- Release Notes and Announcements
- Release Notes
- Announcements
- Announcement on Changing External Network Links
- Interface Authentication Upgrade Announcement
- Maintenance Time Change from Local Time to Beijing Time
- Account Type and Permission Changes
- Product Architecture Name Change
- Disk Storage Space Composition Change
- Ending Support for Classic Network [2022.12.31]
- Backup Billing Start [2022.07.10]
- Ending Sale for Basic Edition 1-Core Specification [2022.03.07]
- User Guide
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Constraints and Limits
- Usage Specifications and Suggestions
- Maintaining Instance
- Renaming Instance
- Setting Instance Remarks
- Setting Instance Tag
- Setting Instance Project
- Modify Instance-level Character Set Collation
- Modify System Time Zone
- Setting Instance Maintenance Information
- Multi-AZ Disaster Recovery
- Restarting Instance
- Terminating Instance
- Migrating Across AZs
- Manual Primary-Secondary Switching
- Recycle Bin
- Adjusting Instance Configuration
- Read-Only Instance
- Network and Security
- Account Management
- Database Management
- Data Security
- Parameter Configuration
- Monitoring and Alarms
- Backup and Restoration
- Log Management
- Publish-Subscribe
- SSIS
- Data Migration (New)
- Data Migration (Legacy)
- Best Practice
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Instance Management APIs
- CreateCloudDBInstances
- CreateCloudReadOnlyDBInstances
- ModifyInstanceEncryptAttributes
- UpgradeDBInstance
- RollbackInstance
- RestoreInstance
- RestartDBInstance
- ResetAccountPassword
- ModifyDBRemark
- ModifyDBName
- ModifyDBInstanceProject
- ModifyDBInstanceName
- ModifyAccountPrivilege
- InquiryPriceUpgradeDBInstance
- InquiryPriceCreateDBInstances
- DescribeZones
- DescribeRollbackTime
- DescribeRegions
- DescribeProductConfig
- DescribeFlowStatus
- DescribeDBs
- DescribeDBInstances
- DescribeAccounts
- DeleteDB
- DeleteAccount
- CreateDBInstances
- CreateDB
- CreateAccount
- TerminateDBInstance
- RecycleDBInstance
- CloneDB
- DescribeDBCharsets
- ModifyDatabaseMdf
- ModifyDatabaseCT
- ModifyDatabaseCDC
- DescribeDBsNormal
- ModifyInstanceParam
- DescribeInstanceParams
- DescribeInstanceParamRecords
- OpenInterCommunication
- DescribeDBInstanceInter
- DescribeBusinessIntelligenceFile
- DeleteBusinessIntelligenceFile
- CreateBusinessIntelligenceFile
- CreateBusinessDBInstances
- CloseInterCommunication
- Network Management APIs
- Backup APIs
- RunMigration
- ModifyMigration
- DescribeMigrations
- DescribeMigrationDetail
- DescribeBackups
- DeleteMigration
- CreateMigration
- CreateBackup
- ModifyBackupStrategy
- StartIncrementalMigration
- StartBackupMigration
- ModifyIncrementalMigration
- ModifyBackupMigration
- DescribeUploadBackupInfo
- DescribeIncrementalMigration
- DescribeBackupUploadSize
- DescribeBackupMigration
- DescribeBackupCommand
- DeleteIncrementalMigration
- DeleteBackupMigration
- CreateIncrementalMigration
- CreateBackupMigration
- DescribeBackupFiles
- Extended Event APIs
- Database APIs
- Other APIs
- Data Types
- Error Codes
- FAQs
- Overview
- Model Selection
- Pricing and Selection
- Connection and Network
- Account and Permission
- Backup and Rollback
- Data Migration
- Publish/Subscribe
- Read-Only Instance
- Version and Architecture Upgrade
- Disk Space and Specification Adjustment
- Monitoring and Alarms
- Log
- Parameter Modification
- Features
- Performance/Space/Memory
- Service Agreement
- Performance Evaluation
- Glossary
- Contact Us
- Release Notes and Announcements
- Release Notes
- Announcements
- Announcement on Changing External Network Links
- Interface Authentication Upgrade Announcement
- Maintenance Time Change from Local Time to Beijing Time
- Account Type and Permission Changes
- Product Architecture Name Change
- Disk Storage Space Composition Change
- Ending Support for Classic Network [2022.12.31]
- Backup Billing Start [2022.07.10]
- Ending Sale for Basic Edition 1-Core Specification [2022.03.07]
- User Guide
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Constraints and Limits
- Usage Specifications and Suggestions
- Maintaining Instance
- Renaming Instance
- Setting Instance Remarks
- Setting Instance Tag
- Setting Instance Project
- Modify Instance-level Character Set Collation
- Modify System Time Zone
- Setting Instance Maintenance Information
- Multi-AZ Disaster Recovery
- Restarting Instance
- Terminating Instance
- Migrating Across AZs
- Manual Primary-Secondary Switching
- Recycle Bin
- Adjusting Instance Configuration
- Read-Only Instance
- Network and Security
- Account Management
- Database Management
- Data Security
- Parameter Configuration
- Monitoring and Alarms
- Backup and Restoration
- Log Management
- Publish-Subscribe
- SSIS
- Data Migration (New)
- Data Migration (Legacy)
- Best Practice
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Instance Management APIs
- CreateCloudDBInstances
- CreateCloudReadOnlyDBInstances
