- Intelligent Scheduling APIs
- Alarm Notification APIs
- Resource List APIs
- Connection Configuration APIs
- Statistical Report APIs
- Other APIs
- Data Types
- Error Codes
- FAQs
- Legacy Anti-DDoS Pro
- Anti-DDoS Basic
- Service Level Agreement
- Anti-DDoS Pro Policy
- Glossary
Operation Scenarios
Anti-DDoS Pro supports the CC protection function. When the HTTP request amount calculated by Anti-DDoS Pro exceeds the set HTTP Request Threshold, CC protection is automatically triggered. Meanwhile, Anti-DDoS Pro supports URL allowlist, IP allowlist, and IP blocklist policies:
- For URLs in the allowlist, their access requests do not require CC attack detection and can pass directly.
- For IPs in the allowlist, their HTTP access requests do not require CC attack detection and can pass directly.
- For IPs in the blocklist, their HTTP access request will be directly denied.
You can custom the protection policy according to the features and protection needs of your business to block CC attacks more accurately.
Directions
- Log in to Anti-DDoS Console and choose Anti-DDoS Pro -> Protection Configuration. On the CC Protection tab, select the target region and Anti-DDoS Pro instance to configure CC protection.
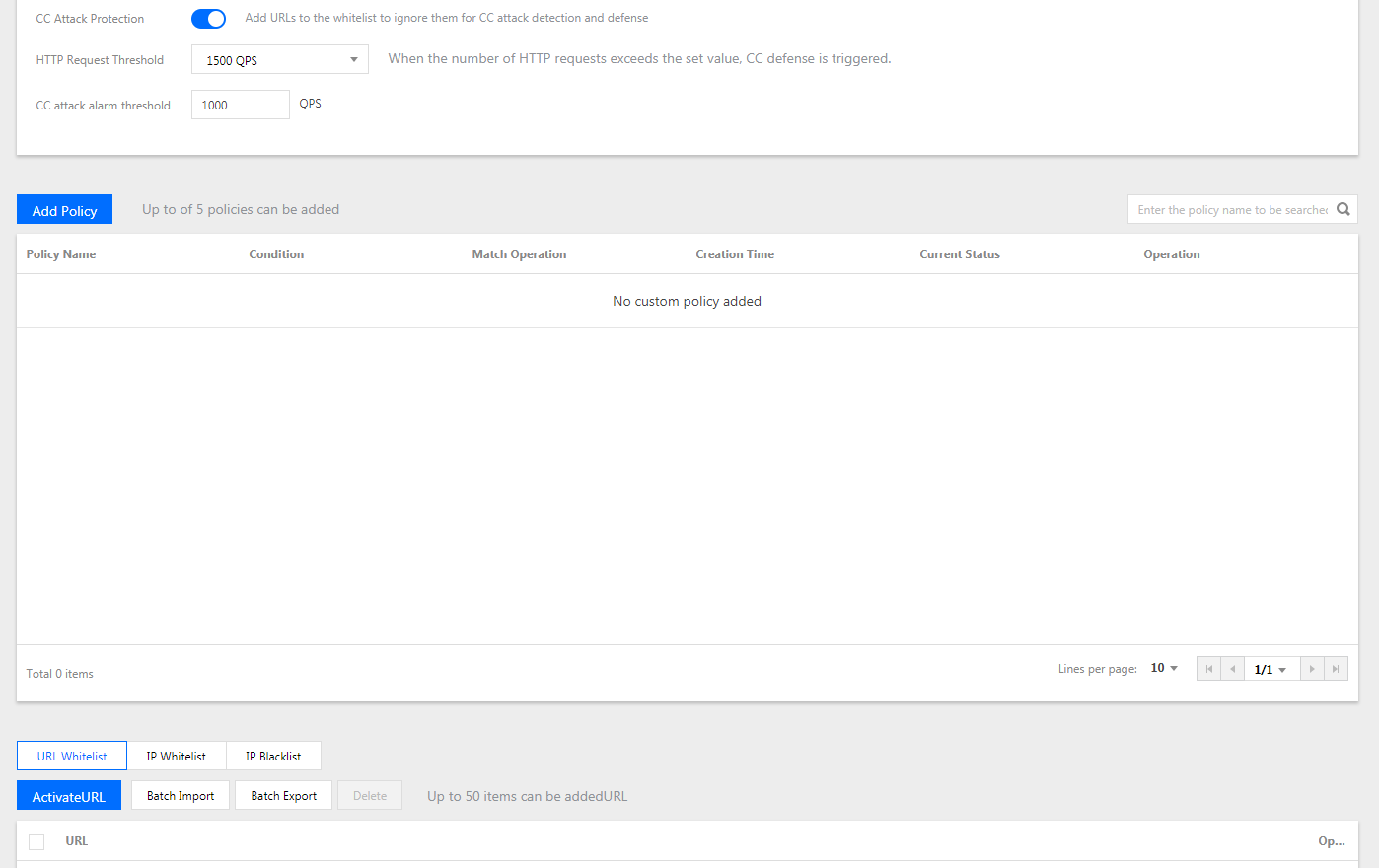
- Click
 next to CC Protection to enable it.
next to CC Protection to enable it.
- By default, CC Protection is disabled.
