- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Access Key
- User Groups
- Role
- Policies
- Troubleshooting
- Permissions Boundary
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Natural Language Processing
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Best Practice
- Security Best Practice
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to COS Resources under the Account
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Read-only Access to VPCs
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- User APIs
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSafeAuthFlagColl
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Role APIs
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- GetRole
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Data Types
- Error Codes
- FAQs
- Glossary
- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Access Key
- User Groups
- Role
- Policies
- Troubleshooting
- Permissions Boundary
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Natural Language Processing
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Best Practice
- Security Best Practice
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to COS Resources under the Account
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Read-only Access to VPCs
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- User APIs
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSafeAuthFlagColl
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Role APIs
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- GetRole
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Data Types
- Error Codes
- FAQs
- Glossary
Overview
As the SP, Tencent Cloud needs to configure the OIDC for the IdP to establish a trust relationship with the enterprise IdP. This enables users from the enterprise IdP to log in to Tencent Cloud via user-based SSO.
This document uses Azure Active Directory as an example of IdP.
Note
View the OIDC protocol configuration information, (Copy the link at Azure Active Directory > App Registration > Endpoints > OpenID Connect Metadata Document, and open it in browser for specific configuration details)
Directions
1. Log in to the Tencent Cloud account Cloud Access Management Console.
2. In the navigation pane on the left, click Identity Providers > User-Based SSO.
3. On the User-Based SSO Management page, you can view the current User-Based SSO status and configuration information.
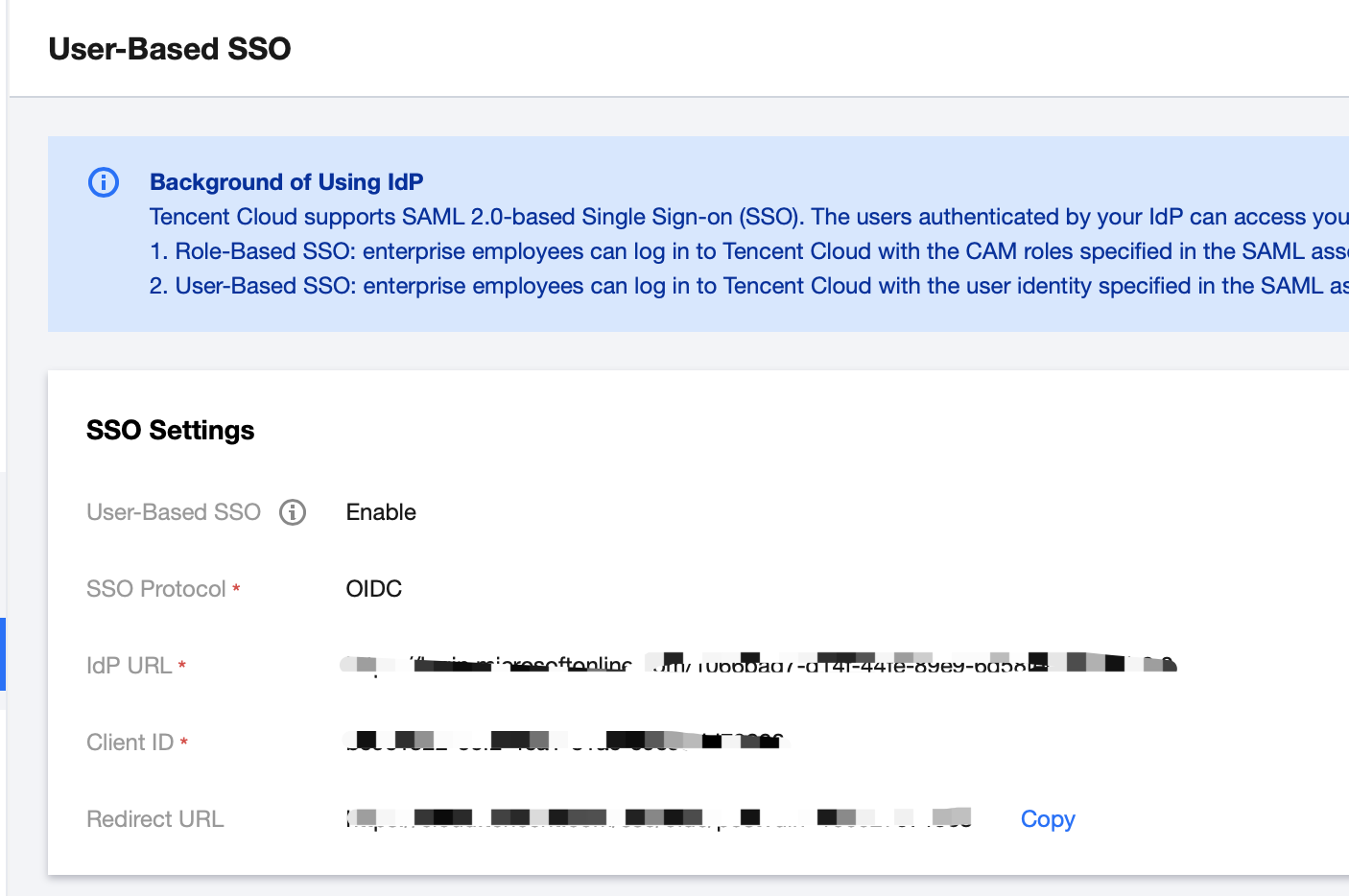

