- Release Notes and Announcements
- Tencent Cloud Network Overview
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Network Topology
- Virtual Private Cloud (VPC)
- Subnets
- Route Tables
- IPs and ENIs
- Bandwidth Package
- Network Connection
- Security Management
- Diagnostic Tools
- Alarming and Monitoring
- Sharing VPC Subnet Resource
- Best Practices
- View the Total Bandwidth for Single-Region Traffic-Based Billing
- Migrating from the Classic Network to VPC
- Best Practices of Security Group Change
- Configuring CVM Instance as Public Gateway
- Building HA Primary/Secondary Cluster with HAVIP + Keepalived
- Creating a High-availability Database by Using HAVIP + Windows Server Failover Cluster
- Hybrid Cloud Primary/Secondary Communication (DC and VPN)
- Hybrid Cloud Primary/Secondary Communication (CCN and VPN)
- CVM Access to Internet Through EIP
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- VPC APIs
- DeleteTrafficPackages
- DescribeUsedIpAddress
- DescribeAccountAttributes
- CreateDefaultVpc
- CreateVpc
- ModifyVpcAttribute
- DescribeVpcs
- DescribeVpcPrivateIpAddresses
- DescribeVpcInstances
- DeleteVpc
- AttachClassicLinkVpc
- DescribeClassicLinkInstances
- DetachClassicLinkVpc
- AssignIpv6CidrBlock
- DescribeVpcIpv6Addresses
- UnassignIpv6CidrBlock
- CreateAssistantCidr
- ModifyAssistantCidr
- DescribeAssistantCidr
- CheckAssistantCidr
- DeleteAssistantCidr
- DescribeVpcResourceDashboard
- ModifyLocalGateway
- DescribeLocalGateway
- DeleteLocalGateway
- CreateLocalGateway
- AdjustPublicAddress
- DescribeTrafficPackages
- Subnet APIs
- Route Table APIs
- EIP APIs
- Highly Available Virtual IP APIs
- ENI APIs
- AssignPrivateIpAddresses
- UnassignPrivateIpAddresses
- ModifyNetworkInterfaceAttribute
- DetachNetworkInterface
- DescribeNetworkInterfaces
- CreateNetworkInterface
- AttachNetworkInterface
- MigratePrivateIpAddress
- MigrateNetworkInterface
- DeleteNetworkInterface
- ModifyPrivateIpAddressesAttribute
- UnassignIpv6Addresses
- ModifyIpv6AddressesAttribute
- AssignIpv6Addresses
- DescribeNetworkInterfaceLimit
- DisassociateNetworkInterfaceSecurityGroups
- AssociateNetworkInterfaceSecurityGroups
- CreateAndAttachNetworkInterface
- IP Location APIs
- Bandwidth Package APIs
- NAT Gateway APIs
- DescribeNatGateways
- ResetNatGatewayConnection
- ModifyNatGatewayDestinationIpPortTranslationNatRule
- ModifyNatGatewayAttribute
- DisassociateNatGatewayAddress
- DescribeNatGatewayDestinationIpPortTranslationNatRules
- DeleteNatGatewayDestinationIpPortTranslationNatRule
- DeleteNatGateway
- CreateNatGatewayDestinationIpPortTranslationNatRule
- CreateNatGateway
- AssociateNatGatewayAddress
- ModifyNatGatewaySourceIpTranslationNatRule
- DescribeNatGatewaySourceIpTranslationNatRules
- DeleteNatGatewaySourceIpTranslationNatRule
- CreateNatGatewaySourceIpTranslationNatRule
- RefreshDirectConnectGatewayRouteToNatGateway
- DescribeNatGatewayDirectConnectGatewayRoute
- VPN Gateway APIs
- GenerateVpnConnectionDefaultHealthCheckIp
- ResetVpnGatewayInternetMaxBandwidth
- ResetVpnConnection
- RenewVpnGateway
- ModifyVpnGatewayAttribute
- ModifyVpnConnectionAttribute
- ModifyCustomerGatewayAttribute
- InquiryPriceResetVpnGatewayInternetMaxBandwidth
