- Tutorial
- Release Notes and Announcements
- Release Notes
- Public Image Release Notes
- Announcements
- Updating Some Image Pip Package Management Tools for CentOS 7
- CentOS 8 End of Maintenance
- Discontinuation of Support for SUSE Commercial Images
- Price Reduction in Selected Availability Zones
- OrcaTerm Proxy IP Addresses Updates
- Pay-as-you-go Price Adjustments for Standard S3 CVMs in the Silicon Valley Region
- Vulnerability repairing for Linux images
- Stopping supporting for Ubuntu 10.04 images
- Solution to Tomcat Start Failure on Ubuntu14.04
- Upgrading Virtio network card drive for Windows CVMs
- About Configuration of Security Group Port 53
- Windows Server 2003 System Images End of Support Announcement
- End of Support for Windows Server 2008 R2 Enterprise Edition SP1 64-bit System Images
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Operation Guide Overview
- Use Limits
- Convenience Features
- Instances
- Creating Instances
- Managing Instance Launch Template
- Batch Sequential Naming or Pattern String-Based Naming
- Logging In to Linux Instances
- Logging in to Windows instance
- Adjusting Configuration
- View Instance Details
- Renaming Instances
- Resetting Instance Password
- Managing Instance IPs
- Changing Instance Subnet
- Changing Security Group
- Conversion from Pay-As-You-Go to Monthly Subscription
- Searching for Instances
- Exporting Instance List
- Renewing Instances
- Starting Up Instances
- Shutting Down Instances
- Restarting Instances
- Reinstalling System
- Using Tencent Cloud Automation Tools to execute commands
- Terminating/Returning Instances
- Enabling Instance Termination Protection
- Instance Repossession or Recovering
- Spot Instances
- Querying the Repossession Status of a Spot Instance
- No Charges When Shut Down for Pay-as-You-Go Instances
- Managing Roles
- Enabling and Disabling Hyper-Threading
- Reserved Instances
- Images
- Migrating Servers
- Maintenance Tasks
- Cloud Disks
- Networking
- Security
- Security Groups
- Protection of Sensitive Operations
- Managing Login Password
- Managing SSH Keys
- Spread Placement Group
- Unblocking Port 25
- Tags
- Monitoring and Alarms
- Sample Console Configuration
- Best Practice
- Best Practices
- Choosing the CVM Model
- Setting up a Website
- Building an Environment
- Building a Website
- Building an Application
- Building a Visual GUI
- Data Backup
- Uploading Local Files to CVM
- Copying Local Files to CVMs
- Uploading Files from Windows to a Windows CVM via MSTSC
- Uploading Files from MacOS to Windows CVM Using MRD
- Uploading Files from Linux to Windows CVM using RDP
- Uploading files via WinSCP to a Linux CVM from Windows
- Uploading Files from Linux or MacOS to Linux CVM via SCP
- Uploading Files from Linux to a CVM Using FTP
- Uploading Files from Windows to a CVM Using FTP
- Other CVM Operations
- CVM Access to COS via a Private Network
- Best Practices for Boot Mode Legacy BIOS and UEFI
- Recovering Data on Linux CVMs
- Managing Disk Space on Windows CVMs
- Changing Kernel of a Linux Instance Manually
- Setting Up Windows-based AD Domain on a CVM
- Network Performance Test
- High-throughput Network Performance Test
- Using USB/IP to Share USB Devices in Linux
- Using RemoteFx to Redirect USB Devices in Windows
- Using AVX-512 Instructions to Accelerate AI Applications on CVM
- Building Tencent SGX Confidential Computing Environment
- Configuring Persistent Memory in M6p Instances
- Calling Cloud APIs via Python to Share Custom Images in Batches
- Operations Guide
- Initializing Data Disks
- Environment Configurations
- Installing Software
- User Data
- Work with Operating Systems
- System Activation
- System Updates
- System Shutdown
- Configuring High-performance Power Management
- Windows Recovery Mode
- Updating the Virtio ENI Driver
- Modifying SID
- Modifying VNC Resolution
- Ensuring Unique SIDs for CVMs Using Sysprep
- Use of the atop Monitoring Tools by Linux Instances
- Introduction to Linux Kernel Parameters
- Others
- Troubleshooting
- Instance-Related Failures
- CVM Login Failures
- Windows Instance Login Failures
- Windows Instance Login Failures
- An authentication error occurred when you tried to log in to a Windows instance remotely
- Failed to Reset the CVM Password or the CVM Password Is Invalid
- Connection to a Windows CVM through Remote Desktop was denied
- Requires network-level identity verification
- Problems occurred when you tried to log in to a Windows CVM remotely on Mac
- Failed to log in to a Windows CVM due to high CPU and memory usage
- Failed to connect to a remote computer through Remote Desktop
- Credentials Not Work
- Windows instance: no remote Desktop license server can provide license
- Remote Login Failure Due To Port Issues
- Linux Instance Login Failures
- Linux Instance Login Failures
- Unable to Log in to a Linux Instance via SSH Key
- Failing to log in to a Linux CVM due to high CPU and memory usage
- Remote Login Failure due to Port Issues