- ModifyInstanceEncryptAttributes
- UpgradeDBInstance
- RollbackInstance
- RestoreInstance
- RestartDBInstance
- ResetAccountPassword
- ModifyDBRemark
- ModifyDBName
- ModifyDBInstanceProject
- ModifyDBInstanceName
- ModifyAccountPrivilege
- InquiryPriceUpgradeDBInstance
- InquiryPriceCreateDBInstances
- DescribeZones
- DescribeRollbackTime
- DescribeRegions
- DescribeProductConfig
- DescribeFlowStatus
- DescribeDBs
- DescribeDBInstances
- DescribeAccounts
- DeleteDB
- DeleteAccount
- CreateDBInstances
- CreateDB
- CreateAccount
- TerminateDBInstance
- RecycleDBInstance
- CloneDB
- DescribeDBCharsets
- ModifyDatabaseMdf
- ModifyDatabaseCT
- ModifyDatabaseCDC
- DescribeDBsNormal
- ModifyInstanceParam
- DescribeInstanceParams
- DescribeInstanceParamRecords
- OpenInterCommunication
- DescribeDBInstanceInter
- DescribeBusinessIntelligenceFile
- DeleteBusinessIntelligenceFile
- CreateBusinessIntelligenceFile
- CreateBusinessDBInstances
- CloseInterCommunication
- Network Management APIs
- Backup APIs
- RunMigration
- ModifyMigration
- DescribeMigrations
- DescribeMigrationDetail
- DescribeBackups
- DeleteMigration
- CreateMigration
- CreateBackup
- ModifyBackupStrategy
- StartIncrementalMigration
- StartBackupMigration
- ModifyIncrementalMigration
- ModifyBackupMigration
- DescribeUploadBackupInfo
- DescribeIncrementalMigration
- DescribeBackupUploadSize
- DescribeBackupMigration
- DescribeBackupCommand
- DeleteIncrementalMigration
- DeleteBackupMigration
- CreateIncrementalMigration
- CreateBackupMigration
- DescribeBackupFiles
- Extended Event APIs
- Database APIs
- Other APIs
- Data Types
- Error Codes
- FAQs
- Overview
- Model Selection
- Pricing and Selection
- Connection and Network
- Account and Permission
- Backup and Rollback
- Data Migration
- Publish/Subscribe
- Read-Only Instance
- Version and Architecture Upgrade
- Disk Space and Specification Adjustment
- Monitoring and Alarms
- Log
- Parameter Modification
- Features
- Performance/Space/Memory
- Service Agreement
- Performance Evaluation
- Glossary
- Contact Us
SSL encryption overview
Secure Sockets Layer (SSL) authentication signifies the process of authenticating the connection from the clients to the cloud server, applicable to both the users and server. Enabling SSL encryption allows you to acquire a CA certificate and upload it to the server. When the clients access the database, the SSL protocol is activated. An SSL secure channel between the clients and the cloud server is established. This mechanism ensures encrypted data transmission, which prevents data interception and unauthorized modification, thus ensuring the safe transmission of information from both parties.
The SSL protocol needs to be established based on reliable TCP and has the advantage of being independent from application layer protocols. Therefore, high-level application layer protocols such as HTTP, FTP, and TELNET can be transparently established based on it. It completes encryption algorithm processing, communication key negotiation, and server authentication before communication is made over application layer protocols. After that, all data transferred over application layer protocols will be encrypted to ensure communication privacy.
Background
SSL, a security confidentiality protocol proposed by Netscape, constructs secure channels for data transmission between browsers and Web servers. It employs encryption algorithms such as RC4, MD5, and RSA to actualize secure communication. The Internet Engineering Task Force (IETF) standardized SSL 3.0, renaming it as the Transport Layer Security (TLS) after standardization. However, since the term SSL is more commonly used, SSL encryption in this document actually refers to TLS encryption.
Note:
The versions of TLS supported by Tencent Cloud Database are 1.0, 1.1, and 1.2.
In scenarios where a database is connected in an unencrypted manner, all information being transmitted over the network is in plaintext, thus posing the risk of being intercepted, tampered with, and impersonated by illegal users. The SSL protocols are designed to solve these risks and can theoretically achieve:
The information is propagated in an encrypted manner, impervious to interception by any third parties.
There is a verification mechanism for immediate tampering detection by both parties in the communication.
Identity certificates will be used to authenticate the identity.
TencentDB for SQL Server enhances linkage security through the employment of SSL encryption, supporting the download and installation of SSL CA certificates to the corresponding application services.
Note:
Not protecting the data itself, SSL encryption guarantees the security of the traffic between the clients and the cloud database server. By encrypting the network connection at the transport layer, it can boost the security and integrity of the communication data. But this will concurrently increase the network connection response time.