- InquiryPriceRenewVpnGateway
- InquiryPriceCreateVpnGateway
- DownloadCustomerGatewayConfiguration
- DescribeVpnGateways
- DescribeVpnConnections
- DescribeCustomerGateways
- DescribeCustomerGatewayVendors
- DeleteVpnGateway
- DeleteVpnConnection
- DeleteCustomerGateway
- CreateVpnGateway
- CreateVpnConnection
- CreateCustomerGateway
- ModifyVpnGatewayCcnRoutes
- DescribeVpnGatewayCcnRoutes
- ModifyVpnGatewayRoutes
- DescribeVpnGatewayRoutes
- DeleteVpnGatewayRoutes
- CreateVpnGatewayRoutes
- SetVpnGatewaysRenewFlag
- Direct Connect Gateway APIs
- ReplaceDirectConnectGatewayCcnRoutes
- DescribeDirectConnectGatewayCcnRoutes
- DeleteDirectConnectGatewayCcnRoutes
- CreateDirectConnectGatewayCcnRoutes
- CreateDirectConnectGateway
- ModifyDirectConnectGatewayAttribute
- DescribeDirectConnectGateways
- DeleteDirectConnectGateway
- DisassociateDirectConnectGatewayNatGateway
- AssociateDirectConnectGatewayNatGateway
- InquirePriceCreateDirectConnectGateway
- Cloud Connect Network APIs
- SetCcnRegionBandwidthLimits
- ModifyCcnAttribute
- EnableCcnRoutes
- DisableCcnRoutes
- DetachCcnInstances
- DescribeCcns
- DescribeCcnRoutes
- DescribeCcnRegionBandwidthLimits
- DescribeCcnAttachedInstances
- DeleteCcn
- CreateCcn
- AttachCcnInstances
- ResetAttachCcnInstances
- RejectAttachCcnInstances
- AcceptAttachCcnInstances
- ModifyCcnRegionBandwidthLimitsType
- GetCcnRegionBandwidthLimits
- DescribeCrossBorderCompliance
- AuditCrossBorderCompliance
- ModifyCcnAttachedInstancesAttribute
- Security Group APIs
- ReplaceSecurityGroupPolicies
- DeleteSecurityGroup
- DescribeSecurityGroupPolicies
- ModifySecurityGroupAttribute
- CreateSecurityGroup
- CreateSecurityGroupPolicies
- DescribeSecurityGroups
- DeleteSecurityGroupPolicies
- ModifySecurityGroupPolicies
- ReplaceSecurityGroupPolicy
- DescribeSecurityGroupAssociationStatistics
- DescribeSecurityGroupReferences
- CreateSecurityGroupWithPolicies
- CloneSecurityGroup
- Network ACL APIs
- Network Parameter Template-Related APIs
- CreateAddressTemplate
- CreateAddressTemplateGroup
- CreateServiceTemplate
- CreateServiceTemplateGroup
- DeleteAddressTemplate
- DeleteAddressTemplateGroup
- DeleteServiceTemplate
- DeleteServiceTemplateGroup
- DescribeAddressTemplateGroups
- DescribeAddressTemplates
- DescribeServiceTemplateGroups
- DescribeServiceTemplates
- ModifyAddressTemplateAttribute
- ModifyAddressTemplateGroupAttribute
- ModifyServiceTemplateAttribute
- ModifyServiceTemplateGroupAttribute
- Network Detection-Related APIs
- Flow Log APIs
- Gateway Traffic Monitor APIs
- Private Link APIs
- CreateVpcEndPointService
- DescribeVpcEndPointService
- ModifyVpcEndPointServiceAttribute
- DeleteVpcEndPointService
- CreateVpcEndPointServiceWhiteList
- DescribeVpcEndPointServiceWhiteList
- ModifyVpcEndPointServiceWhiteList
- EnableVpcEndPointConnect
- DeleteVpcEndPointServiceWhiteList
- DescribeVpcEndPoint
- CreateVpcEndPoint
- ModifyVpcEndPointAttribute
- DeleteVpcEndPoint
- DisassociateVpcEndPointSecurityGroups
- Snapshot Policy APIs
- Other APIs
- Data Types
- Error Codes
- FAQs
- Contact Us
- Glossary
- Release Notes and Announcements
- Tencent Cloud Network Overview
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Network Topology
