安全组变更示例
最后更新时间:2024-01-24 17:22:28
场景描述
部门 A 的 VPC A 和部门 B 的 VPC B 已经通过云联网或对等连接打通,VPC B 的云服务器可以访问 VPC A 中云服务器上的80端口服务。
部门 A 安全部门在巡检中发现,IP 地址为
172.21.10.13和172.21.10.17的云服务器持续扫描 VPC A 中的非开放端口,造成了攻击式影响。部门 A 业务运维人员接安全部门通知后,决定在安全组规则中针对来源 IP 为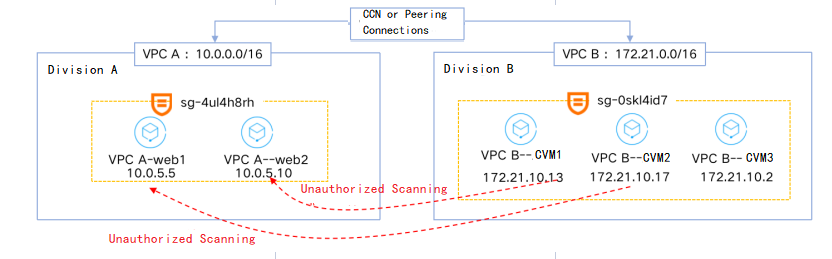
172.21.10.13和172.21.10.17的访问进行封禁。

操作步骤
注意:
建议在业务停服或业务低峰时进行操作。
步骤一:克隆安全组
1. 登录 私有网络控制台,在左侧导航中选择安全 > 安全组。
2. 找到部门 A 受访问攻击的实例关联的安全组,如本例中 sg-4ul4h8rh,单击更多 > 克隆。
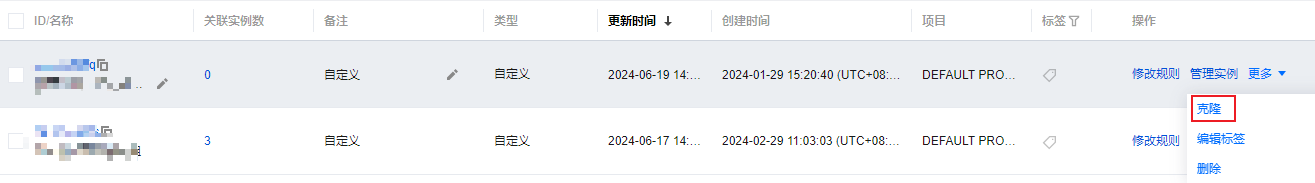

3. 输入克隆安全组的新名称,并单击确定。
步骤二:修改克隆后的安全组
说明:
本例中安全组关联了多个实例,经评估,可将 VPC A 中 web1 实例灰度作为测试实例,稍后用于绑定修改后的克隆安全组进行业务验证。
1. 单击克隆安全组 ID,进入安全组规则详情页。
2. 在入站规则页签,单击添加规则。
3. 在弹出的添加入站规则对话框中,添加攻击方来源 IP(例如
172.21.10.13和172.21.10.17)的拒绝策略,单击完成。注意:
此处经常出现的错误如下:
策略填写错误:例如本例是要禁用攻击方 IP 的流量,那么策略应该是拒绝,如果手误填为允许,将导致无法按照预期禁用流量。
填写网段范围太大:例如本例中只需要禁用 VPC B 中业务1和业务2两台云服务器,而业务3仍需要与 VPC A 通信,如果将入站规则中“来源”填为“
172.21.10.0/24”网段,将导致 VPC B 中业务3也无法访问 VPC A 中的云服务器,不符合预期,因此,如果涉及实例不多,请尽量填写具体 IP 地址,如涉及较多,请尽可能精确填写网段范围,减少不必要的影响。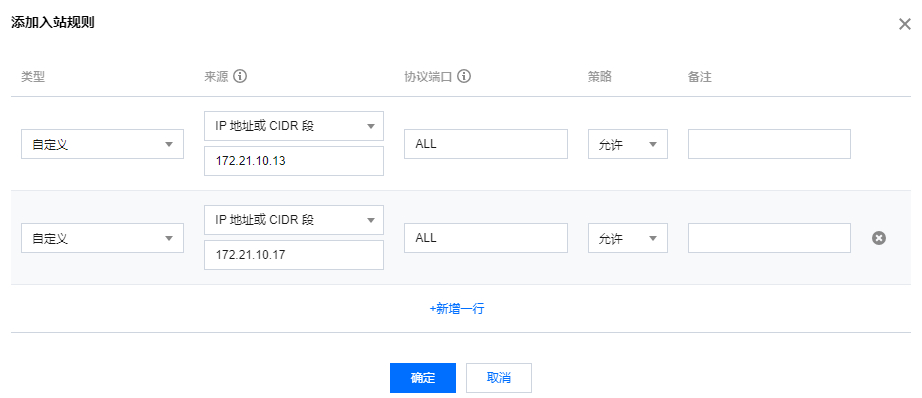
步骤三:将修改后的克隆安全组绑定到测试实例上
说明:
当实例绑定多个安全组时,安全组将由上至下顺序匹配,本例请将克隆安全组移至测试实例原有安全组的最上面,确保克隆安全组优先匹配生效。
1. 单击克隆安全组右侧操作列的管理实例,进入关联实例界面。
2. 单击新增关联,选择需要关联的实例,如本例中的测试实例 web1。
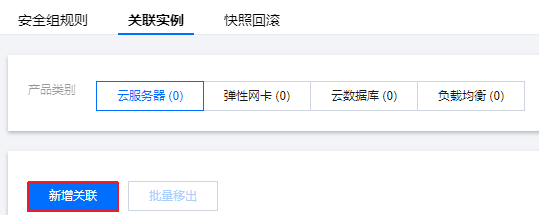