Supported Architectures and Versions
The database instances of all the architectures and versions of TencentDB for SQL Server support SSL encryption settings. In this settings, read-only instances do not need to be configured separately. Once SSL encryption is enabled on a primary instance, it will automatically apply to its read-only instances.
Note:
If you set SSL on the primary instance and choose to execute it during maintenance time, the read-only instances associated with the primary instances will follow the primary instances to take effect. The SSL will take effect along with a restart during the maintenance time of the primary instance.
Notes
After the SSL encryption is enabled, the CPU usage of the instances will rise and the delay in read-write operations will increase. It is suggested that SSL encryption should be enabled only when there is a demand for encryption in the public network linkage. The private network linkage is relatively safe and usually does not require encryption.
Enabling SSL encryption, updating SSL Certificates provided by Tencent Cloud, or disabling SSL encryption will restart the database instance. The instance may be unavailable for a few minutes. Therefore, ensure that your business has a reconnection mechanism before operation. It is recommended that should be done during off-peak hours.
The SSL certificate has a validity period (one year). Please manually renew the validity period of the certificate in the console prior to its expiration, otherwise, the client programs using SSL encrypted connections will not be able to connect normally.
If the SSL certificate is not renewed after expiration, it will only cause the client programs using encrypted connections to be unable to connect with the instance normally. But it will not affect the normal operation of the instance or data security.
After SSL encryption is disabled, the instance can only be connected through non-SSL encrypted methods.
Enabling SSL encryption
1. Log in to the TencentDB for SQL Server console.
2. Select Region. Click Instance ID that needs to enable SSL in the instance list or Manage in the Operation column.
3. On the Instance Management page, select Data Security > SSL Encryption. Then, click the button to enable the feature after SSL encryption status.
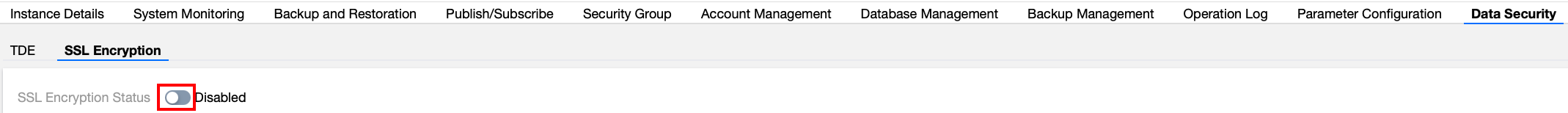
4. Select the execution time in the pop-up window, and click Confirm.
Certificate Origin: By default, the certificate provided by Tencent Cloud is used.
Execution time:
Immediate Execution: SSL encryption is activated immediately after you click OK.
During Maintenance Time: SSL encryption is activated during the instance maintenance time. Modification of the instance maintenance time can be done on the instance details page.
Note:
For detailed description of instance status changes during the activation of SSL encryption, please refer to Appendix 1.
In the process of enabling SSL encryption, your database instance will be restarted. Be sure that your business has a reconnection mechanism.
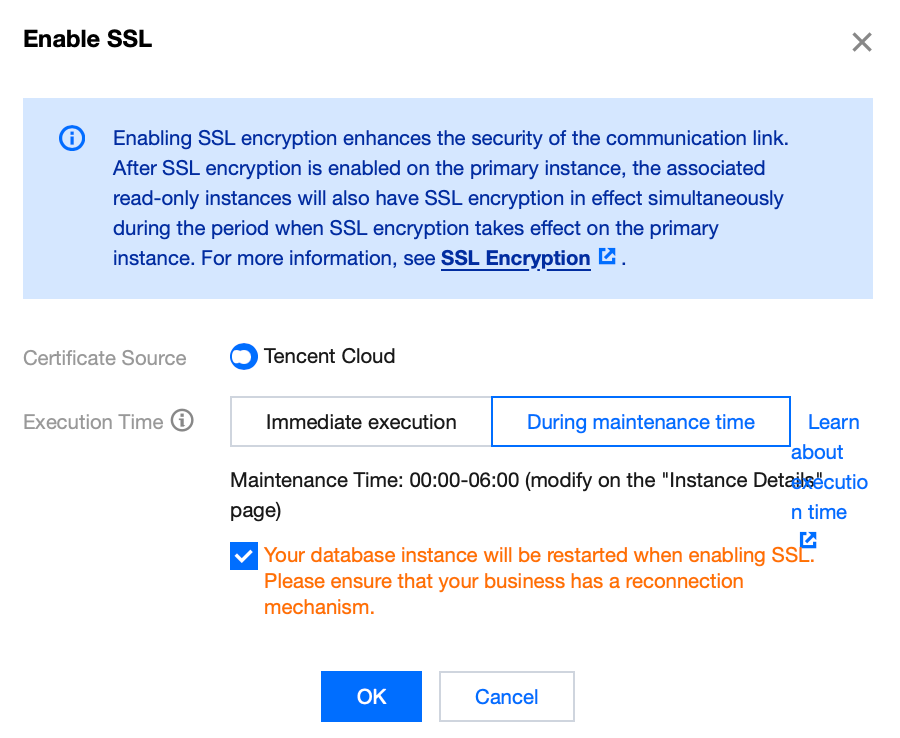
5. Once
activated successfully
, the interface will appear as follows.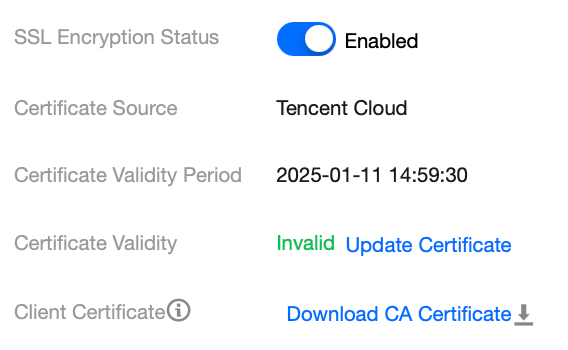
Please note that configuring the client CA certificate is an optional setting, which is used for the clients to trust the server. Click Download CA Certificate to download the certificate and install it onto the clients.