- VNC Login Error (Module is Unknown)
- VNC Login Error (Account Locked due to XXX Failed Logins)
- VNC Login Error (Login Failed with Correct Password)
- VNC or SSH Login Error (Permission Denied)
- Login Failure Due to /etc/fstab Configuration Errors
- sshd Configuration File Permissions
- Infinite Loop Call in /etc/profile
- Login Failure Due to Server Isolation
- Login Failure Due to High Bandwidth Occupation
- Remote Connect Failure Due to Security Group Settings
- Troubleshooting Linux Instance Issues via VNC and Rescue Mode
- Failed to shut down or restart a CVM
- Network Namespace Creation Failure
- Kernel and IO Issues
- Missing System bin or lib Soft Link
- Suspected Infection with Virus
- "no space left on device" Error During File Creation
- Linux CVM Memory Issues
- Network Related Failures
- Instance-Related Failures
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Region APIs
- Instance APIs
- DescribeInstances
- DescribeInstanceFamilyConfigs
- DescribeZoneInstanceConfigInfos
- DescribeInstanceTypeConfigs
- DescribeInstancesOperationLimit
- DescribeInstanceVncUrl
- InquiryPriceRunInstances
- InquiryPriceResetInstance
- InquiryPriceResetInstancesType
- InquiryPriceResizeInstanceDisks
- RunInstances
- StartInstances
- RebootInstances
- StopInstances
- ResetInstance
- TerminateInstances
- ResetInstancesType
- ResizeInstanceDisks
- ResetInstancesPassword
- ModifyInstancesAttribute
- ModifyInstancesProject
- InquirePricePurchaseReservedInstancesOffering
- DescribeReservedInstancesConfigInfos
- DescribeInstancesStatus
- PurchaseReservedInstancesOffering
- Cloud Hosting Cluster APIs
- Placement Group APIs
- Image APIs
- Key APIs
- Security Group APIs
- Network APIs
- Instance Launch Template APIs
- Data Types
- Error Codes
- FAQs
- Related Agreement
- Glossary
- Tutorial
- Release Notes and Announcements
- Release Notes
- Public Image Release Notes
- Announcements
- Updating Some Image Pip Package Management Tools for CentOS 7
- CentOS 8 End of Maintenance
- Discontinuation of Support for SUSE Commercial Images
- Price Reduction in Selected Availability Zones
- OrcaTerm Proxy IP Addresses Updates
- Pay-as-you-go Price Adjustments for Standard S3 CVMs in the Silicon Valley Region
- Vulnerability repairing for Linux images
- Stopping supporting for Ubuntu 10.04 images
- Solution to Tomcat Start Failure on Ubuntu14.04
- Upgrading Virtio network card drive for Windows CVMs
- About Configuration of Security Group Port 53
- Windows Server 2003 System Images End of Support Announcement
- End of Support for Windows Server 2008 R2 Enterprise Edition SP1 64-bit System Images
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Operation Guide Overview
- Use Limits
- Convenience Features
- Instances
- Creating Instances
- Managing Instance Launch Template
- Batch Sequential Naming or Pattern String-Based Naming
- Logging In to Linux Instances
- Logging in to Windows instance
- Adjusting Configuration
- View Instance Details
- Renaming Instances
- Resetting Instance Password
- Managing Instance IPs
- Changing Instance Subnet
- Changing Security Group
- Conversion from Pay-As-You-Go to Monthly Subscription
- Searching for Instances
- Exporting Instance List
- Renewing Instances
- Starting Up Instances
- Shutting Down Instances
- Restarting Instances
- Reinstalling System
- Using Tencent Cloud Automation Tools to execute commands
- Terminating/Returning Instances
- Enabling Instance Termination Protection
- Instance Repossession or Recovering
- Spot Instances
- Querying the Repossession Status of a Spot Instance
- No Charges When Shut Down for Pay-as-You-Go Instances
- Managing Roles
- Enabling and Disabling Hyper-Threading
- Reserved Instances
- Images
- Migrating Servers
- Maintenance Tasks
- Cloud Disks
- Networking
- Security
- Security Groups
- Protection of Sensitive Operations
- Managing Login Password
- Managing SSH Keys
- Spread Placement Group
- Unblocking Port 25
- Tags
- Monitoring and Alarms
- Sample Console Configuration
- Best Practice
- Best Practices
- Choosing the CVM Model
- Setting up a Website
- Building an Environment
- Building a Website
- Building an Application
- Building a Visual GUI
- Data Backup
- Uploading Local Files to CVM
- Copying Local Files to CVMs
- Uploading Files from Windows to a Windows CVM via MSTSC
- Uploading Files from MacOS to Windows CVM Using MRD
- Uploading Files from Linux to Windows CVM using RDP
- Uploading files via WinSCP to a Linux CVM from Windows
- Uploading Files from Linux or MacOS to Linux CVM via SCP
- Uploading Files from Linux to a CVM Using FTP
- Uploading Files from Windows to a CVM Using FTP
- Other CVM Operations
- CVM Access to COS via a Private Network
- Best Practices for Boot Mode Legacy BIOS and UEFI
- Recovering Data on Linux CVMs
- Managing Disk Space on Windows CVMs
- Changing Kernel of a Linux Instance Manually
- Setting Up Windows-based AD Domain on a CVM
- Network Performance Test
- High-throughput Network Performance Test