- Virtual Private Cloud (VPC)
- Subnets
- Route Tables
- IPs and ENIs
- Bandwidth Package
- Network Connection
- Security Management
- Diagnostic Tools
- Alarming and Monitoring
- Sharing VPC Subnet Resource
- Best Practices
- View the Total Bandwidth for Single-Region Traffic-Based Billing
- Migrating from the Classic Network to VPC
- Best Practices of Security Group Change
- Configuring CVM Instance as Public Gateway
- Building HA Primary/Secondary Cluster with HAVIP + Keepalived
- Creating a High-availability Database by Using HAVIP + Windows Server Failover Cluster
- Hybrid Cloud Primary/Secondary Communication (DC and VPN)
- Hybrid Cloud Primary/Secondary Communication (CCN and VPN)
- CVM Access to Internet Through EIP
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- VPC APIs
- DeleteTrafficPackages
- DescribeUsedIpAddress
- DescribeAccountAttributes
- CreateDefaultVpc
- CreateVpc
- ModifyVpcAttribute
- DescribeVpcs
- DescribeVpcPrivateIpAddresses
- DescribeVpcInstances
- DeleteVpc
- AttachClassicLinkVpc
- DescribeClassicLinkInstances
- DetachClassicLinkVpc
- AssignIpv6CidrBlock
- DescribeVpcIpv6Addresses
- UnassignIpv6CidrBlock
- CreateAssistantCidr
- ModifyAssistantCidr
- DescribeAssistantCidr
- CheckAssistantCidr
- DeleteAssistantCidr
- DescribeVpcResourceDashboard
- ModifyLocalGateway
- DescribeLocalGateway
- DeleteLocalGateway
- CreateLocalGateway
- AdjustPublicAddress
- DescribeTrafficPackages
- Subnet APIs
- Route Table APIs
- EIP APIs
- Highly Available Virtual IP APIs
- ENI APIs
- AssignPrivateIpAddresses
- UnassignPrivateIpAddresses
- ModifyNetworkInterfaceAttribute
- DetachNetworkInterface
- DescribeNetworkInterfaces
- CreateNetworkInterface
- AttachNetworkInterface
- MigratePrivateIpAddress
- MigrateNetworkInterface
- DeleteNetworkInterface
- ModifyPrivateIpAddressesAttribute
- UnassignIpv6Addresses
- ModifyIpv6AddressesAttribute
- AssignIpv6Addresses
- DescribeNetworkInterfaceLimit
- DisassociateNetworkInterfaceSecurityGroups
- AssociateNetworkInterfaceSecurityGroups
- CreateAndAttachNetworkInterface
- IP Location APIs
- Bandwidth Package APIs
- NAT Gateway APIs
- DescribeNatGateways
- ResetNatGatewayConnection
- ModifyNatGatewayDestinationIpPortTranslationNatRule
- ModifyNatGatewayAttribute
- DisassociateNatGatewayAddress
- DescribeNatGatewayDestinationIpPortTranslationNatRules
- DeleteNatGatewayDestinationIpPortTranslationNatRule
- DeleteNatGateway
- CreateNatGatewayDestinationIpPortTranslationNatRule
- CreateNatGateway
- AssociateNatGatewayAddress
- ModifyNatGatewaySourceIpTranslationNatRule
- DescribeNatGatewaySourceIpTranslationNatRules
- DeleteNatGatewaySourceIpTranslationNatRule
- CreateNatGatewaySourceIpTranslationNatRule
- RefreshDirectConnectGatewayRouteToNatGateway
- DescribeNatGatewayDirectConnectGatewayRoute
- VPN Gateway APIs
- GenerateVpnConnectionDefaultHealthCheckIp
- ResetVpnGatewayInternetMaxBandwidth
- ResetVpnConnection
- RenewVpnGateway
- ModifyVpnGatewayAttribute
- ModifyVpnConnectionAttribute
- ModifyCustomerGatewayAttribute
- InquiryPriceResetVpnGatewayInternetMaxBandwidth
- InquiryPriceRenewVpnGateway
- InquiryPriceCreateVpnGateway
- DownloadCustomerGatewayConfiguration
- DescribeVpnGateways
- DescribeVpnConnections