The downloaded file is a compressed package (TencentDB-SSL-CA.zip), containing the following three files:
.p7b file: It is used to import the CA certificate in Windows.
.jks file: It is a truststore certificate storage file in Java with a unified password tencentdb, which is used to import the CA certificate chain in the Java program.
.pem file: It is used to import the CA certificate in other systems or applications.
Connecting to SSL VPN Client
Once SSL encryption is enabled, when the clients are logging in to the TencentDB for SQL Server instances, there exist two scenarios of the trusted server certificate and the untrusted server certificate. If the server certificate is trusted, there's no need to configure SSL CA certificate for encrypted connections. However, if it isn't trusted, you are required to import and set up the SSL CA certificate for establishing the encrypted connection.
Scenario One: Encrypted Connection and Trusted Server Certificate
Step 1: Encrypted Connection Login
1. Open the SQL Server Management Studio client, and click Option in the lower right corner of the dialogue box.
2. On the Connection Properties tab, enable the Encrypt Connection and Trust Server Certificate options, then click Connect.
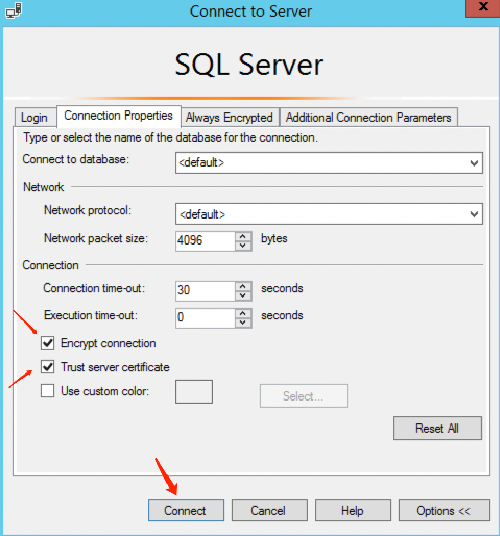
Step 2: Validate Whether the Connection is Encrypted
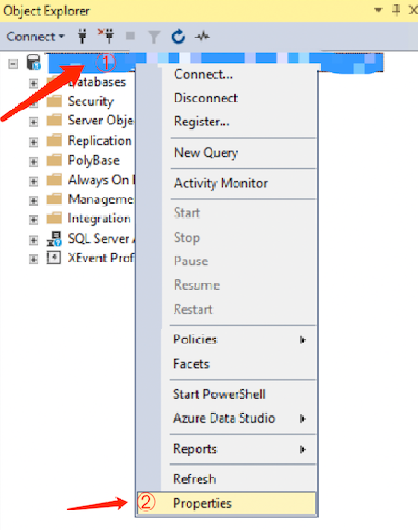
1. Once the connection is successful via SSMS, right-click on the instance and select Properties.
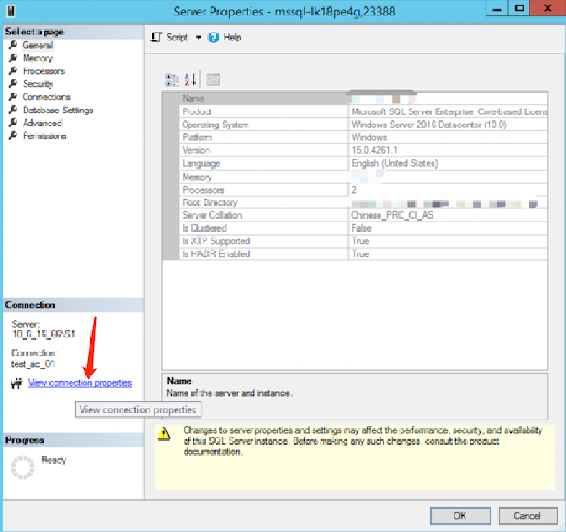
2. On the service properties page that pops up, click View connection properties on the left.
3. On the connection property page, you can view whether the connection has been encrypted.
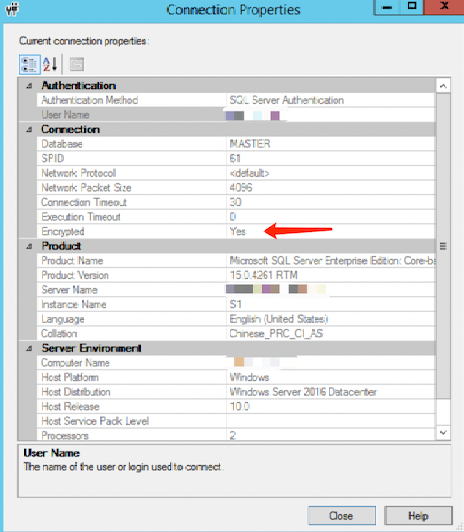
Execute the following query command. If the query result is TRUE, it indicates that the connection is encrypted. If the result is FALSE, it signifies that the connection is not encrypted.
SELECT ENCRYPT_OPTION FROM SYS.DM_EXEC_CONNECTIONS WHERE SESSION_ID = @@SPID;
Scenario Two: Encrypted connection and untrusted server certificate
Step 1: Download the CA Certificate
After the SSL encryption is enabled, on the target instance details page > Data Security > SSL Encryption, click Download CA certificate.