4. By clicking on the switch button following User-Based SSO, you can either enable or disable it.
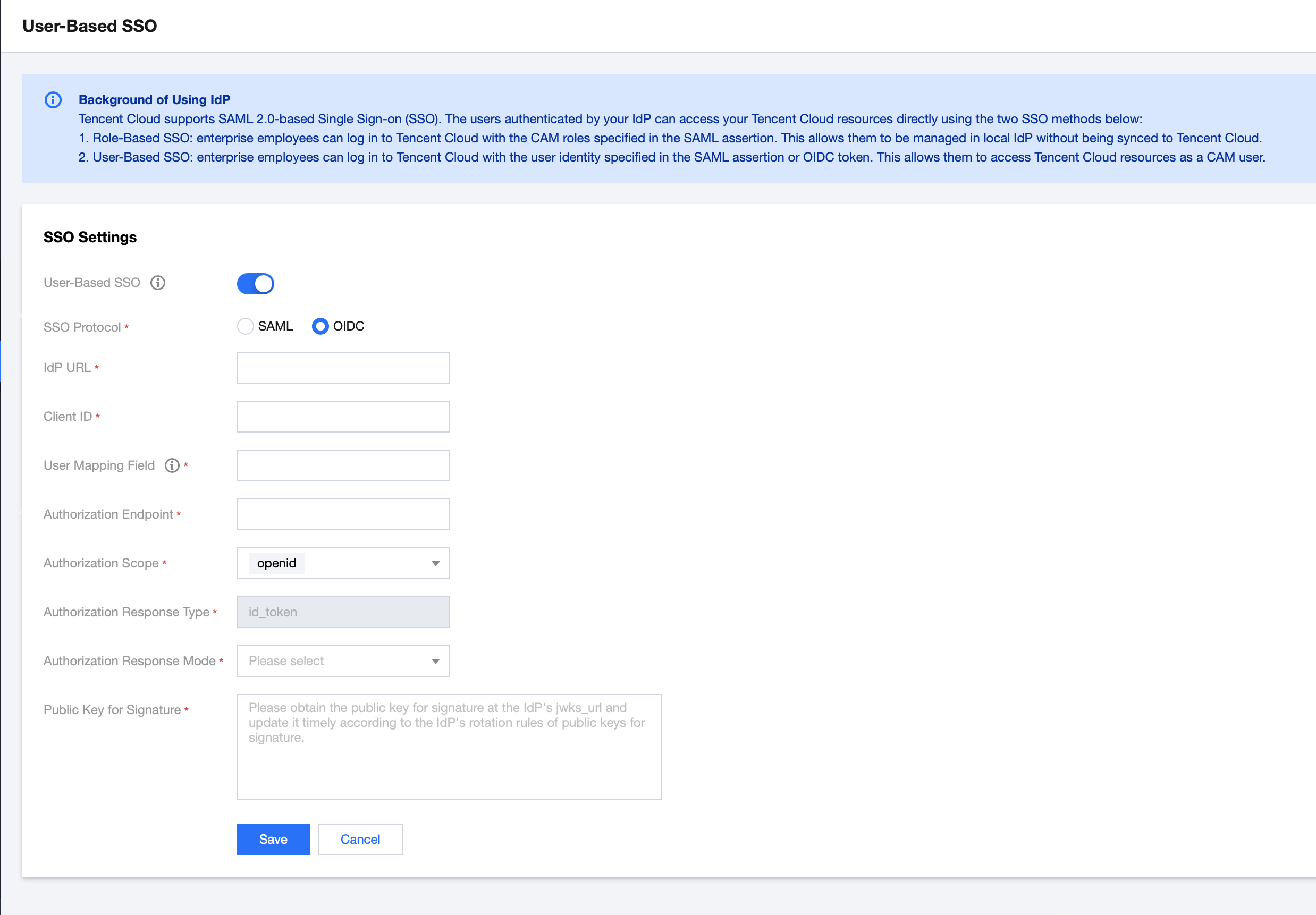

When user-based SSO is enabled: CAM sub-users cannot log in to Tencent Cloud via account ID and password. All CAM sub-users will be redirected to the IdP user login page for identity verification.
When user-based SSO is disabled: CAM users can login to Tencent Cloud via account ID and password, and the user-based SSO settings will not take effect.
SSO Protocol: Select the OIDC type.
IdP URL: Identifier of OpenID Connect IdP. Corresponds to the 'issuer' field value in the OpenID Connect metadata document provided by the IdP.
Client ID: Client ID registered with the OpenID Connect IdP. It can be obtained from the Azure Active Directory > Enterprise Applications > OIDCSSO Application Overview page.
User Mapping Field: The field maps the CAM sub-user name in the OpenID Connect IdP. Optional values in the "claims_supported" provided in the OpenID Connect metadata document obtained from the IdP. In this example, the name field is used to map the CAM's username.
Authorization Request Endpoint: The address of the authorization request of the OpenID Connect IdP. Corresponds to the "authorization_endpoint" field value in the OpenID Connect metadata document provided by the IdP.
Authorization Request Scope: The range of information for the authorization request by the OpenID Connect IdP. By default, 'openid' is mandatory.
Authorization Request Response Type: The type of parameters returned by the authorization request from OpenID Connect IdP. By default, 'id_token' is mandatory.
Authorization Request Response Mode: The response mode of the authorization request by OpenID Connect IdP. 'form_post' and 'fragment' modes are optional, and 'form_post' is recommended.
Signature Public Key: The public key for verifying the signature of the OpenID Connect IdP ID Token. Corresponds to the content (obtained by visiting the link) linked in the "jwks_uri" field in the OpenID Connect metadata document provided by the IdP. For the security of your account, we recommend you to routinely rotate the signing public key.
5. Click Save.

 Yes
Yes
 No
No
Was this page helpful?