- DescribeCustomerGateways
- DescribeCustomerGatewayVendors
- DeleteVpnGateway
- DeleteVpnConnection
- DeleteCustomerGateway
- CreateVpnGateway
- CreateVpnConnection
- CreateCustomerGateway
- ModifyVpnGatewayCcnRoutes
- DescribeVpnGatewayCcnRoutes
- ModifyVpnGatewayRoutes
- DescribeVpnGatewayRoutes
- DeleteVpnGatewayRoutes
- CreateVpnGatewayRoutes
- SetVpnGatewaysRenewFlag
- Direct Connect Gateway APIs
- ReplaceDirectConnectGatewayCcnRoutes
- DescribeDirectConnectGatewayCcnRoutes
- DeleteDirectConnectGatewayCcnRoutes
- CreateDirectConnectGatewayCcnRoutes
- CreateDirectConnectGateway
- ModifyDirectConnectGatewayAttribute
- DescribeDirectConnectGateways
- DeleteDirectConnectGateway
- DisassociateDirectConnectGatewayNatGateway
- AssociateDirectConnectGatewayNatGateway
- InquirePriceCreateDirectConnectGateway
- Cloud Connect Network APIs
- SetCcnRegionBandwidthLimits
- ModifyCcnAttribute
- EnableCcnRoutes
- DisableCcnRoutes
- DetachCcnInstances
- DescribeCcns
- DescribeCcnRoutes
- DescribeCcnRegionBandwidthLimits
- DescribeCcnAttachedInstances
- DeleteCcn
- CreateCcn
- AttachCcnInstances
- ResetAttachCcnInstances
- RejectAttachCcnInstances
- AcceptAttachCcnInstances
- ModifyCcnRegionBandwidthLimitsType
- GetCcnRegionBandwidthLimits
- DescribeCrossBorderCompliance
- AuditCrossBorderCompliance
- ModifyCcnAttachedInstancesAttribute
- Security Group APIs
- ReplaceSecurityGroupPolicies
- DeleteSecurityGroup
- DescribeSecurityGroupPolicies
- ModifySecurityGroupAttribute
- CreateSecurityGroup
- CreateSecurityGroupPolicies
- DescribeSecurityGroups
- DeleteSecurityGroupPolicies
- ModifySecurityGroupPolicies
- ReplaceSecurityGroupPolicy
- DescribeSecurityGroupAssociationStatistics
- DescribeSecurityGroupReferences
- CreateSecurityGroupWithPolicies
- CloneSecurityGroup
- Network ACL APIs
- Network Parameter Template-Related APIs
- CreateAddressTemplate
- CreateAddressTemplateGroup
- CreateServiceTemplate
- CreateServiceTemplateGroup
- DeleteAddressTemplate
- DeleteAddressTemplateGroup
- DeleteServiceTemplate
- DeleteServiceTemplateGroup
- DescribeAddressTemplateGroups
- DescribeAddressTemplates
- DescribeServiceTemplateGroups
- DescribeServiceTemplates
- ModifyAddressTemplateAttribute
- ModifyAddressTemplateGroupAttribute
- ModifyServiceTemplateAttribute
- ModifyServiceTemplateGroupAttribute
- Network Detection-Related APIs
- Flow Log APIs
- Gateway Traffic Monitor APIs
- Private Link APIs
- CreateVpcEndPointService
- DescribeVpcEndPointService
- ModifyVpcEndPointServiceAttribute
- DeleteVpcEndPointService
- CreateVpcEndPointServiceWhiteList
- DescribeVpcEndPointServiceWhiteList
- ModifyVpcEndPointServiceWhiteList
- EnableVpcEndPointConnect
- DeleteVpcEndPointServiceWhiteList
- DescribeVpcEndPoint
- CreateVpcEndPoint
- ModifyVpcEndPointAttribute
- DeleteVpcEndPoint
- DisassociateVpcEndPointSecurityGroups
- Snapshot Policy APIs
- Other APIs
- Data Types
- Error Codes
- FAQs
- Contact Us
- Glossary
The instance port verification feature can help you detect the port accessibility of a security group associated with CVM instances, locate faults, and improve the user experience.
This feature supports the accessibility detection of common ports and custom ports. See below for the common ports.