Step 2: Clients import the CA certificate
1. Click the search box in the lower-left corner of the desktop, and input certmgr.msc to open the Certificate Manager.
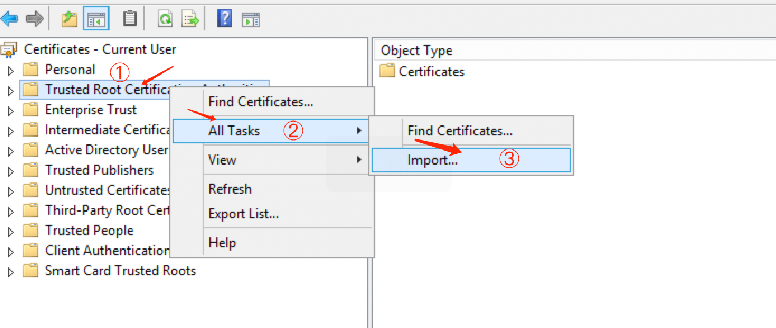
2. In the certmgr dialog box, right-click Trusted Root Certification Authorities, and choose All Tasks > Import.
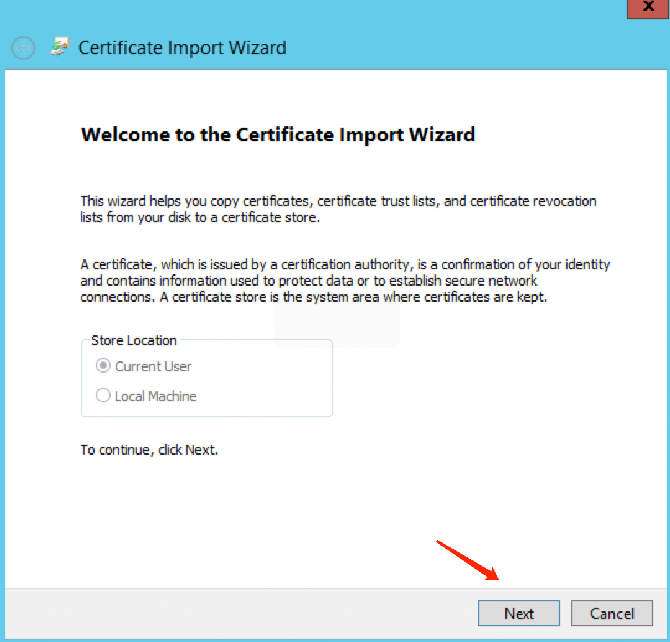
3. Click Next.
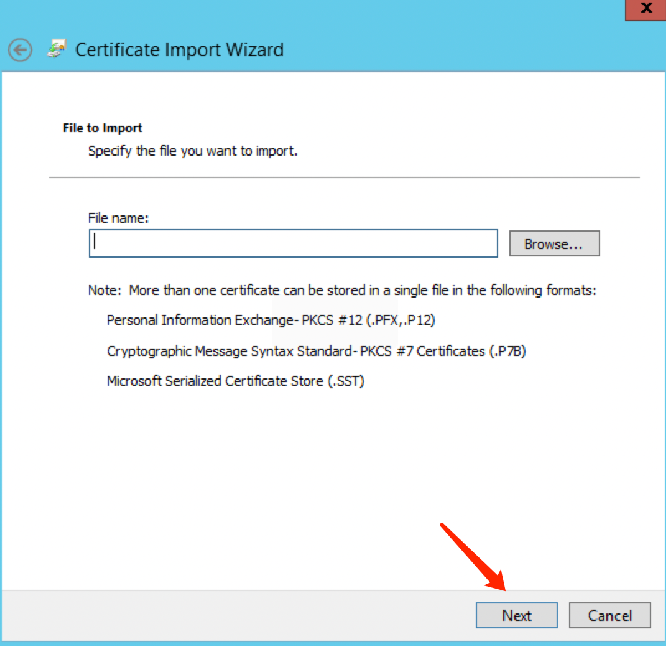
4. On the Certificate Import Wizard page, click Browse to import the downloaded SSL CA certificate, and then click Next.
5. Select the locally downloaded TencentDB-SSL-CA certificate file, and click Open.
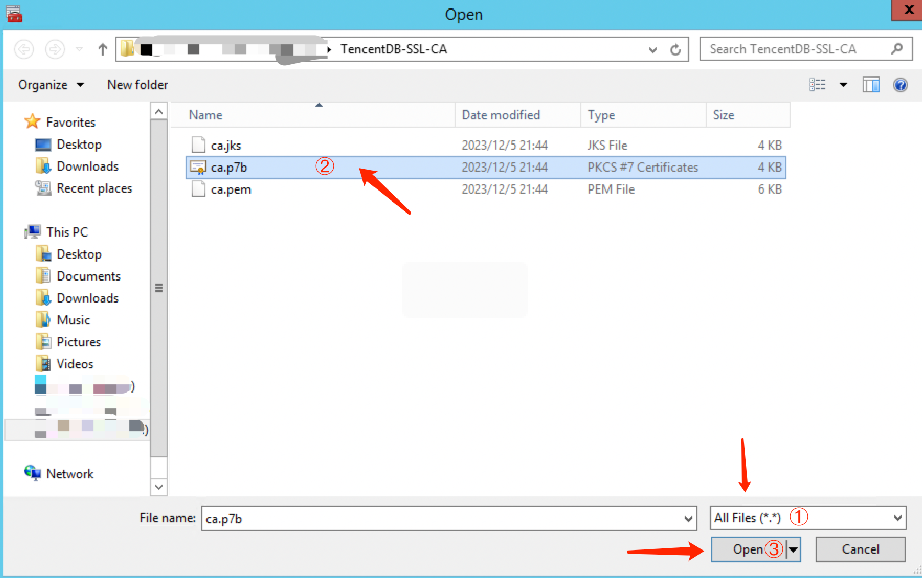
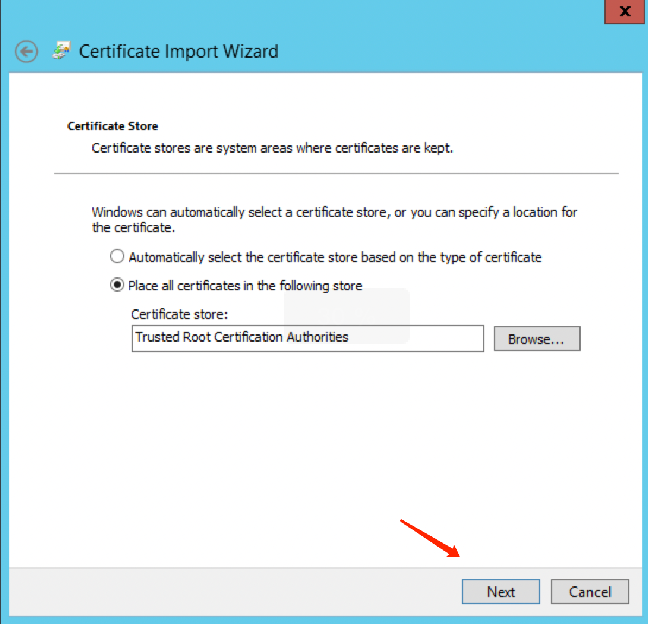
6. Select the location to store the certificates according to personal needs, then click Next, followed by clicking Done.
You can also import the SSL CA certificate by commands. For instance, you can execute the following command to import the certificate via CMD or PowerShell.
CERTUTIL -addstore -enterprise -f -v root "ca.p7b"
Step 3: Log in through an encrypted connection
1. Open the hosts file located at C:\\Windows\\System32\\drivers\\etc.
2. Add IP mssql-******* at the end of the hosts file.
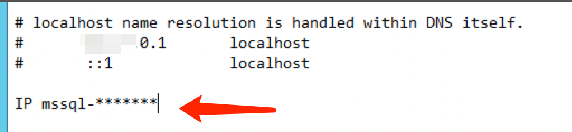
Note:
IP: Substitute it with the private or public IP address of the the corresponding instance.
mssql-*******: Replace it with the corresponding instance ID.