- You can set the HTTP request amount threshold, custom CC protection policy and blocklist/allowlist when you enable CC protection.
- Click the drop-down list right to the HTTP Request Threshold to select a proper threshold.
- Click Add Access Control Policy, and then set the following parameters according to the actual business demand in the Add Access Control Policy pop-up box. Click OK to complete the configuration.
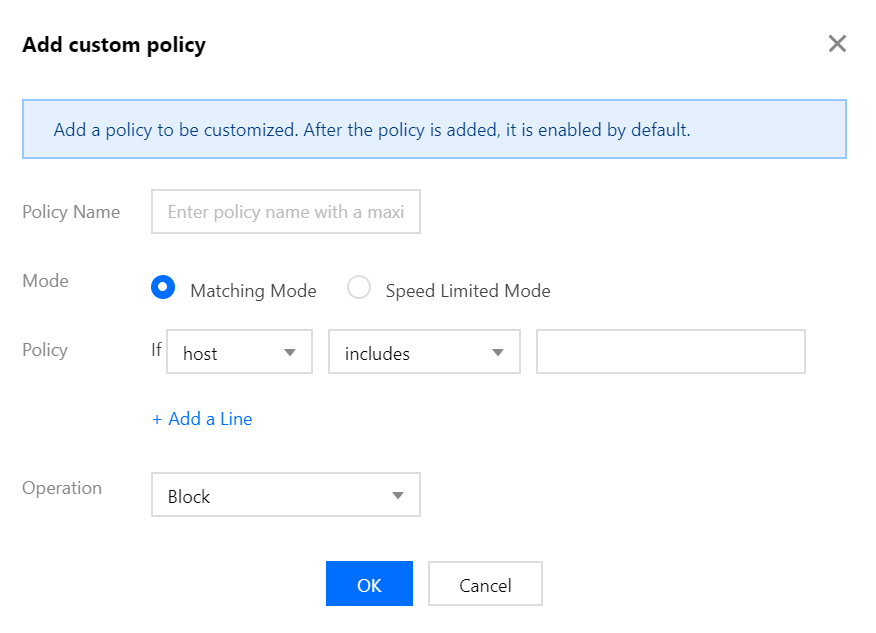
The custom policy takes effect only when Anti-DDoS Pro is under attack.
Match mode: Each custom policy may have up to 4 conditions for feature control, and these conditions have “and” relation, which means all conditions must be matched before the policy takes effect.
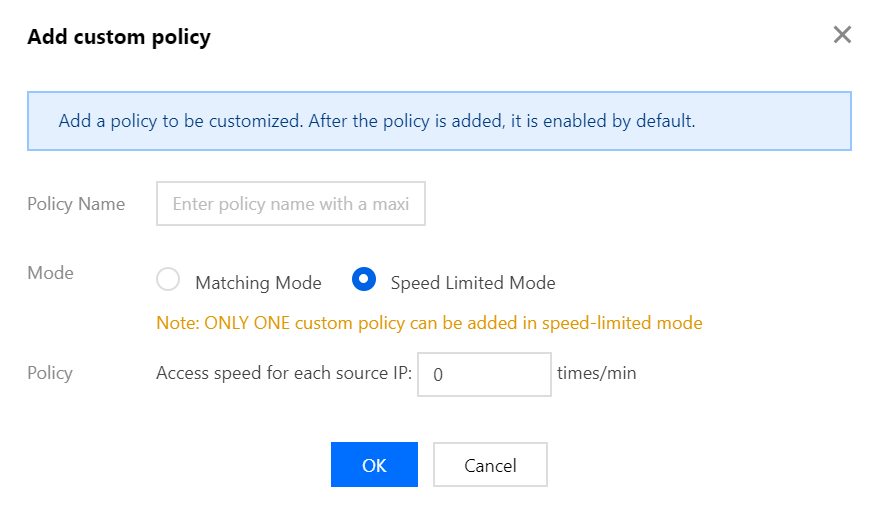
Speed limit mode: Each custom policy only allows for setting 1 policy condition.
Policy Name
Enter policy name, which consists of 1-20 characters. Character type is not restricted.Mode
Match Mode: When it detects requests matched the corresponding HTTP field, it will block the request or require human-machine recognition.
Speed Limit Mode: Limits the speed of source IP access.
Policy
When you select Match Mode, it supports a combination of multiple features such as
host,CGI,Referer, andUser-Agentfrom HTTP messages. The combination logic includes contain, not contain, and equal to. You can set up to 4 policy conditions for feature control as described below:Field Description Logic host Domain name of the access request contain, not contain, equal to CGI URL of the access request contain, not contain, equal to Referer Source website of the access request, which means at which webpage the access request is generated contain, not contain, equal to User-Agent Information like browser identifier of the requester client contain, not contain, equal to When you select Speed Limit Mode, you limit the speed of each source IP access. You are allowed to set only one policy condition.
- Click URL Allowlist, IP Allowlist, or IP Blocklist tab for blocklist/allowlist configuration. Addition and deletion are allowed.
When you add a URL to the Anti-DDoS Pro allowlist, the HTTP protocol header is optional. But Anti-DDoS Pro supports only HTTP protocol. Example:
http://test.com/index.phporwww.test.com/index.php.

 Yes
Yes
 No
No
Was this page helpful?