Rule | Port | Description |
Inbound rules | ICMP protocol | Used to pass control messages such as the ping command. ICMP is a control protocol, and no ports are involved. |
| TCP:20 | Used to allow uploads and downloads over FTP. |
| | TCP:21 |
| TCP:22 | Used to allow Linux SSH login. |
| TCP:3389 | Used to allow Windows remote login. |
| TCP:443 | Used to provide website HTTPS service. |
| TCP:80 | Used to provide website HTTP service. |
Outbound rules | ALL | Used to allow all outbound traffic for access to external networks. |
Operation Guide
1. Log in to the VPC console.
2. Click Diagnostic Tools > Port Verification in the left sidebar to access the management page.
3. Select a region at the top of the page, locate the instance you want to verify in the list, and click Quick Check.
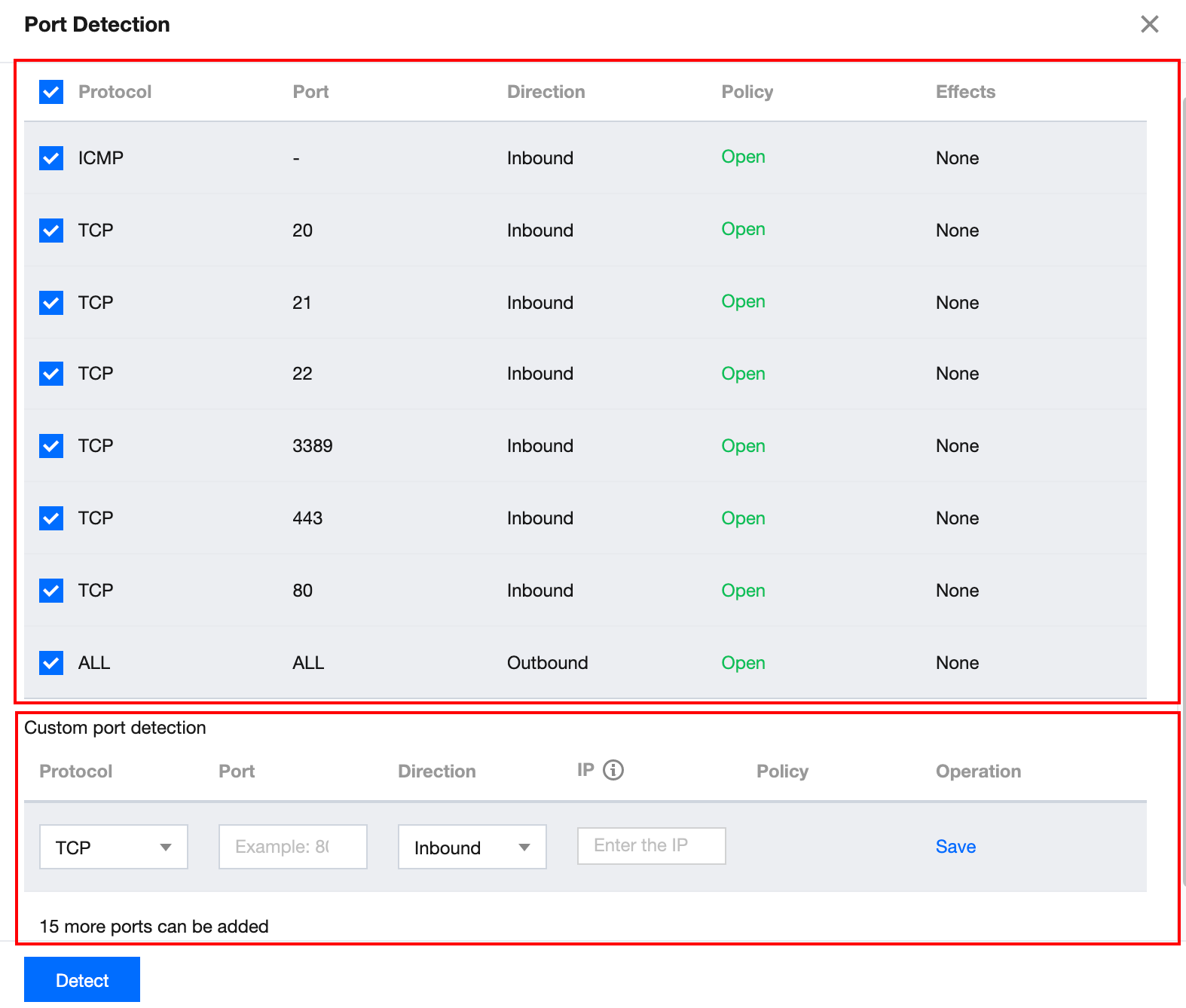
4. You can see the port detection details in the pop-up window. Perform the following operations as needed.
Uncheck the port that you do not want to detect.
Enter custom ports to detect and click Save.
Protocol: select TCP or UDP.