- Using USB/IP to Share USB Devices in Linux
- Using RemoteFx to Redirect USB Devices in Windows
- Using AVX-512 Instructions to Accelerate AI Applications on CVM
- Building Tencent SGX Confidential Computing Environment
- Configuring Persistent Memory in M6p Instances
- Calling Cloud APIs via Python to Share Custom Images in Batches
- Operations Guide
- Initializing Data Disks
- Environment Configurations
- Installing Software
- User Data
- Work with Operating Systems
- System Activation
- System Updates
- System Shutdown
- Configuring High-performance Power Management
- Windows Recovery Mode
- Updating the Virtio ENI Driver
- Modifying SID
- Modifying VNC Resolution
- Ensuring Unique SIDs for CVMs Using Sysprep
- Use of the atop Monitoring Tools by Linux Instances
- Introduction to Linux Kernel Parameters
- Others
- Troubleshooting
- Instance-Related Failures
- CVM Login Failures
- Windows Instance Login Failures
- Windows Instance Login Failures
- An authentication error occurred when you tried to log in to a Windows instance remotely
- Failed to Reset the CVM Password or the CVM Password Is Invalid
- Connection to a Windows CVM through Remote Desktop was denied
- Requires network-level identity verification
- Problems occurred when you tried to log in to a Windows CVM remotely on Mac
- Failed to log in to a Windows CVM due to high CPU and memory usage
- Failed to connect to a remote computer through Remote Desktop
- Credentials Not Work
- Windows instance: no remote Desktop license server can provide license
- Remote Login Failure Due To Port Issues
- Linux Instance Login Failures
- Linux Instance Login Failures
- Unable to Log in to a Linux Instance via SSH Key
- Failing to log in to a Linux CVM due to high CPU and memory usage
- Remote Login Failure due to Port Issues
- VNC Login Error (Module is Unknown)
- VNC Login Error (Account Locked due to XXX Failed Logins)
- VNC Login Error (Login Failed with Correct Password)
- VNC or SSH Login Error (Permission Denied)
- Login Failure Due to /etc/fstab Configuration Errors
- sshd Configuration File Permissions
- Infinite Loop Call in /etc/profile
- Login Failure Due to Server Isolation
- Login Failure Due to High Bandwidth Occupation
- Remote Connect Failure Due to Security Group Settings
- Troubleshooting Linux Instance Issues via VNC and Rescue Mode
- Failed to shut down or restart a CVM
- Network Namespace Creation Failure
- Kernel and IO Issues
- Missing System bin or lib Soft Link
- Suspected Infection with Virus
- "no space left on device" Error During File Creation
- Linux CVM Memory Issues
- Network Related Failures
- Instance-Related Failures
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Region APIs
- Instance APIs
- DescribeInstances
- DescribeInstanceFamilyConfigs
- DescribeZoneInstanceConfigInfos
- DescribeInstanceTypeConfigs
- DescribeInstancesOperationLimit
- DescribeInstanceVncUrl
- InquiryPriceRunInstances
- InquiryPriceResetInstance
- InquiryPriceResetInstancesType
- InquiryPriceResizeInstanceDisks
- RunInstances
- StartInstances
- RebootInstances
- StopInstances
- ResetInstance
- TerminateInstances
- ResetInstancesType
- ResizeInstanceDisks
- ResetInstancesPassword
- ModifyInstancesAttribute
- ModifyInstancesProject
- InquirePricePurchaseReservedInstancesOffering
- DescribeReservedInstancesConfigInfos
- DescribeInstancesStatus
- PurchaseReservedInstancesOffering
- Cloud Hosting Cluster APIs
- Placement Group APIs
- Image APIs
- Key APIs
- Security Group APIs
- Network APIs
- Instance Launch Template APIs
- Data Types
- Error Codes
- FAQs
- Related Agreement
- Glossary
An authentication error occurred when you tried to log in to a Windows instance remotely
Last updated: 2024-01-06 17:32:18
Problem Description
When a Remote Desktop Connection is used to log in to a Windows instance, an error is displayed.
An authentication error has occurred. The token supplied to the function is invalid.
An authentication error has occurred. The function requested is not supported.
Problem Analysis
Microsoft published a security update in March 2018. By correcting how the Credential Security Support Provider protocol (CredSSP) validates requests during authentication, this update fixes the remote code execution vulnerability in the CredSSP. Both the client and server need to install the security update, or the preceding error may occur.
Remote connection fails in the following three scenarios:
Scenario 1: The security update is installed on the server but not on the client, and the "force updated clients" policy is configured.
Scenario 2: The security update is installed on the client but not on the server, and the "force updated clients" policy is configured.
Scenario 3: The security update is installed on the client but not on the server, and the "mitigated" policy is configured.
Solution
Note:
Logging in to CVM via VNC
1. Log in to the CVM console.
2. On the Instances page, find the target CVM instance and click Log in.
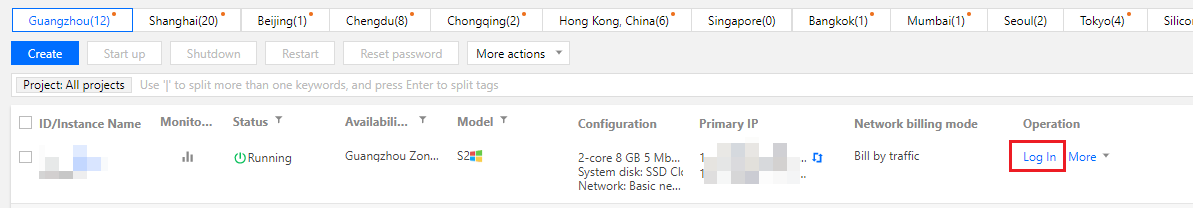