3. Open the SQL Server Management Studio client, click on the Option in the lower right corner of the dialogue box.
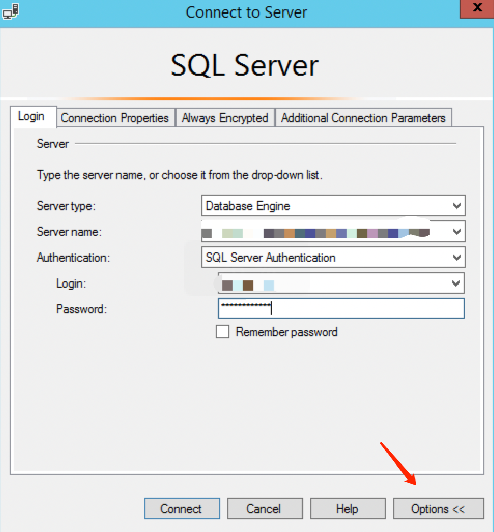
4. On the Connection Properties tab, check the Encrypt Connection, and then click Connect.
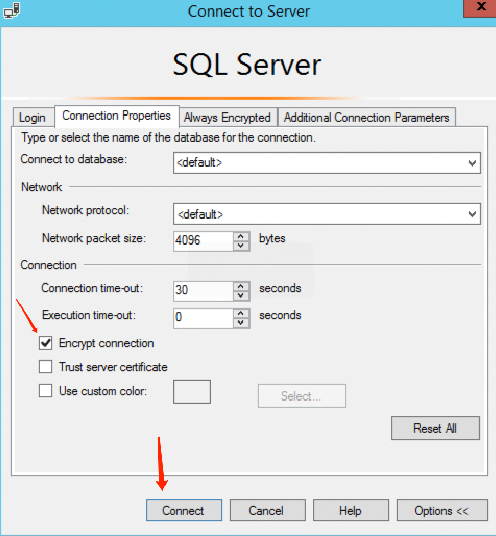
Step 4: Verify if the connection has been encrypted
1. Once the connection is successful via SSMS, right-click on the instance and select Properties.
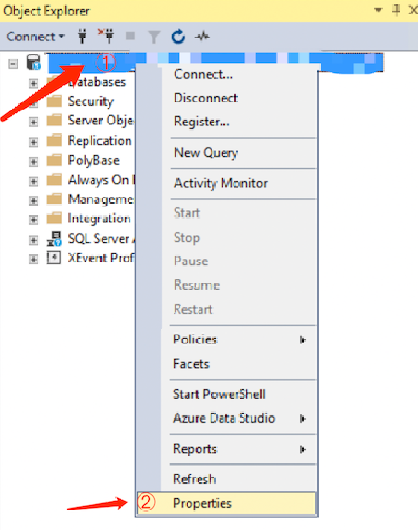
2. On the service properties page that pops up, click View connection properties on the left.
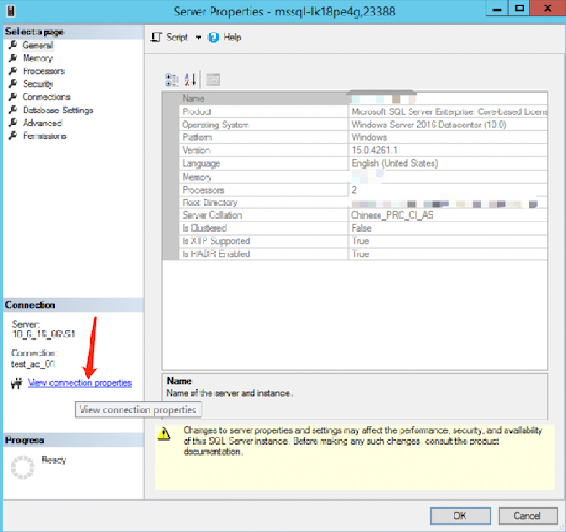
3. On the connection property page that pops up, you can view whether the connection has been encrypted.
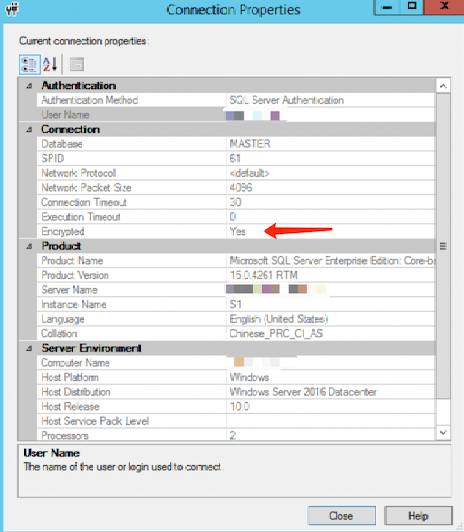
Execute the following query command. If the query result is TRUE, it indicates that the connection is encrypted. If the result is FALSE, it signifies that the connection is not encrypted.
SELECT ENCRYPT_OPTION FROM SYS.DM_EXEC_CONNECTIONS WHERE SESSION_ID = @@SPID
Updating the validity period of the certificate
Note:
The SSL certificate has a validity period (one year). You need to manually update the certificate before it expires to ensure that client programs using SSL encrypted connections can continue to connect normally.
During the update of SSL Certificates, your database instance will be restarted to load the new SSL Certificates. Please ensure that your business has a reconnection mechanism.
1. Log in to the TencentDB for SQL Server console.
2. Select Region. Click Instance ID of the target SSL or Manage in the Operation column.
3. Choose Data Safety > SSL Encryption on the Instance Management page, then click Update Certificate after the validity of SSL Certificates.