Port: enter one port number to detect, which cannot be the same as a common port.
Direction: select Inbound or Outbound.
IP: enter the source IP for the inbound direction and destination IP for the outbound direction. Enter ALL for all source and destination IP addresses.
Up to 15 custom ports can be detected.
If you need to detect the outbound traffic towards IP 10.0.1.12 using TCP protocol through port 30, enter the following information in the Custom port detection area.
5. After completing the configuration, click Detect. The result will be displayed in the Policy column.
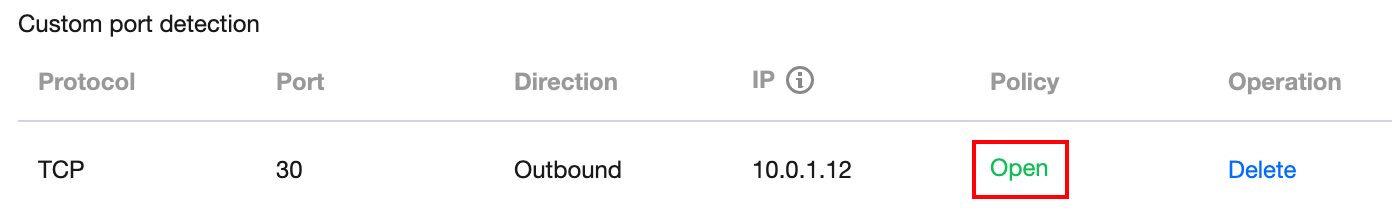
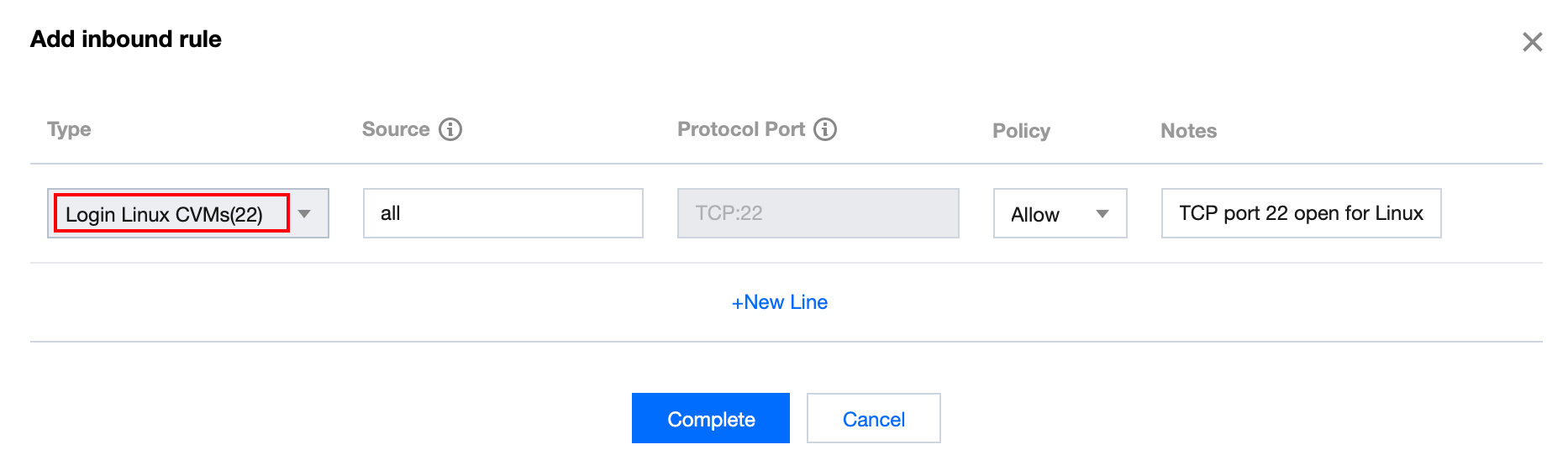
Assumes that you need to open an Not opened port, for example TCP:22,

Then you can add an inbound rule for the security group associated with the instance in the Security Group console to open port TCP:22. You can select all for Source to allow all IPs, or enter a specific IP (IP range).
Relevant Information
For information on security groups, see Security Group Overview and Adding a Security Group Rule.
For more information on common ports, see Common Server Ports.

 Yes
Yes
 No
No
Was this page helpful?