3. In the Standard Login | Windows Instance pop-up window, select Login via VNC.
4. In the login pop-up window, select Send remote command in the top-left corner and press Ctrl-Alt-Delete to open the system login window as shown below:
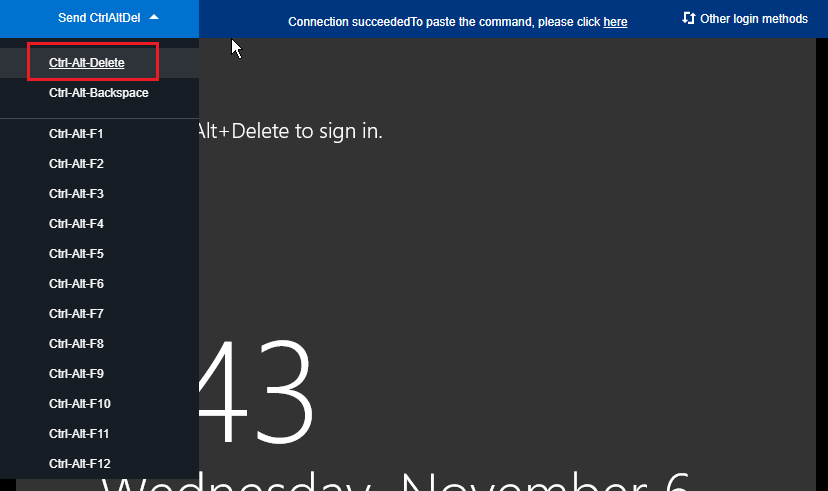