3. 单击确定。
4. 观测测试实例业务是否持续正常。
如业务正常,则执行下一步。
如业务异常,则变更回退,进行问题回溯,如在变更窗口内已明确问题,请评估是否继续修改克隆安全组并继续变更,如是,则重复 步骤二;如否,则本次变更终止,结束。
说明:
经观测本例中测试实例上的业务持续正常,说明修改克隆安全组符合预期。
步骤四:解绑测试实例上的克隆安全组
说明:
将测试实例上的克隆安全组进行解绑,稍后修改原安全组。
请注意,如果一个实例只关联了一个安全组,则无法进行安全组解绑操作。
1. 单击克隆安全组右侧操作列的管理实例,进入关联实例界面。
2. 在需要解绑安全组的实例(如本例中的测试实例web1)右侧,单击移出安全组完成该实例安全组的解绑。
步骤五:修改原安全组
1. 单击原安全组 ID,本例中为 VPC A 中 web1 和 web2 绑定的安全组 ID,进入安全组规则详情页。
2. 在入站规则页签,单击添加规则。
3. 在弹出的添加入站规则对话框中,添加攻击方来源 IP(例如
172.21.10.13和172.21.10.17)的拒绝策略,请确保规则中来源、策略等填写无误后,单击完成。步骤六:2分钟后无条件变更回退
说明:
无条件变更回退,目的在于能够及时发现安全组变更中是否存在对周边业务的短暂影响,以便及时做出应对决策,降低业务影响程度。
1. 修改完原安全组规则后,等待约2分钟,进行无条件回退,即删除 步骤五 中对安全组的修改。
2. 观察相关业务是否均持续正常,至少观测30分钟。
如所有业务均正常,则执行下一步。
如有部分业务反馈异常,建议立即终止本次变更,待问题回溯并评估业务影响后,再重新发起变更。
说明:
本例中业务观测30分钟后,业务均正常。
步骤七:再次修改原安全组
1. 再次执行 步骤五 的操作,即单击原安全组 ID,本例中为 VPC A 中 web1 和 web2 绑定的安全组 ID,进入安全组规则详情页。
2. 在入站规则页签,单击添加规则。
3. 在弹出的添加入站规则对话框中,添加攻击方来源 IP(例如
172.21.10.13和172.21.10.17)的“拒绝”策略,请确保规则中来源、策略等填写无误后,单击完成。4. 观察相关业务是否均持续正常,至少观测30分钟。
如所有业务均正常,则变更成功,结束。
如有部分业务反馈异常,建议立即终止本次变更,待问题回溯并评估业务影响后,再重新发起变更。
说明:
本例中业务运行正常,本次变更成功,结束。
文档反馈