4. Select the execution time in the pop-up window, and click Confirm.
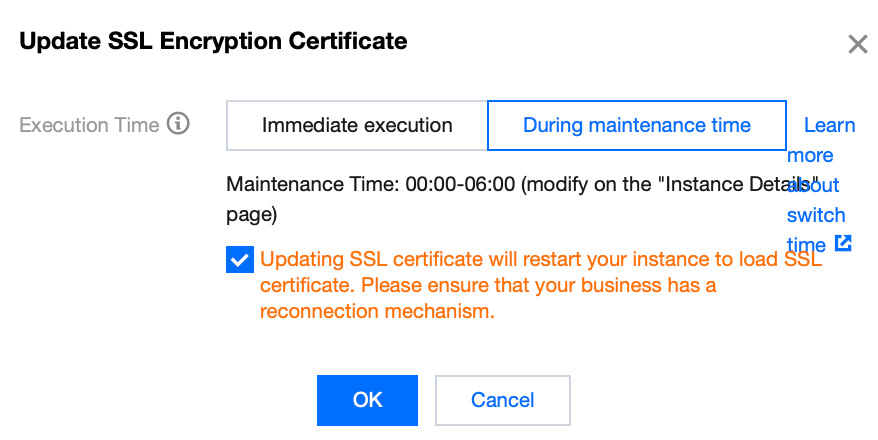
Execution time:
Immediate execution: SSL Certificates will promptly be updated upon you click OK.
During maintenance time: Update SSL Certificates within the instance maintenance time. Modification of the instance maintenance time can be done on the instance details page.
Disabling SSL encryption
Note:
During the process of disabling SSL encryption, your database instance will be restarted. Please ensure that your business has a reconnection mechanism.
1. Log in to the TencentDB for SQL Server console.
2. Select Region. In the instance list, click Instance ID of the instance that needs to disable SSL or Manage in the Operation column.
3. Select Data Security > SSL Encryption on the Instance Management page, then click the button to disable the function after SSL Encryption Status.
4. Select the execution time in the popup, and click OK.
Execution time:
Immediate execution: SSL encryption will be disabled immediately upon you click OK.
During maintenance time: Disable SSL encryption within the instance maintenance time. Modification of the instance maintenance time can be done on the instance details page.
Appendix 1: Changes for Instance-related Status during SSL Settings
During SSL settings, if the chosen execution time falls within the maintenance time, the system will check at a 10-minute interval whether the SSL settings related operations coincide with the maintenance time. If the operations coincide with the maintenance time, the system commences the deployment or termination of SSL, and promptly reboots the service upon completion.
Note:
If a user schedules an SSL operation during the maintenance time, and the designated instance is in a non-operational status prior to reaching this window, further tasks cannot be initiated from this instance until the SSL encryption operation has concluded.
Example
Assume that the maintenance time is set from 17:00 to 18:00. If a user configures to enable SSL encryption within this maintenance time at 17:05, the system initiates the asynchronous scheduling task at 17:10. Once successful deployment of SSL Certificates is accomplished, the service restarts immediately.
Explanation for Instance Status Changes
The status change of instances chosen to be executed during the maintenance time is as follows:
Prior to 17:05, the instance status was in operation;
Between 17:05 and 17:10, the status of the primary instance and the RO Replica instance is in the process of SSL operation;
After 17:10, the status of the primary instance and the RO replica instance is in the process of task execution;
Not until the asynchronous task is completed do the state of both the primary instance and RO replica instance revert back to Running.
The status changes of instances for which the execution time is set to immediate execution are as follows:
After an SSL operation task is initiated via the console, the status of both the primary instance and the RO replica instance changes to Task Execution In Progress. It only reverts back to Running after the asynchronous task is completed.
Explanation of the SSL Operation Status Change of Instances
The changes in the instance operation status when SSL encryption is initiated are as follows:
The execution time is set to immediate execution: Not activated-> Activating-> Activated.
Execution time is within the maintenance time: Not activated-> Waiting for activation within the maintenance time window-> Activating-> Activated.
The changes to the instance operation status when the certificate is updated are as follows:
The execution time is set to immediate execution: Activated -> updating -> initiated .
The execution time is within the maintenance time: Not initiated-> Waiting for updates within the maintenance time window-> Updating-> Activated.
The changes in the instance operation status are as follows when SSL is disabled:
Execution time is set to immediate execution: Enabled-> Being disabled-> Disabled.
The execution time is within the maintenance time: Enabled-> Waiting for disabling in maintenance time window-> Being disabled-> Disabled.
FAQs
How can you view whether the SSL encryption has been enabled for the current connection?
You can query the sys.dm_exec_connections dynamic management view by using the following command, which will inform you whether the current connection has SSL encryption:
SELECT session_id,encrypt_optionFROM sys.dm_exec_connections;GO
If the sys.dm_exec_connections dynamic management view query returns the session ID of the current connection and the encrypt_option value is true, then it demonstrates that the connection has successfully enabled SSL encryption.
Why was the client software able to establish a connection last year, but fails to establish a connection this year?
The SSL certificate has an expiration date, typically one year. The issue might be due to certificate expiration, which needs manual renewal. For detailed steps, refer to Renewing the Certificate Validity Period.

 Yes
Yes
 No
No
Was this page helpful?