5. Enter the login password and press Enter to log in to the Windows CVM instance.
Solution 1. Install the security update (recommended)
Install the security update on the unpatched client or server. For updates for different operating systems, see CVE-2018-0886 | CredSSP remote code execution vulnerability. This solution uses Windows Server 2016 as an example.
In other operating systems, you may use the following methods to enter Windows Update:
Windows Server 2012: 

Windows Server 2008: Start > Control Panel > System and Security > Windows Update
Windows 10: 

Windows 7: 

1. On the desktop, click 

2. In the Settings pop-up window, select Update & Security.
3. In Update & Security, select Windows Update and click Check for updates.
4. Click Start Installation.
5. After the installation is complete, restart the instance to finish the update.
Solution 2. Modify the policy
In a CVM instance that has the security update installed, set the Encryption Oracle Remediation policy to Vulnerable. This solution uses Windows Server 2016 as an example. Follow the steps below:
Note:
If no group policy editor is available in the Windows 10 Home operating system, you can modify the registry to edit the policy as instructed in Solution 3. Modify the registry.
1. On the desktop, click 

Note:
You can also press Win+R to open the Run window.
2. On the left sidebar, select Computer Configuration > Administrative Templates > System > Credentials Delegation and double-click Encryption Oracle Remediation.
3. In the Encryption Oracle Remediation pop-up window, select Enabled and set Protection level to Vulnerable.
4. Click OK.
Solution 3. Modify the registry
1. On the desktop, click 

Note:
You can also press Win+R to open the Run window.
2. On the left sidebar, select Computer > HKEY_LOCAL_MACHINE > SOFTWARE > Microsoft > Windows > CurrentVersion > Policies > System > CredSSP > Parameters.
Note:
If the directory path does not exist, create one manually.
3. Right-click Parameters, select New > DWORD (32-bit) value, and name the file AllowEncryptionOracle.
4. Double-click the newly created "AllowEncryptionOracle" file, set Value data to "2", and click OK.
5. Restart the instance.

 Yes
Yes
 No
No
Was this page helpful?